Revealing the secrets of Ethernet security technology: How does IPSG protect your online world?

Revealing the secrets of Ethernet security technology: How does IPSG protect your online world?
Introduction to IPSG
1.Definition
IP source defense attack IPSG (IP Source Guard) is a source IP address filtering technology based on Layer 2 interfaces. It can prevent malicious hosts from forging the IP addresses of legitimate hosts to impersonate legitimate hosts. It can also ensure that unauthorized hosts cannot pass the IP address specified by themselves. IP address to access the network or attack the network.

2.Purpose
As the scale of the network becomes larger and larger, network attacks implemented by forging source IP addresses (referred to as IP address spoofing attacks) are also gradually increasing. Some attackers obtain network access rights by forging the IP addresses of legitimate users, illegally access the network, and even cause legitimate users to be unable to access the network, or information is leaked. IPSG provides a defense mechanism against IP address spoofing attacks, which can effectively prevent such network attacks.
A typical example of using IPSG to prevent attacks is shown in the figure below. An illegal host forges the IP address of a legal host to obtain Internet access. At this time, by deploying the IPSG function on the user-side interface or VLAN of the Device, the Device can check the IP packets entering the interface and discard packets from illegal hosts, thereby preventing such attacks.
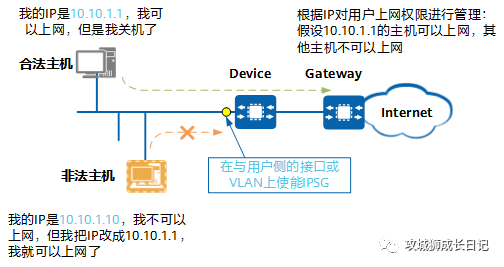
IPSG typical attack defense
Basic principles of IPSG
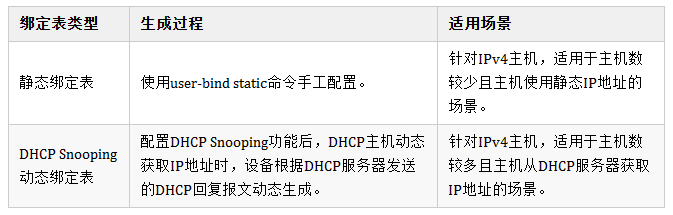
IPSG uses the binding table (binding relationship between source IP address, source MAC address, VLAN, and incoming interface) to match and check the IP packets received on the Layer 2 interface. Only packets matching the binding table are allowed to pass. Other messages will be discarded.
The binding table is shown in the following table, including static and dynamic.
After the binding table is generated, IPSG delivers an ACL to the specified interface or specified VLAN based on the binding table, and the ACL is used to match and check all IP packets. Messages sent by the host will only be allowed to pass if they match the binding table. Messages that do not match the binding table will be discarded. When the binding table information changes, the device will re-issue the ACL. By default, if IPSG is enabled without a binding table, the device will allow IP protocol packets except IGMP protocol packets to pass, but will reject all IP data packets.
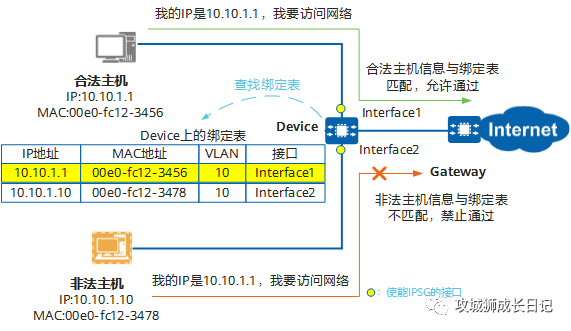
IPSG is generally applied to user-side access equipment and can be applied based on interfaces or VLANs.
- Apply IPSG on the user-side interface, and all IP packets received by the interface will be checked by IPSG.
- Apply IPSG to the user-side VLAN, and all interfaces belonging to the VLAN will perform IPSG checks upon receiving IP packets.
- If the access device on the user side does not support the IPSG function, you can also apply IPSG on the interface or VLAN of the upper-layer device.
Interface roles in IPSG
IPSG only supports application on Layer 2 physical interfaces or VLANs, and only untrusted interfaces with the IPSG function enabled are checked. For IPSG, all interfaces are untrusted interfaces by default, and trusted interfaces are specified by the user. The trusted interface/untrusted interface of IPSG is also the trusted interface/untrusted interface in DHCP Snooping. The trusted interface/untrusted interface is also applicable to IPSG based on the static binding table method.
