Attack methods and defense measures on the wireless link layer of 4G LTE

Attack methods and defense measures on the wireless link layer of 4G LTE
1. 4G LTE air interface protocol framework
Long Term Evolution (LTE) is the project name of an innovative high-performance air interface used in mobile communication systems, and it is also a communication system and communication standard. LTE is the long-term evolution of the Universal Mobile Telecommunications System (UMTS) technical standard formulated by The 3rd Generation Partnership Project (3GPP), and was officially launched at the 3GPP Toronto meeting in December 2004. Create a project and start it. In fact, there is still some distance between LTE and 4G indicators, but the technologies used include Orthogonal Frequency Division Multiplexing (OFDM), Multi-Input Multi-Output (MIMO), etc. These Technology is the key technology of 4G, so it is also called quasi-4G.
The 4G LTE air interface protocol stack is divided into three layers: the physical layer, the wireless link layer and the top layer. The wireless link layer has three sublayers, namely the MAC layer, the RLC layer and the PDCP layer, while the top layer has the RRC layer, NAS Layer and IP layer three sub-layers. The air interface protocol of 4G LTE can be divided into user plane and control plane. The user plane can provide user data transmission services for the upper layer protocol stack through the transmission channel of the air interface, and also provide transmission channels for the control plane and NAS signaling. The user plane protocol stack is mainly composed of the physical layer, MAC layer, RLC layer, and PDCP layer. and IP layer, as shown in Figure 2-1.
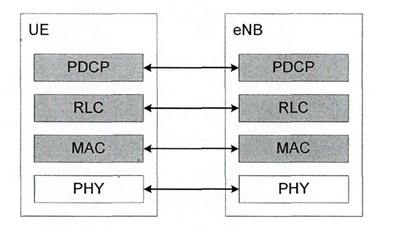
Figure 2‑1 User plane of LTE protocol stack
The control plane is mainly responsible for the management of user wireless resources, the establishment of wireless connections, the guarantee of service quality and the release of resources. Its protocol stack is composed of physical layer, MAC layer, RLC layer, PDCP layer, RRC layer and NAS layer, such as As shown in Figure 2-2.
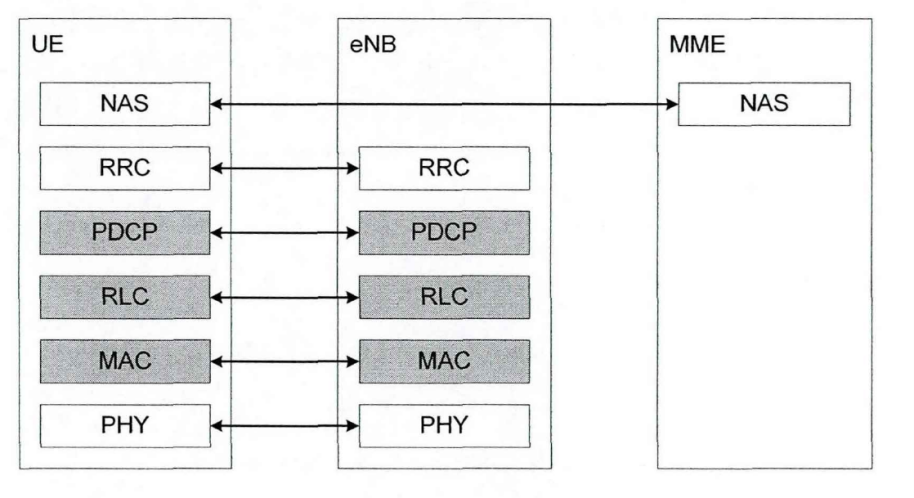
Figure 2-2 User plane of LTE protocol stack
1.1 Physical layer
The physical layer is the bottom layer of the 4G LTE protocol stack. It is mainly responsible for the conversion between bit data and radio signals, and also provides protection for data transmission at the MAC layer, such as: error checking and error correction, rate matching, power control or distribution etc.
