When will the API chaos stop? Ruixu Information strikes hard to fight "stubborn diseases"

In the era of "APIs for everything", quickly building products and services through APIs and responding to customer needs are essential skills for digital enterprises. But at the same time, APIs carry more and more complex application logic and more and more sensitive data characteristics, which also makes APIs a key attack target of hackers.
In recent years, many well-known international companies have suffered a huge blow due to the negligence of API security. Not only that, but malicious API traffic has increased by 681% over the past 12 months, with 95% of organizations experiencing API security incidents, according to the Q1 2022 State of API Security Report by research arm Salt Labs. However, most organizations are not ready to meet these challenges, with more than one-third (34%) of enterprises having no API security strategy.
API five security risks, have you been recruited?
In 2021, my country's "Data Security Law" will be officially implemented, data security will enter the track of the rule of law, and API security will also enter a new stage of legal construction. From the perspective of the technical requirements for data transmission, provision and disclosure of the "Data Security Law", API applications in domestic government and enterprise institutions mainly face five major management challenges and security risks:
Risk 1: API assets cannot be effectively managed
Because the number of APIs is growing so fast, many companies don't know how many APIs they have and what state they are in. API interfaces cannot be scanned and probed. How to sort out a large number of API interfaces? If API assets are unclear, how should security responsibilities be divided and implemented? How to solve the life cycle management of API assets?
Ruixu solution: In response to the challenges of API asset management, Ruixu API security management and control platform (API BotDefender) can continuously discover API interfaces, establish an API list, and compare it with the API list provided by the business side, so as to discover unknown APIs and APIs in a timely manner. Zombie API. At the same time, API interfaces are classified, grouped, and responsible persons are assigned to realize data decentralization management; API interface styles are extracted to provide visual display for API interfaces.
Risk 2: API security attack risk
Insecure APIs continue to expand the application attack surface, making it easier for hackers to conduct reconnaissance, gather configuration information, and plan cyberattacks. When APIs face various security attacks, how can enterprises effectively identify and protect them? For example: Are API request parameters compliant? Is the API interface calling sequence compliant?
Ruixu solution: In the face of diversified API attacks, Ruixu API security management and control platform can define the API interface calling sequence based on known business logic and dependencies, prevent access behavior that bypasses business logic, and set interface request parameter calling rules in advance. Reject illegal API request parameter calls, reduce security configuration errors, and narrow the attack surface. At the same time, it supports API security attack detection and protection, and introduces semantic analysis technology to further improve detection accuracy.
Risk 3: Sensitive data management and control
Attacks against APIs have now become the first choice for malicious attackers, and more and more hackers use APIs to steal sensitive data and conduct business fraud. If an enterprise does not desensitize sensitive information and other data and transmit it without encryption, once the traffic is intercepted and cracked, it will have a serious impact on the rights and interests of enterprises and citizens. Therefore, enterprises need to have a deeper understanding of which APIs carry what type of sensitive information; how to identify sensitive data in API access; how to implement control over sensitive data in APIs; how to respond to compliance audit requirements, etc.
Ruishu solution: In order to better manage sensitive data and meet compliance audit requirements, Ruishu API security management and control platform has a built-in sensitive information detection engine, covering 18 types of sensitive data such as name, mobile phone number, ID card, bank card, and password. It can automatically classify sensitive information, gain real-time insight into sensitive data, plaintext passwords and weak passwords transmitted in two directions in the API interface, and desensitize the sensitive information in the returned messages of the API interface in a timely manner to avoid the risk of data leakage.
Risk 4: API Abnormal Access Risk
With the continuous upgrading of automated attack methods, even if enterprises have established mechanisms such as identity authentication, access authorization, and sensitive data protection, it is sometimes unavoidable that hackers use machines to simulate normal user behavior to carry out attacks. In the face of logging in with a legal identity, simulating normal operations, and multi-source and low-frequency API access requests, can enterprises detect whether the access behavior is abnormal? How to manage API access behavior, and how to identify business risks from API access? How to manage and control abnormal access?
Ruixu Solution: Logging in with a legal identity, simulating normal operations, and multi-source and low-frequency API access requests are important reasons why API attacks are difficult to detect. In this regard, the Ruixu API security management and control platform monitors the access behavior of API interfaces in real time based on multi-dimensional real-time monitoring, including access success rate, time-consuming, TPS, concurrency, attack events and other dimensions, establishes API access baselines, and can detect abnormalities that deviate from the baseline in time. access behavior. At the same time, the built-in API business threat model can see the common business threats of API, such as: credential stuffing, crawlers, etc., and perform human-machine identification efficiently and accurately.
Risk five: real-time security protection
Faced with unknown and diverse API attacks, enterprises need to enable real-time security protection and proactively discover and respond to API security threats in order to truly build a security line of defense for the business, for example: whether real-time fine-grained block and fuse various types of attacks risk? Can the protection be achieved without affecting the business?
