What is MACsec? What changes can it bring to your network environment?

What is MACsec? What changes can it bring to your network environment?
background
Under normal circumstances, most data is transmitted in clear text on LAN links, which will cause many security risks, such as bank account information being stolen and tampered with, and malicious network attacks. After MACsec is deployed in the network, transmitted Ethernet data frames can be protected, reducing the risk of information leakage and malicious network attacks.
MACsec Overview
MACsec (Media Access Control Security) is a secure communication method on a LAN based on the 802.1AE and 802.1X protocols. The security of Ethernet data frames is ensured through functions such as identity authentication, data encryption, integrity verification, and replay protection to prevent the device from processing messages with security threats. MACsec ensures the secure transmission of user business data in the LAN from the following aspects:
- Data frame integrity check
- User data encryption
- Data source authenticity verification
- Replay protection
Typical application scenarios
- Deploy MACsec between switches to protect data security, such as between access switches and uplink aggregation or core switches.
- When there are transmission devices between switches, MACsec can be deployed to protect data security.
1. Point-to-point data transmission
Important data is transmitted between SwitchA and SwitchB, and point-to-point MACsec is deployed to securely protect the data.
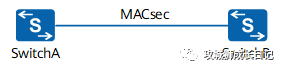
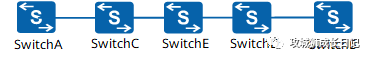
2. Point-to-point data transmission including transparent transmission equipment
There are transparent transmission switches SwitchC, SwitchD, and SwitchE between SwitchA and SwitchB. Point-to-point MACsec is deployed between SwitchA and SwitchB to secure data. To ensure that SwitchA and SwitchB can negotiate MACsec sessions, the transparent transmission switch needs to support the Layer 2 protocol transparent transmission function.
MACsec working mechanism
The MKA (MACsec Key Agreement) protocol is responsible for the establishment and management of MACsec secure channels and the negotiation of keys used by MACsec. The following introduces the basic concepts involved in the working process of the MKA protocol:
- CA (Secure Connectivity Association) is a security association established and maintained by the key agreement protocol. It is a collection of two or more members on the LAN that support MACsec and use the same key and key algorithm suite. The key used by CA members is called CAK (Secure Connectivity Association Key). MACsec is mainly used in point-to-point networking environments, that is, networking from the interface of one device to the interface of another device, so paired CAK is mainly used. Two connected devices form a CA, and they use the same CAK.
- SA (Secure Association) is a security relationship that ensures the safe transmission of data frames between CA members. Each SA has one or a set of keys for encrypting data frames, called SAK (Secure Association Key). SAK is generated by an algorithm based on CAK and is used for encryption and decryption of data messages.
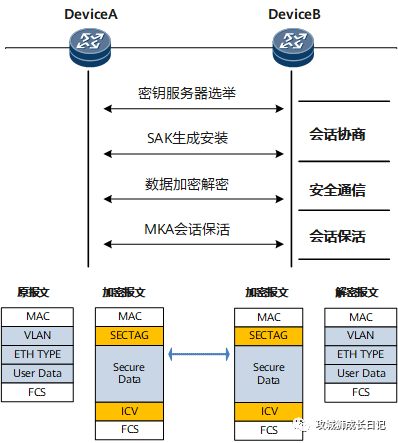
1. Operating mechanism
The point-to-point MACsec interaction process is mainly divided into three stages: session negotiation, secure communication, and session keepalive.
Schematic diagram of MACsec interaction process
Point-to-point MACsec interaction process:
(1) Session negotiation
- After the MACsec function is enabled on the interfaces of the devices at both ends, a key server (Key Server) is elected based on priority. Users can configure the priority value of the interface. The smaller the value, the higher the priority. The device interface with higher priority will be elected as the key server. When the priorities of both parties are the same, the SCI (Secure Channel Identifier) value of the interface is compared. The SCI consists of the interface MAC address and the last two bytes of the interface index (Interface Index). The interface with the smaller SCI value will be elected as the key. server.
- The devices at both ends are statically configured with the same CAK. The key server generates a SAK for encrypting data packets based on the statically configured CAK and distributes it to the opposite device.
(2) Secure communication
The sender uses SAK to encrypt the data message, and the receiver uses SAK to decrypt the data message. The devices at both ends can serve as both senders and receivers, and the communication process is protected by MACsec. Users can also configure the timeout period of the SAK. When the SAK usage time reaches the timeout period or the number of SAK encrypted messages reaches a certain number, the SAK will be replaced to ensure the security of the key.