The physical layer is responsible for scheduling radio resource blocks, so that the physical layer of 4G LTE is used for different spectrum allocations, where radio resource blocks can be divided into time domain, frequency domain and air domain. A radio resource block in the time domain can be divided into multiple radio sub-frames, one subframe is 1, and consists of two time slots, and each time slot consists of 7 OFDM symbols. Resources in the frequency domain may be called subcarriers. A time slot in the time domain and 12 subcarriers in the frequency domain can form a 2-dimensional grid, which is called a resource block (Resource Block, RB). Wherein, each small network in each resource block may be called a resource element (Resource Element, RE). The resources in the airspace are logically mapped to antenna ports, and each port corresponds to a single time-frequency resource grid.
A series of resource elements carrying higher-level information are called physical channels, including physical control channels, physical data channels, downlink broadcast channels, and uplink random access channels. Wherein, the uplink refers to the data or signaling transmitted by the base station to the terminal user, and the downlink refers to the data or signaling transmitted by the terminal user to the base station.
1.2 Wireless Link Layer
The radio link layer can be further divided into a medium access control (MAC) sublayer, a radio link control (RLC) sublayer and a packet data convergence (PDCP) sublayer. The wireless link layer is mainly responsible for organizing the bit data of the physical layer and providing data transmission services to the top layer.
1.2.1 MAC sublayer
The MAC sublayer protocol is responsible for scheduling the medium to access the radio resources of the physical layer, and provides radio resource allocation services for the RLC sublayer and PDCP sublayer. The functions of the MAC sublayer on the base station and the end user are not exactly the same; the same functions of the two are:
(1) Mapping: transmission from logical channels to transport channels;
(2) Multiplexing: Multiplexing the MAC SDU of the logical channel into a transport block (TB) and transmitting it to the physical layer through the transport channel;
(3) Demultiplexing: demultiplexing the transport blocks from the physical layer on the transport channel into MAC SDUs of the logical channel;
(4) Correction: Errors in transmission are corrected by Hybrid Automatic Repeat request (HARQ).
Unique features of the MAC in the base station:
(1) Allocate radio resources such as resource blocks, transmit power, etc. to end users;
(2) Prioritize resource allocation for end users;
(3) Select the transmission format.
Unique Features of MAC in Terminal:
(1) Control the logical channel;
(2) Scheduling information report.
Overall, the MAC sublayer is mainly responsible for the multiplexing and demultiplexing of transport blocks between logical channels and transport channels, and finally provides reliability through the HARQ mechanism.
1.2.2 RLC sublayer
The main functions of the RLC sublayer are to provide segmentation and reassembly for the data packets of the PDCP sublayer, and to manage the retransmission of service data packets, thereby providing reliable services for the transmission of user data and control data. Among them, the RLC sublayer can be divided into three transmission modes: Transparent Mode (Transparent Mode, TM), Acknowledged Mode (Acknowledged Mode, AM), and Unacknowledged Mode (Unacknowledged Mode, UM). Acknowledgment mode can retransmit RLC PDUs that were not received correctly, so as to realize error-free and sequential transmission of data packets. The unacknowledged mode is opposite to the acknowledged mode, and the RLC PDU is not retransmitted. The transparent mode only transparently transmits the data without any processing on the data.
1.2.3 PDCP sublayer
The PDCP sublayer is mainly responsible for the transmission protection of the messages of the control plane and the user plane. On the control plane, the PDCP sublayer is responsible for encryption and integrity protection; for IP data on the user plane, the PDCP sublayer only performs header compression and encryption, and does not provide integrity protection. Since the PDCP sublayer is the first sublayer in the protocol stack that encrypts and integrity protects data packets from bottom to top, we can read the load and header information of all data packets under the PDCP sublayer to analyze the wireless link. Meta information of the road layer, such as the packet length of the PDCP sublayer. In this article, we identify and analyze traffic by collecting and analyzing the PDCP packet length characteristic of the PDCP sublayer.
1.3 Top layer
The top layer is mainly divided into three sublayers, namely Radio Resource Control (RRC), Non-Access Stratum (NAS), and Internet Protocol (Internet Protocol).
The RRC sublayer is mainly responsible for radio session management and radio bearer control. All radio connections such as RRC connections between the base station and end users will be performed on this sublayer, therefore, procedures such as paging and system information broadcasting will also be performed on this sublayer. Only after the terminal user completes the RRC connection with the base station, the terminal user can receive and send network data.
