What about the SSH protocol? Why does a normal connection suddenly report an Identification problem?

What about the SSH protocol? Why does a normal connection suddenly report an Identification problem?
They have the advantages of simple operation and high transmission efficiency, but they all have the same problem, that is, the security risks caused by clear text transmission of data. SSH uses methods such as encrypting data transmission and improving authentication strength to overcome the security issues in Telnet and FTP applications and realize secure remote login and file transfer services.
SSH
- SSH is mainly a connection protocol. Why do we need SSH? , once the content transmitted by traditional protocols is intercepted, it will be completely exposed, and the content will be exposed. The SSH protocol encrypts and verifies network data and establishes a secure tunnel between the SSH client and the SSH server, providing a secure transmission channel for network services in an insecure network environment.
They have the advantages of simple operation and high transmission efficiency, but they all have the same problem, that is, the security risks caused by clear text transmission of data. SSH uses methods such as encrypting data transmission and improving authentication strength to overcome the security issues in Telnet and FTP applications and realize secure remote login and file transfer services.
- But when I use SSH, I actually get Remote Host Identification Has Changed error and solution. Now that there is a problem, it must be solved. Next, let’s see how the problem is solved.
Scenes
- The service I originally connected to via ssh suddenly became unavailable, which caught me off guard.
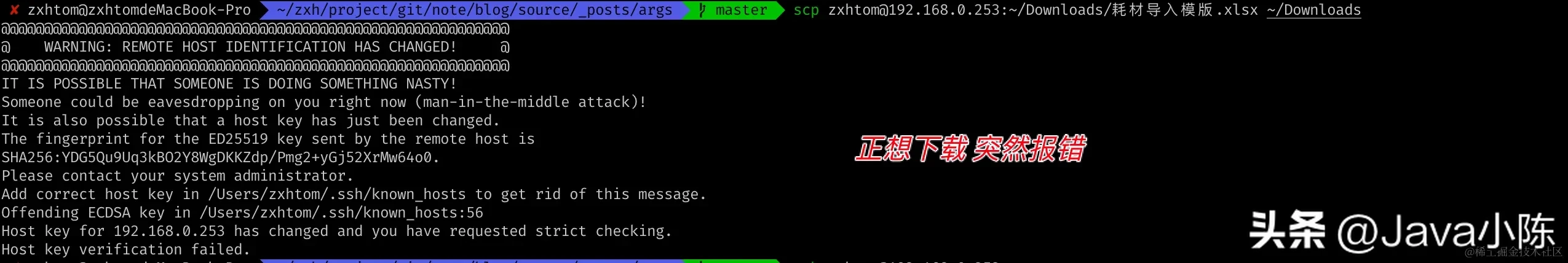
- This service is my virtual machine. There was no problem with the connection before, and it was confirmed that the username was legal. I was not asked to enter a password, so there was no password error.
identify the problem
- Use the problem error statement [Remote Host Identification Has Changed error and solution]. Among them, identification means authentication, which means authentication failed. How could the authentication fail for Hao Duanduan?
- Then came the days of self-reflection. I've been thinking about it for a long time, but my friend reminded me. Could it have anything to do with you reinstalling the system? It seems to be related to this problem scenario. Because the system version was upgraded before, I did a system reinstallation operation. Now that I think about it, although the IP is still the same IP, the service is no longer the same as before.
- After reading the information, I found that the problem was not caused by reinstalling the system. To be precise, it was not directly caused by reinstalling the system, but because we reinstalled OpenSSH, which caused the service authentication to fail.
ssh storage
- Before solving this problem, let’s start with a little discussion. Do you know where the ssh connection information is stored? Have you ever noticed that when you first connect to a service you are asked to enter yes or no for confirmation?
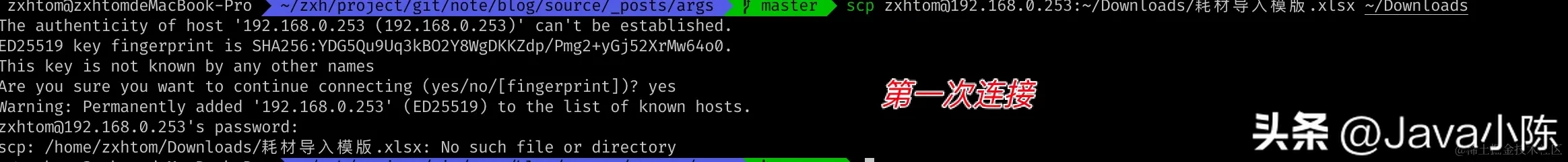
- The first connection requires us to confirm whether to continue the connection. After entering yes, the server's connection information will be appended to known hosts, and the corresponding location is ~/.ssh/known_host.
