Nintendo blitzes GitHub, deleting more than 8,000 emulator code repositories overnight

Nintendo Blitzes GitHub! 8535 code bases were removed overnight .
As long as it contains the Yuzu Switch emulator code , it is said to have illegally bypassed Nintendo's technical protection measures and run illegal pirated Switch games.

GitHub also responded.
Developers haveThe infringing content may be deleted or changed at any time. In addition, GitHub provides developers with legal resources and guidance on how to submit a DMCA (a U.S. copyright law) counter-notification.
As soon as this incident came out, netizens also exploded, with voices supporting Nintendo and Yuzu.
Some netizens suggested not to make any noise:
Let’s vote with our wallets!
Some netizens thought they were deleting all Nintendo emulators:
Fortunately it's only related to Yuzu.
"Reported content must be deleted"
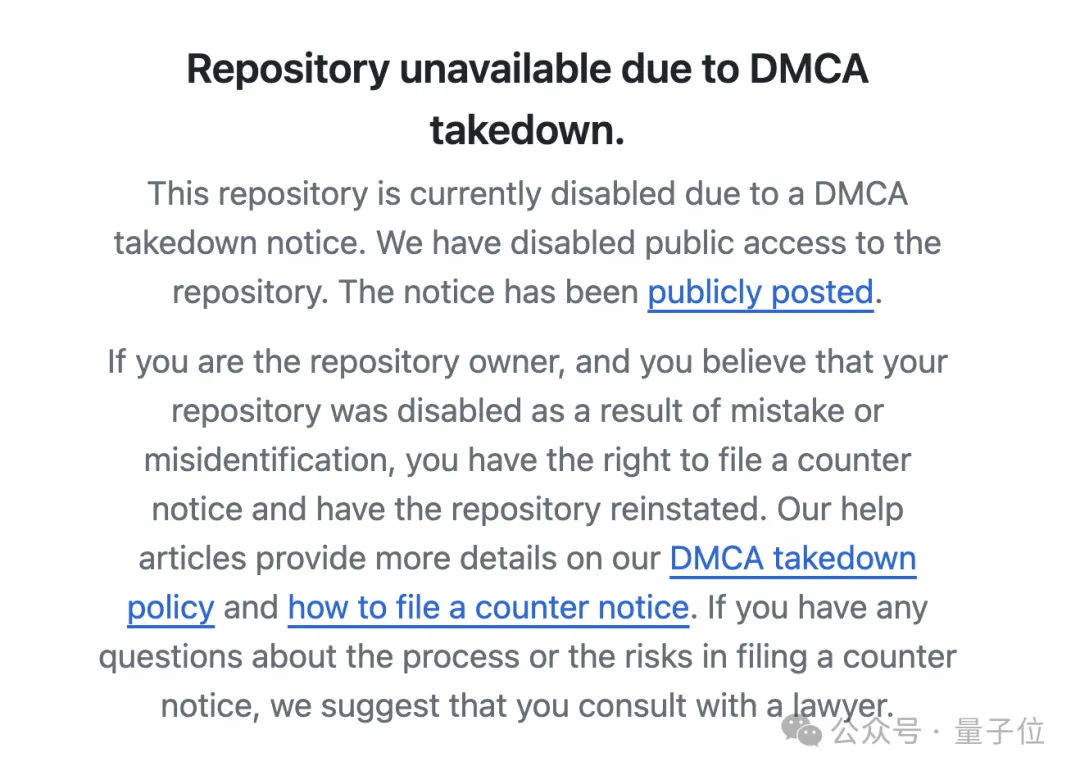
Currently, when you open the Yuzu-related warehouse again, the warehouse is already disabled.
Also noted below: If you are the owner of this repository and believe that the repository has been disabled due to mistake or misidentification, you have the right to submit a counter-notification to have the repository reinstated.
The following is part of the conversation between Nintendo's agent responsible for the incident and GitHub.
Q: Please provide a detailed description of the original copyrighted work that is allegedly infringed. If possible, please provide the URL of the online publishing location.
A: The Nintendo Switch game console and electronic games contain technical protection measures (TPMs) that allow the Nintendo Switch game console to only interact with genuine Nintendo electronic game files.
This process protects Nintendo's copyrighted video games, including but not limited to U.S. Copyright Registration Numbers PA0002213509 (Super Mario Maker 2) , PA0002233840 (Assemble! Animal Crossing) , PA0002213908 (Luigi's Mansion 3) , and PA0002028142 (Sel Legend of the Wild: Breath of the Wild) .
These measures prevent users from playing pirated Nintendo games on the Nintendo Switch console and prevent users from illegally copying and playing Nintendo games on unauthorized devices.
Q: Do you claim to have any technical measures in place to control access to your copyrighted content? If you're unsure, please review our Anti-Circumvention Technology Complaints.
A: Yes.
Q: What technical measures have you taken and how effectively do they control access to your copyrighted materials?
A: Nintendo has embedded technical protection measures (TPM) in the Switch console and game files , including encryption of game files, which requires specific encryption keys (such as prod.keys) to authenticate, access and run each game on the Switch. game.
The Switch console supports physical cartridges and digital games downloaded from Nintendo servers. Both formats are protected by Nintendo's TPM, which includes encryption of the games. When a game is launched on the Switch, it is decrypted and authenticated using Nintendo's encryption key so players can play.
