In-depth understanding of DNS tunnel communication in practical scenarios

In-depth understanding of DNS tunnel communication in practical scenarios
words written in front
Recently, we conducted an in-depth analysis of the use and usage of Domain Name System DNS tunneling technology in the wild. Attackers can use DNS tunneling technology to bypass various security policies in an organization's network environment, because most organizations have relatively loose management policies for DNS traffic. Previous research has also shown that malware campaigns such as SUNBURST and OilRig utilize DNS tunneling technology to achieve remote command and control (C2).
However, we still don’t know many details about how attackers use DNS tunneling technology in the wild. For example, are they using DNS tunneling just for C2? How do they implement and host these technologies? Can we monitor malicious activity by capturing and monitoring DNS tunnel traffic?
In this article, we will conduct a detailed analysis and introduction to the multiple aspects of DNS tunnel communication technology used by attackers in the wild.
DNS tunnel basics
What is a DNS tunnel
DNS tunneling is a technology that encodes data for non-DNS programs and protocols in DNS queries and responses. This allows various types of communication traffic to be forwarded through the DNS protocol, including file transfers, C2, and web traffic. wait.
Why perform DNS tunneling
DNS typically uses UDP port 53, which is typically open on clients, systems, servers, and firewalls to support the transmission of DNS queries. DNS is a basic component of the Internet. It provides services for many applications, from web browsing and email services to host automatic discovery, load balancing, security review and monitoring services, etc., all of which require the use of DNS.
Due to its criticality, most organizations have relatively loose security management policies for DNS traffic, which has led many attackers to choose to utilize the DNS protocol to tunnel C2 communication traffic and retrieve malware payloads.
Many malware campaigns, such as SUNBURST, OilRig, xHunt and DarkHydrus, use DNS tunneling technology. The permission policy for DNS traffic allows attackers to access the Internet, and a large amount of benign DNS traffic becomes a natural disguise for attackers to hide their footprints.
How to perform DNS tunneling
Two main components are required to perform DNS tunneling: client and server. The client sends DNS packets to the Internet, encodes the content via a DNS query, and decodes the content from the DNS response. The server receives a DNS query from a recursive resolver, decodes the content from the DNS query, and encodes the content into a DNS response.
The following figure shows the execution process of DNS tunnel:
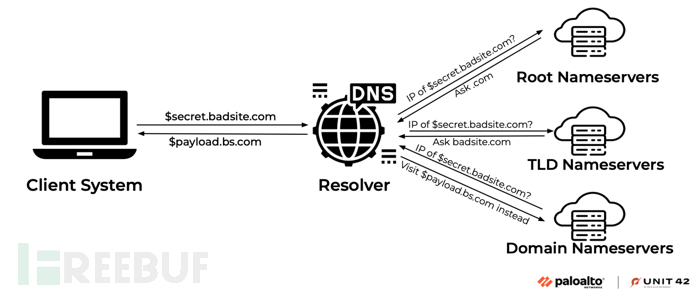
In the above diagram, the client will first encode the sensitive data value into the subdomain $secret and send it as a DNS query request to $secret.badsite[.]com. Next, the resolver iteratively queries name servers at different domain levels until it gets a valid response. Similarly, the server component (name server) can also encode the malicious payload into the subdomain $payload and send a DNS response (CNAME $payload.bs[.]com) to $secret.badsite[.]com.
Instead of sending the raw data, we typically encode and segment the data using an encoding algorithm. Virtually anyone can come up with an algorithm to fragment data.
There are also many ready-made open source DNS tunneling tools, such as iodine, DNSStager, dnscat2, sliver, and Cobalt Strike . These tools support encoding of generic messages into subdomains of DNS queries and various types of DNS responses such as A (IPv4 address), AAAA (IPv6 address), TXT, CNAME, and MX.
Applying DNS tunneling technology to C2
C2 is the most common application scenario of DNS tunneling technology. The same activity can share some characteristics, such as using the domain name server used for communication as C2, or using common tunneling tools to implement encoding and decoding.
The first example targeted the malicious activities of an organization in the financial field. We observed communications between 22 tunnel domain names and the same target user.
These domains shared 7 nameserver IPs and used the same underlying coding tools. The attackers even applied for seemingly identical security/cloud provider domain names in an attempt to evade detection.
