Besides security differences, what are the differences between HTTP and HTTPS?

Besides security differences, what are the differences between HTTP and HTTPS?
HTTP and HTTPS are two common network protocols used to transfer data between browsers and servers. However, there are some important differences between them, which relate to data security, transmission performance, usage cost and search ranking. This article will introduce the differences between HTTP and HTTPS from the following aspects. The outline of this article is as follows:
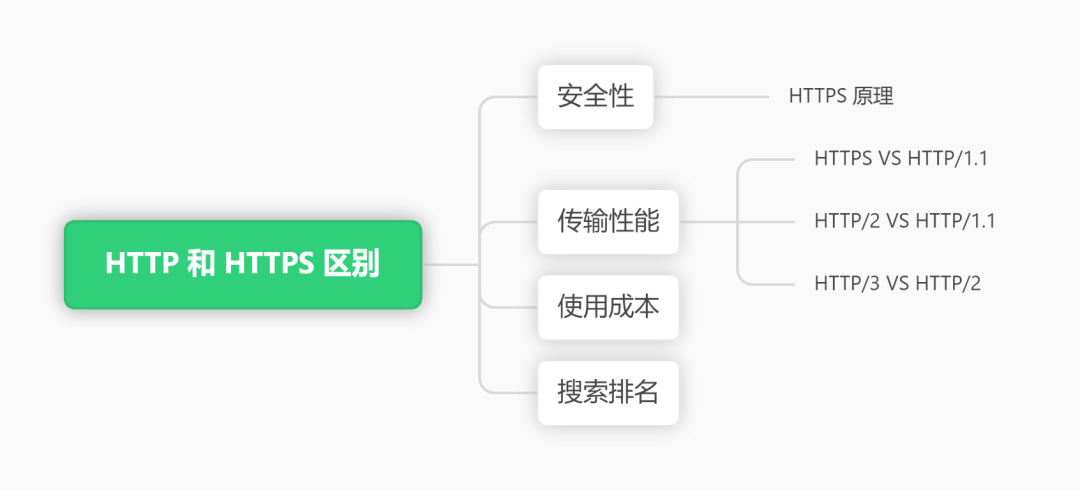 picture
picture
Data security
The HTTP protocol is a clear text transmission protocol that does not perform any encryption or verification of data. This means that anyone on the network can intercept, view or modify the data transmitted by HTTP . This poses a great security risk, especially for Some sensitive information, such as username, password, bank card number, ID number, etc.
The HTTPS protocol is a secure transmission protocol that adds an SSL/TLS layer to HTTP . SSL/TLS is an encryption and authentication technology that can encrypt, decrypt, sign and verify data, thus ensuring Data confidentiality, integrity and identity authenticity prevent data from being stolen or tampered with by third parties.
 picture
picture
Image source https://coolcao.com 2018/08/06/https/
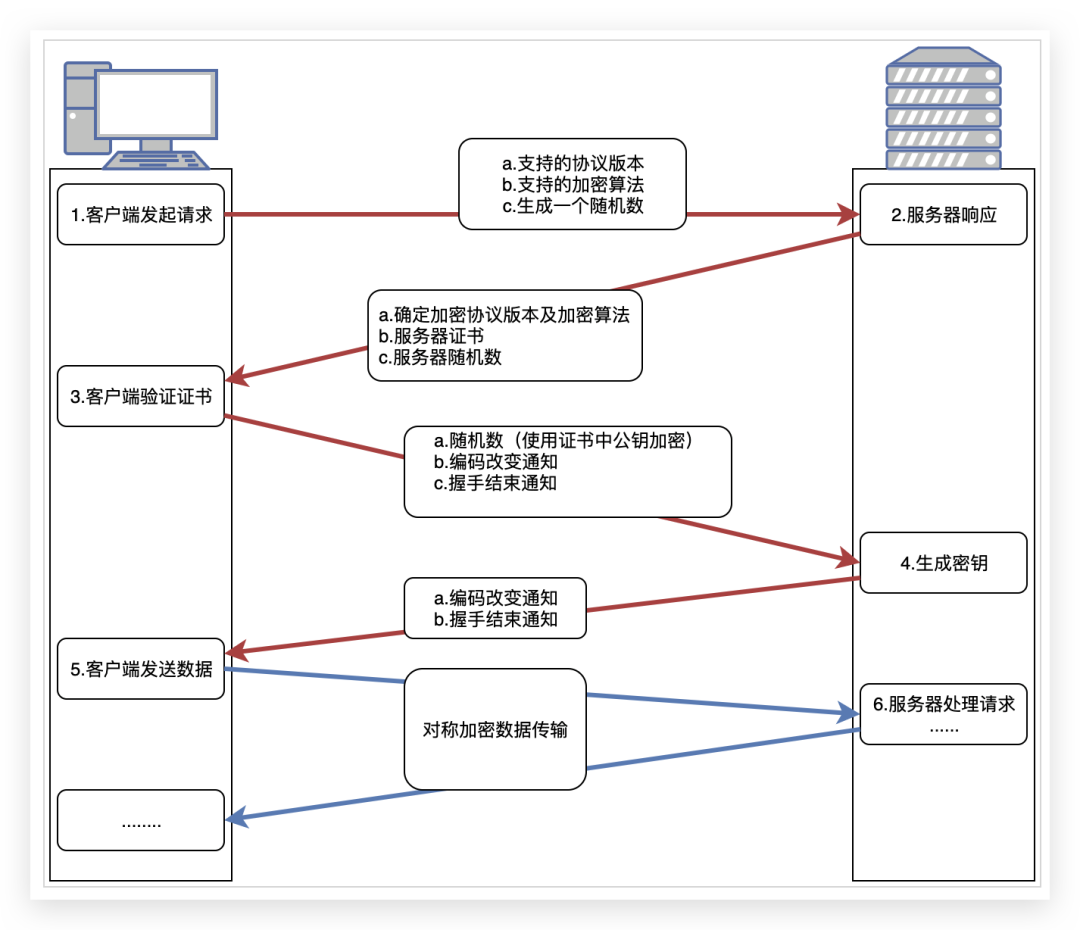
As shown in the figure above, the HTTPS process includes a handshake and subsequent data transmission. The purpose of the handshake is for the client and the server to negotiate encryption algorithms and other parameters.
The working principle of the HTTPS protocol is roughly as follows:
- The client requests the server for the first time, tells the server the protocol version it supports, the encryption algorithm and compression algorithm it supports, and generates a random number (client random) to inform the server.
Information that the client needs to provide:
- Supported protocol version, such as TSL1.0 version
- A random number generated by the client to later generate a symmetric key
- Supported encryption algorithms; supported compression methods, etc.
- The server confirms the encryption method used by both parties and returns the client certificate and a server random number (server random)
Information the server needs to provide:
- protocol version
- encryption algorithm
- Server generated random number
- Server certificate
- After receiving the certificate, the client first verifies the validity of the certificate, then generates a new random number (premaster secret), uses the public key in the digital certificate to encrypt the random number, and sends it to the server.
