Istio configuration security: How to avoid misconfiguration

Istio is a powerful service mesh solution that provides zero-trust security, observability, and advanced traffic management without code changes. However, we often encounter unexpected behaviors due to misconfiguration. This article introduces several common Istio configuration errors, explains the principles behind them, and shows how to identify and resolve these problems through diagrams. We also introduce TIS Config Analyzer[1], a tool provided by Tetrate, which is a tool for optimizing Istio operational efficiency and security.
Cases of accidents caused by configuration errors
The following are two typical cases of accidents caused by configuration errors:
- 1. Amazon Web Services outage in 2017[2]: A simple typo led to a widespread service outage that affected thousands of online services and applications, highlighting how even in mature cloud infrastructure, a small configuration error can have serious consequences.
- 2. GitLab’s data loss incident in 2017[3]: Due to a configuration error, GitLab accidentally deleted a large amount of production data during database maintenance. Although the backup mechanism was configured well, the incorrect configuration prevented the timely recovery of the data.
These cases demonstrate that proper configuration management is critical to preventing service disruptions and data loss.
Common types of Istio configuration errors
Istio configuration errors can be divided into the following categories:
1. AuthorizationPolicy: namespace does not exist, only HTTP methods and fully qualified gRPC names are allowed, host has no matching service registry entry, field requires mTLS to be enabled, service account not found, etc.
2. DestinationRule: Multiple destination rules for the same host subset combination, the host has no matching entry in the service registry, the subset tag is not found in any matching host, etc.
3. Gateway: Multiple gateways for the same host-port combination, the gateway selector did not find a matching workload in the namespace, etc.
4. Port: The port name must follow a specific format, the port's application protocol must follow a specific format, etc.
5. Service: No deployment was found that exposes the same port as the service.
6. VirtualService: The route with the target weight has no valid service, points to a virtual service that does not exist in the gateway, etc.
Examples of common Istio configuration errors
In daily use of Istio, the following are some of the most common configuration errors:
1. The virtual service points to a non-existent gateway:
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: details
namespace: bookinfo
spec:
hosts:
- details
gateways:
- non-existent-gateway- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
In this case, the details virtual service attempts to route through a non-existent-gateway, causing traffic management to fail.
2. The virtual service references a non-existent service subset:
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: details
namespace: bookinfo
spec:
hosts:
- details- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
If the details service does not define a corresponding subset, the request will be rejected because the correct service instance cannot be found.
3. The gateway could not find the specified server credentials:
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: cert-not-found-gateway
namespace: bookinfo
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 443
name: https
protocol: HTTPS
tls:
mode: SIMPLE
credentialName: "not-exist"- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
This causes the TLS handshake to fail because the specified certificate not-exist does not exist.
Configuration Validation
In order to reduce the risk of service interruption due to configuration errors, configuration verification becomes an indispensable step. Configuration verification can be divided into the following two types:
• Static configuration validation: Validates the configuration before it is applied to the system. This includes checking for syntax errors, completeness, and validity of configuration items.
• On-demand configuration validation: Validation occurs when the configuration has already been applied but may need to be adjusted based on real-time data. This type of validation helps adapt to changes in a dynamic environment and ensures the continued correctness of the configuration.
Recommended Configuration Validation Tools
istioctl validate
istioctl validate is used to validate the syntax and basic structure of Istio configuration files (such as YAML files) to ensure that the configuration files comply with the Istio API specifications. It can detect syntax errors and format problems before the configuration is applied to the cluster. It is a static analysis tool that is usually used in conjunction with the CI process to prevent invalid configuration files from being applied to the cluster.
istioctl analyze
istioctl analyze[4] is a powerful diagnostic tool for analyzing the running status and configuration consistency of an Istio cluster. It not only checks the syntax of the configuration file, but also checks the configuration actually applied in the cluster to identify potential problems and conflicts. istioctl analyze provides dynamic analysis capabilities that can identify configuration errors and potential problems during cluster runtime.
The configuration process of istioctl analyze is as follows:
1. Collect configuration data: First, istioctl analyze collects Istio configuration data from specified sources. These sources can be active Kubernetes clusters or local configuration files.
2. Parsing and building models: The tool parses the collected configuration data and builds a model that internally represents the Istio configuration.
3. Apply analysis rules: It then applies a series of predefined rules to analyze the model and detect potential configuration issues. These rules cover a variety of potential issues ranging from security vulnerabilities to performance issues.