These domain names include:
panos[.]ltd
ciscocloud[.]space
ubrella[.]online
msft[.]center
mscd[.]store
awsl[.]site
We've listed these domains with their sample queries, nameserver domains, and nameserver IPs in the table below:
domain name | Query sample | domain name server | Domain name server IP |
panos[.]ltd | 10.eff89fcf44a13186ad3765f35860ce19c722c4bcda6bbbae6b7bab6025b36d0.d036b5a3fd8b67e55ee35feff7d014fdb8d32afe93d5d6f05f1dda3a096e8fa.2e10d 53e935549b3a081982724c3e6f806.oak.panos[.]ltd | bur.panos[.]ltd | 34.92.43[.]140 |
ciscocloud[.]space | 10.a6674ae5d37cab7263074adef14925ef28698896b8491276097a470beca325a.669f12d4b31e9a6707ce2ee5b595cb723f40ea6d8e5f406b8fba874c8bec632.32 99de58f43c3e4be80a7d7db2a2ed5aee9e13bac9cb.habit.ciscocloud[.]space | bram.ciscocloud[.]space | 34.92.43[.]140 |
ubrella[.]online | 8.d4fee8aa63e4ee6435452f86e84464168e96e314eb1a19c45e0e76f3ca71b2a.e9476062765ba0aeaeea97333805f09470ff3bd103e3ce8bd3ffefa3dfea90f.369c d352a204e9662db180407f1d1b8fa87be97c81d1.feign.ubrella[.]online | rumor.ubrella[.]online | 34.92.43[.]140 |
mscd[.]store | 4.a6gpmbnqbjewgwnqnlivwhleux4vnnyiuduyqgjkyn9jcihsttpdbdenf7lx8jx.jqhdulrejthsyipzvoleyvhv5s99nydtj5um8bzdmdms9gwdqnq46yis5hvbryo.dernuvjw7a6p6ndq4c8lwomsl7 zq5lncgsutndxfpaufefhr7xxeuhfpk8hs.sny7htmpdpqdcumtgrmeptytbe9p78skry64.17328.fish.mscd[.]store | rug.mscd[.]store | 35.194.255[.]111 |
awsl[.]site | 1.758fcd0ac2301084ef82efb047050ff5e7d45b4cd636b46e4292b67acac5ab0.a1644dfde400b8d41e7b6ec37338c45d34a8e9ed81173e8dffdf57ebb3c9e30.9fc 12877d608dfca610d50a121acbd30b2450391c13a.mud.awsl[.]site | lkas.awsl[.]site | 35.194.255[.]111 |
msft[.]center | 10.c5f310abb43603a3af324ee92bea16c8132ec2909fbca8d1036fe409d33af9b.c8c30e936bffb9f93bcba2c27682dcca1ab79aced6d1cf015a11d56a9c2f9f5.c49d8 757a19b693d78d1772977cbf164e2748b57bb9f.ud.msft[.]center | 08e099da.msft[.]center | 34.81.65[.]4 |
Our second example is an activity targeting another financial industry client. We found that the three tunnel domain names all pointed to the same client and used the same underlying tunneling tool - Cobalt Strike. The representative characteristics of Cobalt Strike include the use of common Prefixes, such as www, post, api, etc.
The three domain names are identity-mgmt[.]com, internalsupport[.]info and cloud-enrollment[.]com. The following are the corresponding query samples, domain name servers and IP addresses:
domain name | Query sample | domain name server | Domain name server IP |
cloud-enrollment[.]com | api.12abc2cb5.446f35fa.dns.cloud-enrollment[.]com | ns1.cloud-enrollment[.]com | 3.238.113[.]212 |
identity-mgmt[.]com | intact.md.180.02d8f18d2.7e8986be.int.identity-mgmt[.]com | ns1.cloud-enrollment[.]com | 3.238.113[.]212 |
internalsupport[.]info | icr.0325e18d8.16ae9fb2.pl.internalsupport[.]info | dn.internalsupport[.]info | 3.238.244[.]129 |
Summarize
Now, more and more network gangs are applying DNS tunnel communication technology to various places, including C2 servers and VPN services. Therefore, as a security defense personnel, it is very important to understand the utilization of DNS tunnel technology in the wild. Only by understanding the underlying tools and related activities of DNS tunnel communication can we achieve fine-grained analysis and achieve rapid response to security incidents. .
Indicators of Intrusion Threat IoC
domain name
panos[.]ltd
ciscocloud[.]space
ubrella[.]online
mscd[.]store
awsl[.]site
msft[.]center
cloud-enrollment[.]com
identity-mgmt[.]com
internalsupport[.]info
claudfront[.]net
allowedlisted[.]net
hsdps[.]cc
rcsmf100[.]net
hammercdntech[.]com
IP address
34.92.43[.]140
35.194.255[.]111
34.81.65[.]4
3.238.113[.]212
3.238.244[.]129
5.252.176[.]63
83.166.240[.]52
5.252.176[.]22
194.31.55[.]85
65.20.73[.]176
Other references
https://unit42.paloaltonetworks.com/tag/dns-tunneling/
https://unit42.paloaltonetworks.com/solarstorm-supply-chain-attack-timeline/
https://unit42.paloaltonetworks.com/dns-tunneling-how-dns-can-be-abused-by-malicious-actors/
https://www.bamsoftware.com/software/dnstt/
https://unit42.paloaltonetworks.com/dns-tunneling-in-the-wild-overview-of-oilrigs-dns-tunneling/
https://unit42.paloaltonetworks.com/oilrig-novel-c2-channel-steganography/
Reference sources
https://unit42.paloaltonetworks.com/dns-tunneling-in-the-wild/
Author of this article: FreddyLu666, please indicate the source of reprint from FreeBuf.COM