The NAS sublayer is mainly responsible for terminal user mobility and session management, that is, user identification, authentication, and security control, but at the same time, this sublayer will also update the end user tracking area and assign temporary network identifiers. The signaling or data at the NAS sublayer will be subject to mandatory integrity protection and encryption.
The IP sublayer provides a port for the device's operating system to access the network. Each end user will have an IP address, through which the user's data packets can be identified and forwarded in the mobile network. At the same time, the core network will also manage and control the traffic of users accessing the network.
2. Attacks against the wireless link layer
2.1 Identity Mapping Attack
Identity and location are important privacy of users. If attackers can obtain identifiers through the characteristics of air interface traffic, they can use identifiers to identify users and analyze their traffic characteristics. Since the base station uses the random access process to synchronize with the uplink user, this initial MAC layer process occurs under the PDCP layer, so there is no protection mechanism, and the user transmits information to the base station in plain text, which leads to attackers. Use this vulnerability to steal user's private information. Identity mapping attacks can be divided into passive identity mapping attacks and active identity mapping attacks.
2.1.1 Passive identity mapping attack
Before the user accesses the cell network, identity authentication will be performed with the cell base station. During the authentication process, everything is transmitted in plain text, which makes the user's IMSI and TMSI transparent. In addition to the user's IMSI and TMSI being transparent, the user's RNTI data is also transparent to the base station of the cell. Therefore, the attacker can perform service identification and location tracking of the user according to the user's RNTI. Attackers can steal user traffic data over the air interface through software radios such as USRP. [1][2] proved that the attack is effective. However, since RNTI only exists in the state of RRC connection, and within a period of time, if the user does not transmit data with the base station for a period of time, the RNTI will also change, which also makes it very difficult for an attacker to simply use RNTI Difficult to track users. Although the RNTI will change, [3] also summarizes the law of RNTI changes, which shows that the attacker can predict the user's next RNTI according to the way the base station allocates the RNTI, so as to identify the user based on the change of the user's traffic. Business. Alternatively, [4] can also identify specific user data by stealing the RNTI and the corresponding TMSI during the random access process of the MAC layer and mapping them one by one.
2.1.2 Active identity mapping attack
The implementation difficulty of active identity mapping attack is relatively greater than that of passive identity mapping attack. In [2], since the header information of RLC, MAC, PDCP uplink packets is readable in the uplink transmission, the attacker can send data in the allocated resources with appropriate header settings, by sending data can Change the scheduling algorithm of data packets to steal bandwidth, or change the load algorithm of the base station so that new users who want to join cannot connect to the cell base station.
2.1.3 Solutions
The user specifically studies the RNTI allocation strategy of a certain base station, and can predict the change of the RNTI of the targeted user. However, the paper also shows that the RNTI will find random assignments. Therefore, when the base station allocates the RNTI randomly, it can greatly reduce the possibility of an attacker tracking the RNTI to identify the user. However, attackers can also identify users through the mapping relationship between TMSI and RNTI. Therefore, the base station can also apply the principle of random allocation to TMSI, which also makes the mapping relationship between TMSI and RNTI non-existent.
2.2 User Data Manipulation Attacks
2.2.1 Redirection attack
The air interface protocol of LTE only has encryption protection for user plane data above the PDCP sublayer, but there is no integrity protection. Therefore, an attacker can obtain the encrypted payload of user plane data by establishing a relay station between the terminal and the base station. Some literature shows that: [4] Intercept the data packet forwarded to the target IP address through the relay station, distinguish the data packet from other payloads, and apply the manipulation mask to change the target IP address to a malicious IP address, so as to achieve the request The purpose of detouring to a malicious server instead of the original DNS originator. However, other data packets are transmitted to the target IP address intact, and a decoding method is obtained, so that the data packets transmitted to the malicious IP address are decoded to obtain user privacy information. [5] The oracle machine is established by using the reflection mechanism of the IP layer, thereby improving the process of decryption and encryption, making redirection attacks more applicable to actual scenarios. The attacker passed the characteristics of the uplink allowing the establishment of any IP connection to the network and the downlink establishing a TCP connection to the terminal, and established an oracle machine to solve the problem of occasional confusion of encrypted and decrypted symbols.