(3) Session keep-alive
The MKA protocol defines an MKA session keep-alive timer, which is used to specify the timeout period of the MKA session. After the MKA session negotiation is successful, the devices at both ends will confirm the existence of the connection by exchanging MKA protocol messages. After receiving the peer MKA protocol message, the device starts the timer.
- If an MKA protocol message from the peer is received within the timeout period, the timer will be restarted.
- If no MKA protocol message from the peer is received within the timeout period, the connection is considered to be unsafe, the peer device is deleted, and MKA negotiation is performed again.
- CAK (Secure Connectivity Association Key) is not directly used to encrypt data messages. It and other parameters are used to derive the encryption key of data messages. The CAK can be issued during the 802.1X authentication process, or it can be statically configured directly by the user.
- MKA (MACsec Key Agreement protocol) is a negotiation protocol for MACsec data encryption keys.
- SAK (Secure Association Key) is derived from CAK based on the algorithm and is used to encrypt data transmitted between secure channels. MKA has a limit on the number of messages that can be encrypted by each SAK. When the PN encrypted by a certain SAK is exhausted, the SAK will be refreshed. For example, on a 10Gbps link, SAK is refreshed every 4.8 minutes at the fastest.
- Key Server determines the encryption scheme and the MKA entity for key distribution.
Introduction to configuration commands
1. Configure static CKN and CAK
Enter system view:
system-view- 1.
Enter the interface view:
interface interface-type interface-number [ .subinterface-number ]- 1.
Configure static CKN and CAK:
mka cak-mode static ckn ckn cak { simple cak-simple | cipher cak-cipher }- 1.
2. Configure MACsec encryption mode
When the data packets sent by the interface are encrypted by MACsec, you can choose to configure the encryption mode of the interface.
- normal: performs both integrity check and data encryption.
- integrity-only: Only integrity verification is performed without data encryption.
Enter system view 1:
system-view- 1.
Enter the interface view:
interface interface-type interface-number [ .subinterface-number ]- 1.
Configure the encryption mode of MACsec:
macsec mode { normal | integrity-only }- 1.
3. Configure the MACsec encryption algorithm
Enter system view:
system-view- 1.
Enter the interface view:
interface interface-type interface-number [ .subinterface-number ]- 1.
Configure the encryption algorithm of MACsec:
macsec cipher-suite { gcm-aes-128 | gcm-aes-xpn-128 | gcm-aes-256 | gcm-aes-xpn-256 }- 1.
4. View configuration results
View statistics on MACsec-protected data packets.
display macsec statistics interface { interface-name | interface-type interface-number}- 1.
View MKA session information:
display mka interface { interface-name | interface-type interface-number }- 1.
MACsec configuration example
1. Configure point-to-point MACsec
Point-to-point MACsec configuration network diagram
Router DeviceA is directly connected to router DeviceB, and MACsec data packets are encrypted and decrypted on interface GE1/0/0 of DeviceA and DeviceB.
2. Configuration ideas
Use the following idea to configure point-to-point MACsec: Configure the same static CKN and CAK on the GE1/0/0 interfaces of DeviceA and DeviceB;
3. Data preparation
To complete this configuration example, you need to prepare the following data:
- CKN and CAK values of the interface
- The data sent by the DeviceA interface is encrypted through gcm-aes-xpn-128
4. Operation steps
Interface GE1/0/0 is configured with ciphertext CKN and CAK.
<DeviceA> system-view
[~DeviceA] interface gigabitethernet1/0/0
[~DeviceA-GigabitEthernet1/0/0] mka cak-mode static ckn a1 cak cipher b1b1b1b1b1b1b1b1b1b1b1b1b1b1b1b1
[*DeviceA-GigabitEthernet1/0/0] commit- 1.
- 2.
- 3.
- 4.
Configure the MACsec encryption mode on interface GE1/0/0. (Optional):
<DeviceA> system-view
[~DeviceA] interface gigabitethernet1/0/0
[~DeviceA-GigabitEthernet1/0/0] macsec mode integrity-only
[*DeviceA-GigabitEthernet1/0/0] commit- 1.
- 2.
- 3.
- 4.
Configure the MACsec encryption algorithm on interface GE1/0/0. (Optional)
<DeviceA> system-view
[~DeviceA] interface gigabitethernet1/0/0
[~DeviceA-GigabitEthernet1/0/0] macsec cipher-suite gcm-aes-xpn-128
[*DeviceA-GigabitEthernet1/0/0] commit- 1.
- 2.
- 3.
- 4.
DeviceB performs the same configuration.