The interviewer asked how HTTPS was transferred from HTTP, I was a little confused

After all, this time is also the golden season for the
"Golden Nine, Silver and Ten" interviews. Of course Ah Fan also wants
to go to the interview, but because of her own limitations, she can only
interview the students who went out for the interview to ask what content, one
of them, Ah Fan feels it is necessary to share with you, that is, to ask about the
content of HTTP.

After all, this time is also the golden season for the
"Golden Nine, Silver and Ten" interviews. Of course Ah Fan also wants
to go to the interview, but because of her own limitations, she can only
interview the students who went out for the interview to ask what content, one
of them, Ah Fan feels it is necessary to share with you, that is, to ask about
the content of HTTP.
HTTP
HTTP protocol is the abbreviation of Hyper Text Transfer
Protocol (Hyper Text Transfer Protocol), which is a transfer protocol used to
transfer hypertext from a World Wide Web server to a local browser. HTTP is
based on the TCP/IP protocol communication protocol to transfer data (HTML
files, picture files, query results, etc.). It does not involve packet transmission,
and mainly specifies the communication format between the client and the
server, and port 80 is used by default.
This is actually the simplified content in Baidu
Encyclopedia. Although it is not too detailed, it is already a general
description of HTTP. Let's take a look at this HTTP from the following aspects.
We won’t explain more about HTTP message and body from here.
A fan has explained it to you completely before, including the evolution
history of HTTP. Today, A fan, let’s talk about the relationship between HTTP
and HTTPS.
HTTP disadvantages
As we all know, there are a lot of advantages of HTTP:
Simple, flexible and easy to expand
Wide application and mature environment
Stateless (no additional resources are required to record
state information)
But the shortcomings of HTTP are also very significant. Why
do you say that HTTP uses plaintext for transmission. Although it is convenient
for our debugging, the information will be exposed, and there is no privacy in
every link.
And in our perception, HTTP is insecure. The first reason is
the plaintext mentioned above, and the other is that HTTP does not verify the
identity of the communicating parties, so the identity of the other party may
be disguised, just like some public places. Those public WIFI, and HTTP cannot
verify the integrity of the message, so the message may also be tampered with.
Based on these contents, we often choose HTTP more
carefully, otherwise when you transmit content, others can easily analyze the
content you want to transmit by using a packet capture tool.
At this time, we thought of one thing. Wouldn't it be enough
to encrypt it?
Yes, there is no problem at all. HTTP does not have an
encryption mechanism, but we can find a way to deal with it. This way is:
SSL or TLS
SSL: Secure Socket Layer
TLS: Security Layer Transport Protocol
When they are used in combination, the content of HTTP
communication can be encrypted, and communication can be carried out on this
line at this time. The combined use of HTTP through SSL is called HTTPS or HTTP
overSSL.
HTTPS
In the vernacular, HTTP is HTTPS after encryption,
authentication, and integrity protection.
The easiest way to distinguish HTTPS is to see a small lock
logo when you visit in the browser.
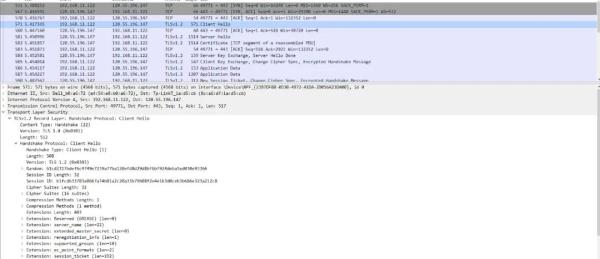
Don’t over 90% of the websites now use HTTPS?
Let's use a packet capture tool to look at the transmission
content of HTTPS and try.
We saw the TLS version and the random number that Afan did
not have on the screenshot.
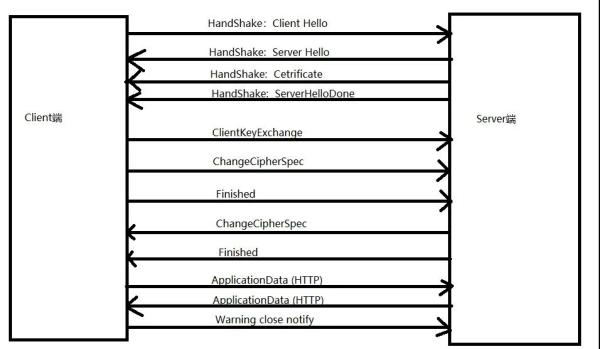
At this time we have to fully analyze the HTTPS secure
communication mechanism. Take a look at a picture and then we will use our
packet capture tool for analysis.
上面這是
HTTPS 的安全通信的機制,我們分別來看看都乾了什麼。
The first step: Client Hello
The client starts the SSL/TSL communication by sending a Client Hello message. It contains a series of contents such as the version of SSL/TSL, the encryption method used and so on.
Step 2: Server Hello
The server determines the SSL/TLS protocol version used by
comparing it with its own version according to the supported SSL/TLS protocol
version sent by the client. Disadvantages such as the masked algorithm.
Step 3: The server sends a Certificate message, which
contains the public key certificate.
The purpose of the certificate is actually to ensure the
identity of the logo, and the certificate generally adopts the X.509 standard.
Step 4: Server Key Exchange
The server sends a Server Hello Done message to request the
client, and the first phase of the SSL/TSL handshake negotiation part ends.
There are also many people who are accustomed to saying that
the fourth step is Server Hello Done. In fact, when we captured the packet, we
found that they were in a request. Let's take a look at the packet and try it
later. Server Hello Done is actually equivalent to telling you that I have
finished sending it here.
Step 5: Client Key Exchange
After completing the first handshake of SSL/TSL, the client
sends a Client Key Exchange message as a response, which is actually to
exchange secret key parameters.
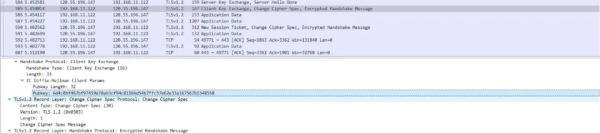
Here, the client will generate a random number again, and
then use the public key from the server to encrypt it to get the ciphertext
PreMaster Key. After the server receives this value, it uses the private key to
decrypt it, so that the secret keys on both sides can be negotiated. Later data
transmission can be encrypted and decrypted with the negotiated secret key.
Step 6: Change Cipher Spec
The client sends a Change Cipher Spec message, prompting the
server to change the encoding, which means that when we send messages in the
future, I use the key we defined before for encryption.
Step 7: Client Finished
The client generates a summary of the previous handshake
message and then encrypts it with the negotiated secret key. This is the first
encrypted message sent by the client. This step is also a more critical step.
The success of this operation depends on whether the server is successful. The
message can be successfully decrypted this time as a basis for judgment.
Step 8: The server sends Change Cipher Spec
Step 9: The server sends the Server Finished message
In fact, the function is similar to Client.
Step 10: The Finished exchange between the server and the
client is completed. At this time, the SSL/TSL connection is OK, and the
message sent is completely called HTTPS.
The last is the content of data transmission.
Since HTTPS is safe, why not use it widely?
In fact, encrypted communication protects the privacy of
data to a certain extent, but the efficiency is relatively low. Every
communication must be encrypted, which consumes resources. If it contains some
money, then encrypted communication must be used, and the main certificate must
be charged. Ah.
If you want to use it, you definitely need a certificate. Just like when you are doing WeChat payment, don't you also need to buy a certificate. Generally, it costs hundreds of dollars a year. So do you know the relationship between HTTP and HTTPS?