The client will verify the certificate issued by the server. After the verification is passed, the client will generate a random number (premaster secret) again, then use the public key in the server certificate to encrypt, and put a ChangeCipherSpec message, which is the message of the encoding change. , as well as the hash value of all previous messages, perform server verification, and then use the new secret key to encrypt a piece of data and send it to the server to ensure that it is correct before formal communication.
- After the server receives the encrypted random number, it uses the private key to decrypt it and obtains the random number (premaster secret).
- Finally, the server and the client use the three random numbers mentioned above (client random, server random, premaster secret) according to the agreed encryption method to generate a symmetric key, which is used to encrypt the entire subsequent conversation process. The server uses a symmetric key to encrypt the response data and transmits it to the client. The client uses the symmetric key to decrypt the response data and obtain the plain text data.
Transmission performance
To discuss transmission performance, explanations need to be made for different HTTP versions,
HTTPS VS HTTP 1.1
In HTTP 1.1 , the performance of HTTP 1.1 is better than that of HTTPS , mainly because HTTPS only adds an SSL/TLS layer to the HTTP 1.1 protocol and has no other modifications.
After adding the SSL/TLS layer, additional encryption and decryption processes are required, which will increase data processing time and transmission time, and will also consume more CPU and memory resources. In addition, the HTTPS protocol also requires certificate verification and key negotiation, which will also increase the connection establishment time.
The HTTP 1.1 connection establishment process only requires a three-way handshake of TCP, while the connection establishment process of the HTTPS protocol also requires an SSL/TLS handshake, which will add at least 6 round-trip times (RTT).
Therefore, the connection establishment time of HTTPS is much longer than that of HTTP 1.1 .
HTTP 2 VS HTTP 1.1
HTTP 2 has much better performance than HTTP 1.1 , mainly in the following points.
binary framing
HTTP 2 uses binary framing, which can reduce data size and format complexity and improve data transmission efficiency.
It mainly modifies the message transmission format of HTTP 1.1 . HTTP 1.1 uses newlines as delimiters for plain text, while HTTP 2 splits all transmitted information into smaller messages and frames and encodes them in a binary format. These frames correspond to messages in a specific data stream. They all Multiplexed within a TCP connection.