4. Generate report: After the analysis is complete, istioctl analyze outputs a detailed report containing all the problems found. If no problems are found, it will inform the user that the configuration seems to be fine.
The following is a flowchart of the istioctl analyze workflow:
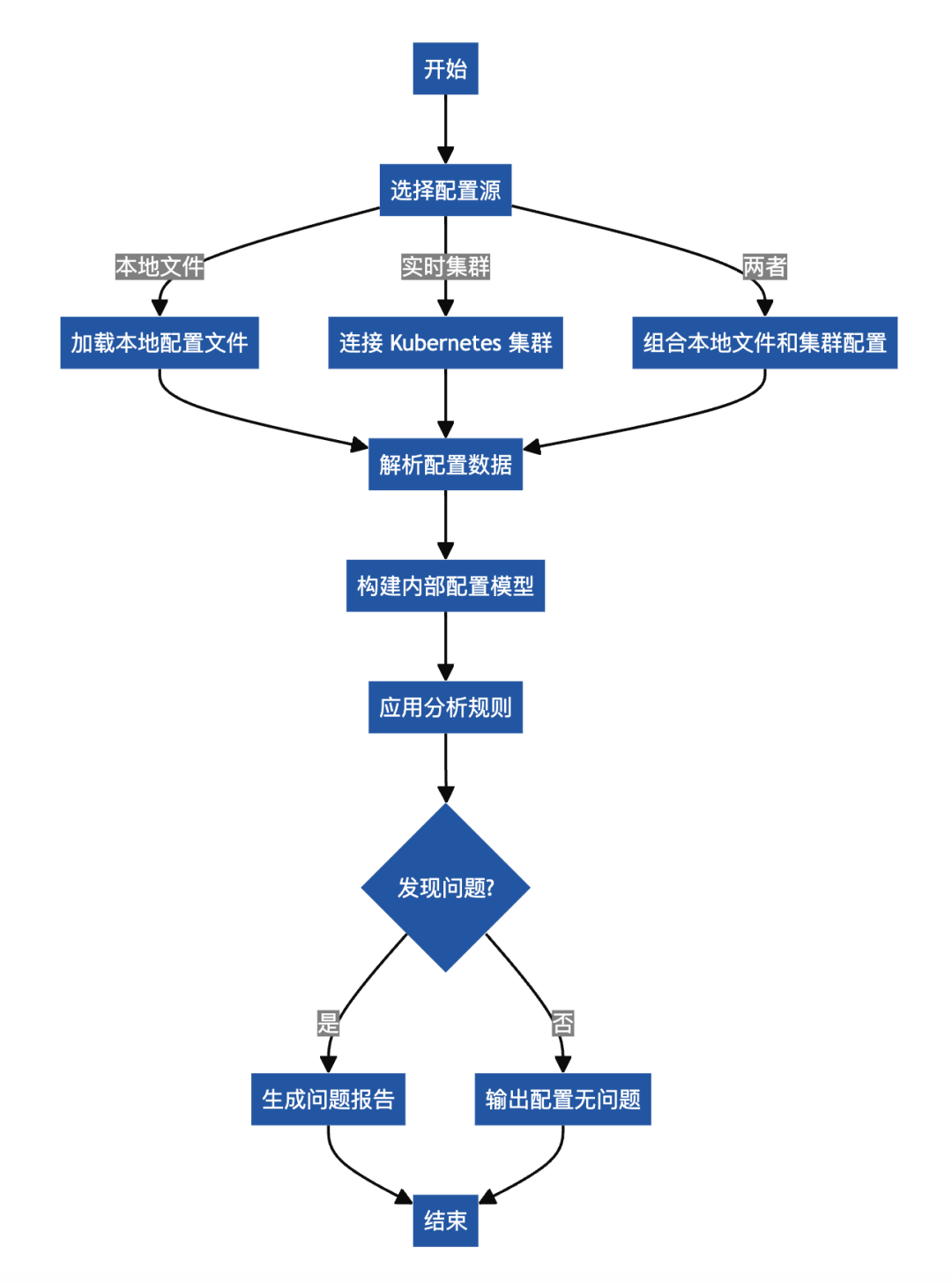 Workflow of istioctl analyze
Workflow of istioctl analyze
Kiali
Kiali[5] is an important tool for managing and visualizing the Istio service mesh, providing real-time insights into the mesh’s health, performance, and configuration status. By integrating Kiali into the Istio environment, configuration security can be enhanced in the following ways:
• Visualization: Kiali provides a graphical representation of the service mesh, making it easier to spot configuration errors, such as routing errors or missing policies.