Ruixu solution: Based on the needs of enterprises for real-time security response and business development, Ruixu API BotDefender has built-in flexible API access control policies, which can be based on API interface, API grouping, API management responsible person, source IP, access frequency, client fingerprint , API token, User Agent, HTTP request features and other hundreds of elements, implement refined access control to API interface, support multi-dimensional frequency limiting, interception, delay, etc., to achieve a balance between security and business.
At present, most enterprises mainly rely on traditional security mechanisms such as identity authentication, permission control, and request content verification in response to API security. Address various emerging threats to APIs in existing business models.
Compared with traditional security products, API BotDefender is the first in the industry to put forward the methodology of "ADMP security model", which realizes API data transmission, Provided and open security governance to systematically ensure API security. This makes up for the shortcomings of various products and has several core advantages:
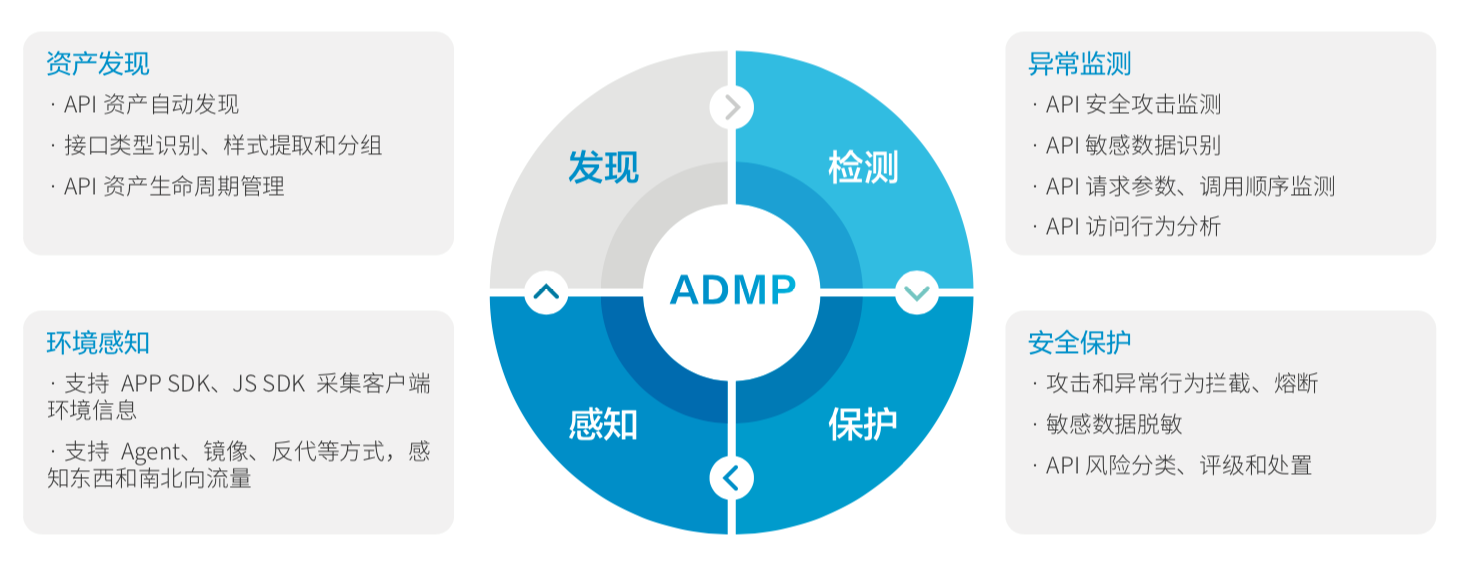
Automate API Asset Management
Traditional API gateways mainly implement authentication and authentication, and lack the discovery and control of API security.
The Ruixu API security management and control platform can quickly and automatically discover API assets, and can realize high-precision identification and style extraction of API interfaces, and give a clear identification of the discovered APIs; The access status of the API is clear at a glance, helping users realize the life cycle management of API assets.
API multi-dimensional attack protection
Traditional WAF is based on a rule base and can only block security attacks by adhering to the rules, but cannot see business threats in all directions.
Ruixu API security management and control platform adopts the whole-process security threat protection technology, and comprehensively detects and analyzes abnormal behaviors based on semantic analysis rules, and the false positive rate and false negative rate are significantly reduced; through traffic analysis and behavior analysis technology, accurately build API business threat model. It not only covers the attack defense of OWASP API Security Top 10, but also can quickly respond to various API business security threats such as crawlers and credential stuffing through the API business threat model.
Industry sensitive data management
The Ruishu API security management and control platform comes with a variety of sensitive data identification strategies by default, covering the identification of dozens of common sensitive data in the government, finance, operators, medical and other industries, and can also identify sensitive data according to the characteristics of industry users. Customize labelled data to help users quickly identify sensitive data.
Dynamic Response Protection
The Ruixu API security management and control platform can dynamically respond to the results or specified conditions of attacks and abnormal behaviors, and improve the difficulty of attack methods such as reverse detection or machine learning analysis.
high performance processing
The Ruishu API security management and control platform optimizes data processing from the process of collecting API data, deconstructing API packets, and contacting API contexts. times.