Nintendo owns or exclusively controls a large number of software and game copyrights, and the operation of TPM can prevent illegal access and copying. During normal operations, TPM needs to access its copyrighted works with the authorization of Nintendo based on relevant information and procedures to effectively control the access and copying of its copyrighted works.
Q: How were the accused projects designed to circumvent your technical protection measures?
A: The repository in the report provides the Yuzu emulator or its code. The Yuzu emulator is mainly used to run Nintendo Switch games.
Specifically, Yuzu illegally bypassed Nintendo's technical protection measures to run pirated Nintendo Switch games. Nintendo Switch games are encrypted using proprietary encryption keys (prod.keys) to prevent unauthorized access and copying.
In its operations, Yuzu used unauthorized copies of these encryption keys to decrypt pirated Switch games or ROMs at or before runtime. Yuzu constituted an act of illegal "trafficking technology mainly used to circumvent technical measures" and violated Article 1201 of the DMCA .
Q: Have you searched for any derivative versions of the allegedly infringing files or repositories? Each derived version is an independent repository and must be individually identified if you believe it is infringing and wish to have it removed.
A: Yes. Based on the number of representatives of the derived repositories I reviewed, I believe that all or most of the derived repositories are infringing to the same extent as the parent repository .
Q: What is the best solution to the alleged infringement?
A: The reported content must be deleted .
Yuzu developers were also sued not long ago
Let’s briefly introduce Yuzu.
Launched in 2018, Yuzu is free and open source software for Windows, Linux and Android.
It can run a large number of copyright-protected Switch games, including popular games "The Legend of Zelda: Breath of the Wild", "Tears of the Kingdom", "Super Mario: Odyssey", "Super Mario: Spectacle", etc.
Yuzu, while it may have some bugs in different games, can generally run games at higher resolutions than the Switch and deliver better frame rates, as long as your hardware is powerful enough.
On Reddit, netizens once believed that Yuzu’s performance was better than other Switch emulators.
Naturally, this also caught Nintendo's attention.
In fact, Nintendo just sued Yuzu Switch emulator developer Tropic Haze two months ago .
According to engadget news, the two parties reconciled in just one week. requirement is:
Tropic Haze must pay $2.4 million in compensation and must permanently cease activities related to providing, marketing, distributing or selling Yuzu emulators or any similar software that circumvents Nintendo's technical protection measures; it must also remove all circumvention devices, tools and Nintendo's in the emulators Encryption keys, and handing over all circumvention devices and modified Nintendo hardware; even the emulator's network domain must be turned over to Nintendo.
However, at that time, everyone also discussed that Yuzu was unlikely to disappear completely, after all, the entire code base can be found on GitHub.

Rango... I didn't expect the attack on GitHub to come so quickly.