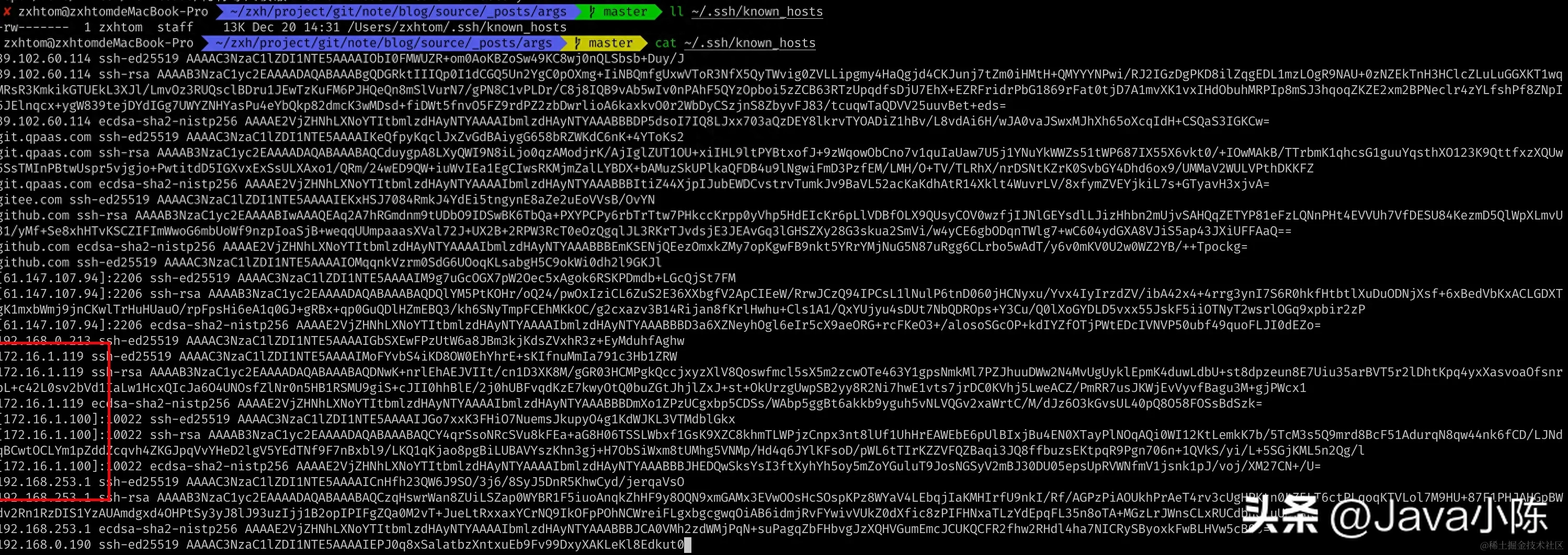
- If you open the file and take a look, you will find that it is a signature storage for each service, so when we reinstall OpenSSH, the signatures here will become invalid.
Back to the topic
- Knowing that the connection cannot be connected due to the expiration of the ssh storage signature location, it is easy to solve the problem. We can directly delete the signature corresponding to 192.168.0.253. But the problem is still a little troublesome. We also saw above that there seem to be many signatures for the same IP. Which one should be deleted? In theory, that's all. Another problem is that it is very troublesome for us to locate and delete. Fortunately, linux OpenSSH provides us with commands.
ssh-keygen -R {ssh.server.ip.address} -f file- 1.
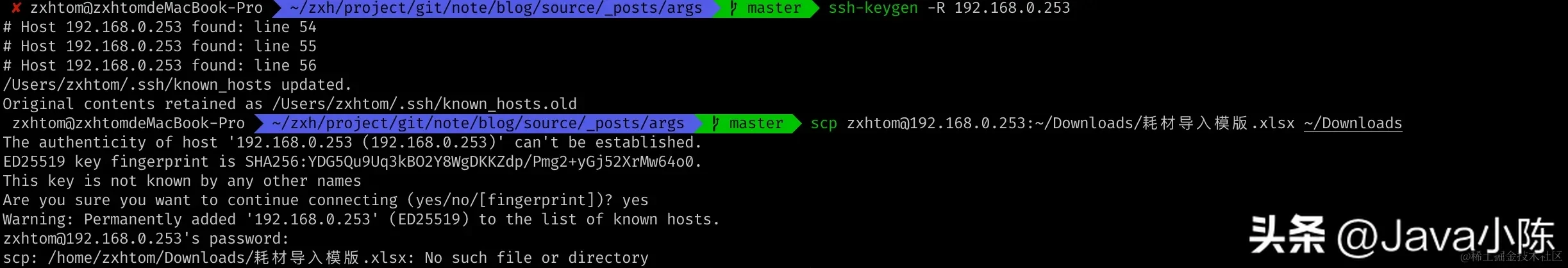
- After executing ssh-keygen, the discovered configuration related to the specified service will be printed. Then it will be updated, and when we connect again, we will perform a confirmation, and then we can operate normally.