Multiplexing
HTTP 2 supports multiplexing, which can transmit multiple requests and responses concurrently on a single connection, avoiding the overhead of head-of-line blocking and repeated connection establishment.
HTTP 2 can send requests and responses simultaneously over a shared TCP connection. HTTP messages can be broken down into independent frames, sent out interleaved without destroying the order of the message itself, and reassembled at the other end based on the stream identifier and headers. Through multiplexing technology, the message header blocking problem of the old version of HTTP can be avoided and the transmission performance can be greatly improved.
header compression
HTTP 2 supports header compression, which can reduce the amount of data transmission and save network bandwidth.
HTTP 2 uses the HPACK algorithm to compress header fields. This compression format encodes the transmitted header fields and reduces the size of the header fields. At the same time, index tables are maintained at both ends to record the header fields that have appeared. Later, during the transmission process, the index numbers of the recorded header fields can be transmitted. After the opposite end receives the data, it can find the corresponding one through the index number. value. Compared with HTTP 1.1, which uses text to transmit message headers, HTTP 2 's header compression can reduce the request resource size.
HTTP 2 Disadvantages
Having said so many advantages of HTTP 2 , we also need to be clear about the disadvantages of HTTP 2 .
- HTTP 2 connection establishment delay: HTTP 2 is still based on the TCP protocol, so TCP three-way handshake and TLS handshake are required, which will consume a certain amount of time and affect data transmission efficiency.
- HTTP 2 head-of-line blocking has not been completely solved: Although HTTP 2 supports multiplexing and can transmit multiple requests and responses concurrently on one connection, if one of the data streams suffers packet loss or delay, the entire TCP connection will be affected. The impact will cause subsequent data flows to be blocked.
- HTTP 2 multiplexing is prone to timeout: The multiplexing technology of HTTP 2 makes multiple requests actually based on the same TCP connection. If the processing time of a certain request is too long, then multiple requests may exceed the client's processing time. timeout, causing the request to fail.
HTTP 3 VS HTTP 2
The improvement of HTTP 3 compared to HTTP 2 can be said to be all-round. The underlying transmission protocol is changed from TCP protocol to QUIC protocol based on UDP protocol, which realizes congestion control and reliable transmission features at the application layer.
advantage
The advantages of HTTP 3 are mainly reflected in its use of the QUIC protocol, which can reduce handshake delays, improve connection stability, support more efficient multiplexing, and better adapt to network changes, etc.
shortcoming
The shortcomings of HTTP 3 are mainly reflected in that it still has some compatibility and stability issues, and sometimes it is even slightly slower than HTTP 2. This may be due to differences in congestion control algorithms, or due to restrictions or filtering of UDP by network devices and firewalls.
As you can see, the performance differences between different HTTP versions are huge. Both HTTP 2 and HTTP 3 are built on HTTPS by default . So if you want higher HTTP protocol transmission performance, you can use HTTP 2 or HTTP 3 protocol.
The cost
The cost of using HTTP is much lower than that of HTTPS , mainly because the HTTPS protocol requires applying for and maintaining a digital certificate, which usually requires a certain fee, and the certificate has a limited validity period and needs to be updated regularly.
In business development, the one-year price of an Alibaba Cloud HTTPS CA enterprise-level certificate usually costs several thousand yuan.
In addition, HTTPS also consumes a lot of server resources, because the encryption and decryption process of the TLS layer also requires the CPU to participate in calculations.
In contrast, HTTP does not need to apply for and maintain digital certificates, nor does it require more server resources, so the cost of using the HTTP protocol is lower.
search ranking
The search ranking of the HTTPS protocol is better than that of the HTTP protocol, mainly because the HTTPS protocol can improve the user's trust and security, thereby increasing the user's visit volume and dwell time, which are important factors for search engine optimization (SEO).
In addition, some mainstream search engines, such as Google and Baidu, have also made it clear that the HTTPS protocol is an important weight indicator for search rankings. In other words, HTTPS websites have more advantages in search rankings than HTTP websites.
Due to the poor security of HTTP protocol, it may lead to user loss and dissatisfaction, thereby affecting user visits and dwell time, which will reduce the effectiveness of search engine optimization (SEO). Moreover, the HTTP protocol is not favored by search engines, so the search ranking of the HTTP protocol is low.
To sum up, the HTTPS protocol has obvious advantages in terms of security and search rankings, while the HTTP protocol is only better in terms of cost control.
With the development of the Internet, the HTTPS protocol has become the choice of more and more websites, while the HTTP protocol has been gradually eliminated. Therefore, it is recommended that website developers and operators upgrade the HTTP protocol to HTTPS protocol as soon as possible to improve the security and competitiveness of the website.