• Validation: Helps validate the Istio configuration, highlighting issues like misconfigured gateway or destination rules before they cause trouble.
• Security Insights: Kiali provides visibility into security policies, ensuring that mTLS and authorization settings are properly enforced.
Combining Kiali with tools such as istioctl validate and istioctl analyze ensures a more robust approach to preventing and resolving Istio configuration errors, thereby improving the security and efficiency of your service mesh.
Introduction to the Config Analyzer tool in Tetrate's TIS
To help developers and operators avoid common configuration errors, Tetrate developed the Config Analyzer[6] tool in the TIS Dashboard. This tool can automatically verify the Istio configuration, analyze the configuration issues of the service mesh according to best practices, and provide optimization suggestions. Config Analyzer can automatically detect configuration issues in the Istio service mesh, provide explanations and solutions, and support on-demand detection of configuration errors.
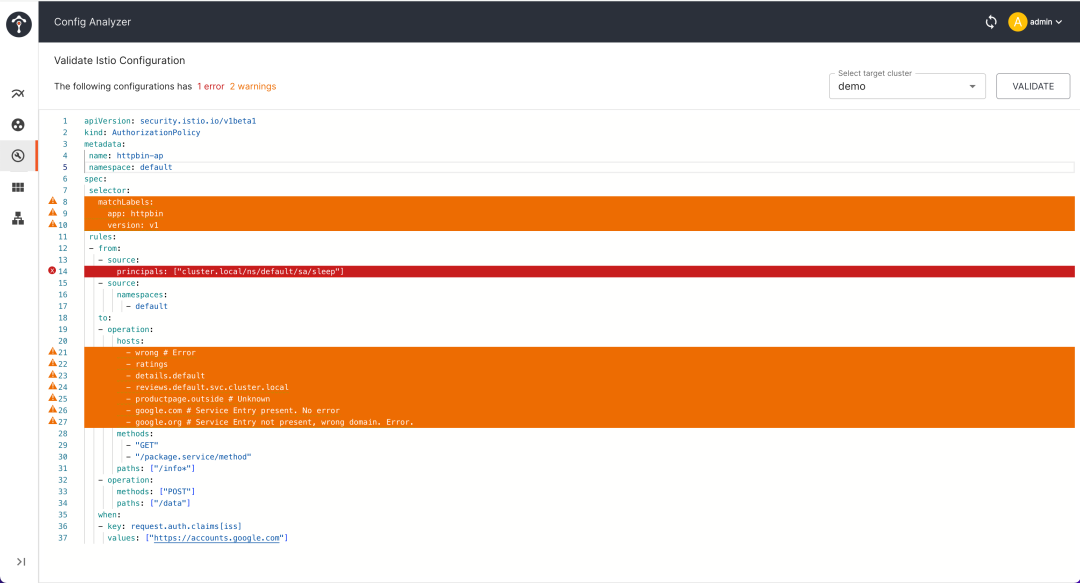 picture
picture
TIS Config Analyzer can detect problems in your configuration on demand.
Summarize
Properly configuring Istio is key to ensuring the health of your service mesh. By understanding and avoiding common configuration errors, and leveraging advanced tools such as Tetrate's TIS Config Analyzer, you can ensure the stability and security of your Istio environment. Remember, a small configuration error can cause the entire service mesh to fail, so continuous monitoring and auditing of configurations is essential.
refer to
• Validation - kiali.io[7]
Reference Links
[1] TIS Config Analyzer: https://docs.tetrate.io/istio-subscription/dashboard/analyzers/config
[2] Amazon Web Services 2017 outage incident: https://www.theverge.com/2017/3/2/14792442/amazon-s3-outage-cause-typo-internet-server
[3] GitLab 2017 data loss incident: https://about.gitlab.com/blog/2017/02/01/gitlab-dot-com-database-incident/
[4] istioctl analyze: https://istio.io/latest/docs/ops/diagnostic-tools/istioctl-analyze/
[5] Kiali: https://kiali.io
[6] Config Analyzer: https://docs.tetrate.io/istio-subscription/dashboard/analyzers/config
[7] Validation - kiali.io: https://kiali.io/docs/features/validations/