The roles of each interface in IPSG are shown in the figure below. in:
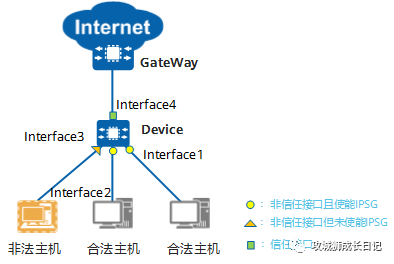
- Interface1 and Interface2 are untrusted interfaces and the IPSG function is enabled. IPSG inspection is performed on packets received from Interface1 and Interface2.
- The Interface3 interface is an untrusted interface but the IPSG function is not enabled. IPSG inspection is not performed on packets received from the Interface3 interface, and there may be attacks.
- The Interface4 interface is a trusted interface designated by the user. IPSG inspection will not be performed on packets received from the Interface4 interface. However, there are generally no attacks on this interface. In a DHCP snooping scenario, the interface directly or indirectly connected to the legitimate DHCP server is usually set as a trusted interface.
IPSG filtering method
Binding table entries include: MAC address, IP address, VLAN ID, and incoming interface. The information specified in the static binding entry is used for IPSG filtering of packets received by the interface. For the dynamic binding table, IPSG filters the packets received by the interface based on the information in the table entry, which is determined by the check items set by the user. By default, all four items are checked for matching. Several common inspection items are as follows:
- Filter based on source IP address
- Filter based on source MAC address
- Filter based on source IP address + source MAC address
- Filter based on source IP address + source MAC address + interface
- Filter based on source IP address + source MAC address + interface + VLAN
Introduction to IPSG configuration commands
(1) Configure static user binding entries:
[Huawei] user-bind static { { { ip-address | ipv6-address } { start-ip [ to end-ip ] } &<1-10> | ipv6-prefix prefix/prefix-length } | mac-address mac-address } * [ interface interface-type interface-number ] [ vlan vlan-id [ ce-vlan ce-vlan-id ] ]- 1.
[Huawei] user-bind static { { { ip-address | ipv6-address } { start-ip [ to end-ip ] } &<1-10> | ipv6-prefix prefix/prefix-length } | mac-address mac-address } * [ interface interface-type interface-number ] [ vlan vlan-id [ ce-vlan ce-vlan-id ] ]- 1.
(2) Enable IPSG function:
[Huawei-GigabitEthernet0/0/1] ip source check user-bind enable- 1.
Enable the IP packet inspection function on the interface or VLAN, and make the VLAN view configuration consistent with the interface view.
(3) Enable IP packet inspection alarm function:
[Huawei-GigabitEthernet0/0/1] ip source check user-bind alarm enable- 1.
(4) Configure IP packet inspection alarm thresholds
[Huawei-GigabitEthernet0/0/1] ip source check user-bind alarm threshold threshold- 1.
After the IP packet inspection alarm function is configured, when the discarded IP packets exceed the alarm threshold, an alarm will be generated to remind the user.
IPSG configuration example
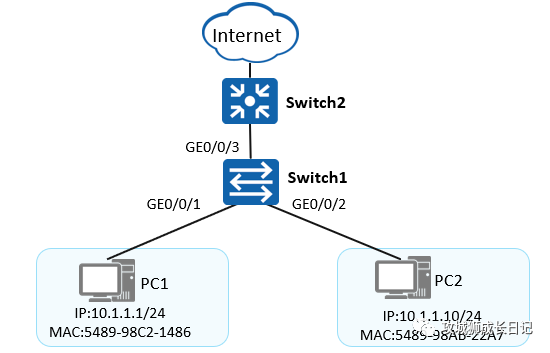
As shown in the figure: Network terminal equipment is manually configured with static IP addresses for unified management, and IPSG is configured on the access switch to prevent hosts from illegally gaining access to the network by changing their IP addresses privately.
- Configure static binding table
- Enable IPSG and alarm reporting functions
Switch1 is configured as follows:
#在接入交换机上配置静态绑定表
[Switch1] user-bind static ip-address 10.1.1.1 mac-address 5489-98C2-1486
[Switch1] user-bind static ip-address 10.1.1.10 mac-address 5489-98AB-22A7
#使能GE0/0/1接口IPSG和IP报文检查告警功能
[Switch1] interface GigabitEthernet 0/0/1
[Switch1-GigabitEthernet0/0/1] ip source check user-bind enable
[Switch1-GigabitEthernet0/0/1] ip source check user-bind alarm enable
[Switch1-GigabitEthernet0/0/1] ip source check user-bind alarm threshold 100
#接口GE0/0/2配置与GE0/0/1类似,此处省略- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
To verify the configuration, execute the display dhcp static user-bind all command on the Switch to view the static binding table information. PC1 and PC2 can access the network normally using the fixed IP addresses assigned by the administrator, but cannot access the network after changing the IP addresses.