2.2.2 Solutions
The root cause of the redirection attack is that there is no integrity protection for the user plane data above the PDCP sublayer, and the attacker can reuse the key stream for decryption and encryption. Therefore, the existence of this attack can be solved by solving the reuse of the key stream, and this solution is also proposed in the protocol: "In order to avoid the reuse of the key stream, the base station can use different radio bearer identifiers to apply to consecutive radio bearer It can also trigger handover within the cell, or trigger transition from RRC connection to RRC idle or non-idle state and finally back to RRC connection.” [6] also carefully analyzed the evaluation of this solution in different scenarios.
2.3 Fingerprint Attack
User plane data below the PDCP sublayer does not have encryption protection. Therefore, side channel traffic information can be used to obtain user traffic information, such as PDCP packet length. The packet length of PDCP will not be changed after receiving encryption, so the inherent transmission of specific services and specific websites allows attackers to identify the ongoing services of the websites and services accessed by users through the PDCP packet length. Therefore, fingerprinting attacks can be subdivided into website fingerprinting attacks and business fingerprinting attacks.
2.3.1 Website fingerprinting attack
Attackers use software radios such as USRP to eavesdrop on target users, obtain relevant transmission data, and then obtain the length of PDCP packets transmitted by them, and finally use advanced machine learning tools such as support vector machines, random forests, and decision trees to analyze the data. Identify, thereby identifying the website data that the target user is visiting, so as to spy on the user's privacy. [7] proved the feasibility of this attack in a network built with the help of a laboratory and a commercial network.
2.3.2 Service fingerprint attack
Similar to the website fingerprint attack method, the attacker can also obtain the PDCP packet length of a certain service performed by the user, and perform specific identification through some algorithms. [8] Obtained the PDCP packet length of different applications of the user through the srsLTE network in the laboratory environment, and extracted 60 features for machine learning, and had considerable accuracy, proving the feasibility of the attack. Since the application program can be identified through this attack, the user's mobile phone brand and business can also be identified accordingly.
2.3.3 Solutions
Fingerprint attacks can be implemented by obfuscating traffic characteristics. [7] reduces the success rate of fingerprint attack to about 53% by blurring the application layer, which effectively reduces the accuracy rate of fingerprint attack.
references
[1]Jover R P. LTE security, protocol exploits and location tracking experimentation with low-cost software radio[J]. arXiv preprint arXiv:1607.05171, 2016.
[2]Forsberg D, Leping H, Tsuyoshi K, et al. Enhancing security and privacy in 3GPP E-UTRAN radio interface[C]//2007 IEEE 18th International Symposium on Personal, Indoor and Mobile Radio Communications. IEEE, 2007: 1 -5.
[3]Attanasio G, Fiandrino C, Fiore M, et al. Characterizing RNTI Allocation and Management in Mobile Networks[C]//Proceedings of the 24th International ACM Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems. 2021: 189 -197.
[4]Rupprecht D, Kohls K, Holz T, et al. Breaking LTE on layer two[C]//2019 IEEE Symposium on Security and Privacy (SP). IEEE, 2019: 1121-1136.
[5]Rupprecht D, Kohls K, Holz T, et al. IMP4GT: IMPersonation Attacks in 4G NeTworks[C]//NDSS. 2020.
[6]Rupprecht D, Kohls K, Holz T, et al. Call Me Maybe: Eavesdropping Encrypted {LTE} Calls With {ReVoLTE}[C]//29th USENIX security symposium (USENIX security 20). 2020: 73-88.
[7]Kohls K, Rupprecht D, Holz T, et al. Lost traffic encryption: fingerprinting LTE/4G traffic on layer two[C]//Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks. 2019: 249 -260.
[8]Zhai L, Qiao Z, Wang Z, et al. Identify What You are Doing: Smartphone Apps Fingerprinting on Cellular Network Traffic[C]//2021 IEEE Symposium on Computers and Communications (ISCC). IEEE, 2021: 1- 7.