Blogger uses Raspberry Pi to bypass Windows Bitlocker encryption in less than a minute
According to news on February 7, the Bitlocker encryption function built into Microsoft Windows 10 and 11 Professional Edition has always been considered a convenient and easy-to-use security solution. However, YouTube blogger stacksmashing recently discovered a huge security flaw in Bitlocker, and he successfully bypassed the encryption in less than a minute using a Raspberry Pi Pico worth less than $10.

stacksmeshing achieved this attack by exploiting a Trusted Platform Module (TPM) design flaw present in many systems. In some configurations, Bitlocker relies on an external TPM to store critical information, such as platform configuration registers and volume master keys, but some CPUs have a built-in TPM. stacksmeshing found that the communication channel between the CPU and the external TPM was completely unencrypted during boot, allowing an attacker to steal critical data.
Based on this discovery, stacksmeshing compromised a laptop equipped with Bitlocker encryption and successfully read the TPM data. He discovered that the laptop's TPM was reading data through an unused connector on the back of the motherboard, right next to one of the laptop's M.2 ports.
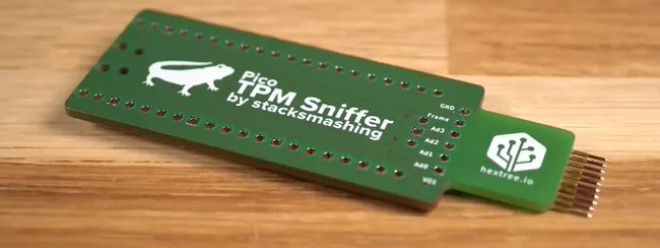
IT House noticed that in order to read the data on the connector, stacksmeshing made a cheap Raspberry Pi Pico device, which can be connected to the unencrypted connector by simply touching the protruding metal pads on the device. Pico is programmed to read the raw 1s and 0s from the TPM, thereby obtaining the volume master key stored on the module.
Research by stacksmeshing shows that Windows Bitlocker and external TPMs are not as secure as previously thought due to the unencrypted communication channel between the TPM and CPU. The good news is that the vulnerability appears to only exist on standalone TPMs. If your CPU has a built-in TPM (both modern Intel and AMD CPUs do), you should be protected from this security hole because all TPM communication occurs inside the CPU.