Understand DNS and how it works in one article

Introduction to Labs
Think of your smartphone contact list as a list of names and contact details for people on the entire planet. Whenever you want to call or text someone, you just find their name in your contact list instead of having to remember their phone number or email address. It's like a giant phone book that allows you to easily find and communicate with anyone in the world.
Similarly, every device on the Internet has a unique identification number called an IP address. When you type a URL into your browser to access a website, your computer needs to know the IP address for that URL, just like you need to know someone's phone number to contact them. DNS is like a giant contact list on the Internet. It matches easy-to-remember domain names (such as www.example.com) with corresponding IP addresses, allowing you to easily visit websites, send emails, etc. So, while you may not understand the technical details of DNS, you use it every day in various activities on the Internet to enable different devices to communicate with each other.
Part 01. A brief history of DNS
- ARPANET era (1960s-1980s): The early Internet did not have a global domain name system, but used hostnames to identify computers on the network. These hostnames are stored in a text file called "hosts.txt", which is manually maintained by the network administrator.
- Creation of DNS (1983): As the Internet grew, a more efficient way to manage and find mappings between hostnames and IP addresses was needed. In 1983, Paul Mockapetris and Jon Postel began developing DNS. They published RFC882 and RFC883, which detail the design of DNS.
- Hierarchy of DNS (1980s-1990s): DNS was designed as a hierarchical system consisting of multiple domain name servers, each of which is responsible for managing domain name and IP address mapping within a specific area. The root name server is at the top level, followed by top-level domain name servers (TLDs), followed by authoritative name servers and caching name servers.
- Commercialization and Growth (1990s-2000s): As the Internet became commercialized, the number of domain name registrations increased dramatically, causing the DNS system to come under pressure. In order to meet the demand, domain name registrars and hosting service providers began to provide domain name registration and management services.
- Introduction of DNSSEC (2000s): To improve DNS security, DNSSEC (Domain Name System Security Extensions) was introduced. It ensures the integrity and authenticity of domain name resolution through a digital signature mechanism and prevents attacks such as DNS hijacking and cache poisoning.
- Launch of new top-level domain names (2010s): ICANN (Internet Corporation for Assigned Names and Numbers) began to approve new top-level domain names, such as ".app", ".blog", etc., enriching the diversity of Internet domain names.
- IPv6 and DNS64/NAT64 (2010s): With the introduction of IPv6, DNS also needs to adapt to the new IP address format. DNS64/NAT64 technology allows communication between IPv6 and IPv4, allowing IPv6 networks to access resources on IPv4 networks.
- Ongoing development (to this day): DNS continues to evolve to adapt to new Internet needs and security challenges. With the development of emerging technologies such as cloud computing and the Internet of Things, the role of DNS in the network ecosystem has become increasingly important.
Part 02. How does DNS work?
DNS uses a hierarchical and distributed structure to manage the mapping relationship between domain names and IP addresses. It makes it easy to use human-readable domain names on the Internet to access various network resources through recursive and iterative query processes. The design of this system enables the entire Internet to work more efficiently and also brings better flexibility and scalability. Its working principle involves multiple levels of domain name servers and the query and response process.
(1) Classification of domain name servers
Domain name servers can be divided into the following four different types based on their roles and hierarchies:
(1)Root Name Servers
The root domain name server is located at the highest level of the DNS hierarchy. There are 13 root domain name servers with different IP addresses distributed around the world. They store information about top-level domain name servers and are responsible for managing the IP addresses of domain name servers for top-level domain names (such as .com, .org, .net, etc.). When the local domain name server receives a query request, if it needs to query the IP address of the top-level domain name server, it will initiate a query to the root domain name server to obtain the corresponding top-level domain name server address.
(2)Top-Level Domain Servers
The top-level domain name server is responsible for managing the mapping of domain names and subdomains under specific top-level domains (such as .com, .org, .net, etc.). For example, the .com top-level domain name server stores all domain name mapping information that ends with .com domain name. When the local domain name server queries the root domain name server, if it needs to query the IP address of a specific top-level domain, it will request the corresponding top-level domain name server to obtain guidance on the next step.
(3) Authoritative Name Servers
Authoritative name servers are the "official" name servers for each specific domain name, and they store mapping information between the domain name and the IP address. When the local domain name server needs to resolve a specific domain name, it sends a query request to the authoritative domain name server for the domain name. These servers can provide exact mapping information or direct lower-level name servers to perform further queries.
(4)Local Name Servers
Local name servers are located on the user's local network, usually provided by an Internet Service Provider (ISP). When a user initiates a domain name query request, the local domain name server is first contacted. If the local domain name server has cached the corresponding mapping information, it will return the result directly. Otherwise, it will initiate a query to the root domain name server, top-level domain name server and authority domain name server through recursive query or iterative query according to the query domain name hierarchical structure to obtain the required mapping information.
(2) DNS domain name resolution process
Domain name resolution includes two query methods, namely recursive query and iterative query.
(1) Recursive query
The client sends the query request to the recursive DNS server, and the server must return the results and cannot simply forward the request to other servers. If the recursive server cannot resolve it, it iterates queries to other DNS servers until it obtains a result, which is then returned to the client. The whole process is transparent to the client, and the local server is under heavy load, but the query is fast.
(2)Iterative query
During the entire iterative query process, the local domain name server queries upwards step by step, and then downwards until the required IP address is obtained. This query mode ensures that each step of the query is completed step by step, maintaining the consistency and correctness of the data. At the same time, each query link can be cached to improve query efficiency and reduce the burden on the DNS server.
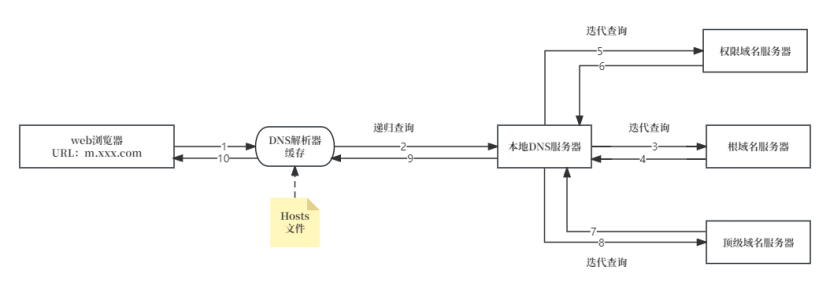
①Local domain name server starts query: When the user enters a domain name in the browser, the local domain name server (usually provided by the Internet service provider) is triggered to perform domain name resolution.
②The local domain name server initiates a query to the root domain name server: The local domain name server initiates a query request to a root domain name server, and the request contains the domain name that needs to be resolved.
③Response from the root domain name server: The root domain name server will not directly provide the required IP address, but will reply to the local domain name server with an IP address pointing to the top-level domain name server. This top-level domain name server is associated with the top-level domain of the queried domain name, such as ".com", ".org", etc.
④The local domain name server initiates a query to the top-level domain name server: The local domain name server initiates a new query request to the obtained top-level domain name server and continues to request the required domain name mapping.
⑤Response from the top-level domain name server: The top-level domain name server replies to the local domain name server with an IP address pointing to the authority domain name server. This authority domain name server is the official server responsible for managing a specific domain name and can provide exact mapping information.
⑥ The local domain name server initiates a query to the authority domain name server: The local domain name server initiates a new query request to the obtained authority domain name server to request the IP address of the required domain name.
⑦Response from the authoritative domain name server: The authoritative domain name server replies to the local domain name server to query the IP address of the required domain name.
⑧The local domain name server returns the result: The local domain name server returns the obtained IP address to the user's computer, so that it can establish a connection with the target server, thereby achieving access to the website or resources.
Part 03, DNS security
As the key infrastructure of the Internet, DNS security directly affects the stable operation of the entire network. However, the DNS system also faces various threats, including:
- DDoS attack: exhausting DNS server resources through a traffic-level denial of service attack
- Domain name hijacking: maliciously binding a domain name to an IP address controlled by the attacker
- DNS Poisoning/Cache Pollution: Phishing, spreading malware, etc. by implanting incorrect DNS records
In order to enhance the security of DNS, the industry has adopted various technical means for protection.
- DNSSEC provides digital signatures to prevent resolution records from being tampered with
- Anycast and multiple domain name servers avoid single points of failure
- Recursive DNS servers filter malicious queries to protect users
- DNS over HTTPS encrypted transmission ensures query privacy and security, etc.
In response to the security threats faced by DNS, we provide users with comprehensive security protection:
- Support DNS over HTTPS transmission encryption to prevent eavesdropping
- Anycast technology and multi-node deployment ensure high service availability
- Threat intelligence based on big data analysis to detect and defend against attacks
- Intelligent parsing and filtering mechanism to intercept malicious websites and protect users
Through the comprehensive application of various technical means, China Mobile's secure DNS service can effectively resist common threats and ensure user query security and experience.
Part 04. Summary and outlook
As the digital phone book of the Internet, DNS's development history reflects the evolution of Internet technology and governance models, and its unique hierarchical tree structure also makes DNS an efficient and reliable core service. Facing the future, DNS will face challenges from emerging networks, and there is still room for improvement in its security and performance. New technologies such as blockchain, artificial intelligence, etc. can also be applied to future DNS systems to enhance their functionality. With the advent of the 5G era, DNS will play a more important role in supporting ultra-large-scale network connections. With the joint efforts of multiple stakeholders, DNS will continue to evolve and continue to promote the development of Internet technology.