Let's talk about virtual mobile cybersecurity

1. Introduction
With the rise of 5G technology, virtual mobile networks (VMNs) are becoming an important part of the modern communications landscape, bringing unprecedented flexibility and efficiency to mobile communications. However, with the widespread adoption of these innovative technologies, we are also facing new challenges, one of which stands out is virtual mobile network security. Emerging technologies such as virtualization, software-defined networking (SDN), and network slicing in VMNs not only bring a high degree of flexibility, but also raise concerns about new aspects of data and communication security.
This article will introduce the key issues facing VMNS network security, identify the threats faced in modern communication infrastructure, and propose strategies and innovations to address these challenges, which will lead you to an in-depth understanding of the core issues of VMNS network security and how to deal with them.
General overview
Virtual mobile networks (VMNs) enable telecommunications network-as-a-service (TaaS) by leveraging cloud computing, network functions virtualization (NFV), and software-defined networking (SDN) to efficiently deploy network functions and scale resources when needed, providing a unified platform for network management. As shown in the figure, by leveraging network and virtualization technologies, a slice, such as a vehicle-to-everything (V2X) experimental slice, can be generated to provide diverse services on the same shared infrastructure.
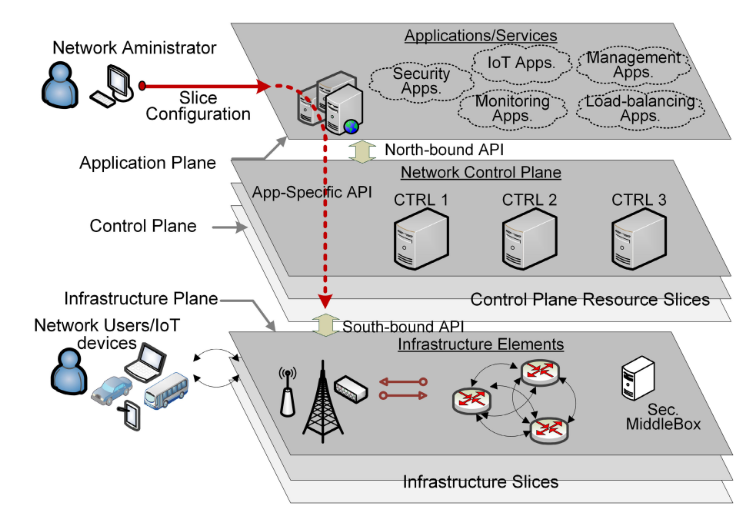 Figure SDN-enabled slicing and security feature layout
Figure SDN-enabled slicing and security feature layout
Therefore, the security of VMNs will depend on the security of SDN, cloud platforms, and most importantly, NFV, virtualization technology. The virtualization of communication networks allows us to deploy multiple services on the same physical infrastructure. Virtualization enables a common commodity system to run one or more different virtual network functions (VNFs). Network functions virtualization (NFV), the implementation of network functions through software for deployment on common network devices, has led to the rise of virtual network functions (VNFs) [1]. NFV has since become an important technology for 5G and post-5G networks [2]. In the future, new verticals will span multiple carrier environments to deliver new services such as e-health, smart home, and vehicle-to-vehicle communications.
Software-defined networking (SDN) is one of the main enabling technologies for VMNs because of its ability to provide an abstraction of the physical network infrastructure [3]. SDN separates network control from data forwarding elements, introduces network programmability, and logically centralizes network control to a central location for management of the entire network. These features make the network more robust, simplify network management, and minimize operational expenses. However, these features also open the door to new security vulnerabilities and challenges. SDN and NFV are highly complementary because they provide great convenience to NFV in terms of the deployment of VNFs while providing support in the network infrastructure [4]. Since all of these technologies are highly interrelated and interdependent, in this subsection we will discuss the security challenges faced and their possible solutions.
2. NFV security challenges
In virtual mobile networks (VMNs), the security challenges of network functions virtualization (NFV) are focused on hypervisors, virtual machines (VMs), and virtual network functions (VNFs). The concept of virtualization threats has recently emerged, and the availability, integrity, and confidentiality of both hardware and software in a VMN can be compromised. In VMNs, a hypervisor is a central entity responsible for creating virtual instances on hardware. Security threats can stem from security weaknesses in software implementations, VNF configurations, hypervisors, and cloud platforms, as well as direct attacks on VNFs, such as side-channel attacks, flood attacks, and malware injections [5].
Due to the dynamic nature of virtual network functions (VNFs), trust management is another serious concern. Because VNFs are able to move between multiple networks and are supported by cloud platforms maintained by different owners and operators[5], they can be targeted for attacks. The targets of such attacks include user traffic, VNF code and policy input, and the state of the VNF. Attackers may exploit the inherent limitations of the operating environment, including its software and hardware[6], to carry out these attacks. In addition, if a standard interface is not defined, it may face more serious security challenges [7].
Security solutions for NFV
Similar to centralized or core network elements, securing a hypervisor NFV must be through appropriate authentication, authorization, and accountability mechanisms, and security mechanisms must be in place to ensure availability. Security verification checks on VNF packages can prevent the introduction of security vulnerabilities throughout the system. As a result, there are multiple proposals to conduct confidentiality checks for VNF packets with proper authentication and integrity verification for inclusion in NFV systems. There are other proposals to protect the system from malicious VNFs. For example, the authors in Ref. [8] propose and demonstrate a verification system that uses the standard TOSCA [9] data model to protect different VNF security attributes of NFV infrastructure (NFVI).
3. Network slicing security challenges
Network slicing brings innovation to mobile communications by enabling resource sharing in 5G networks, but it also brings new challenges to security and privacy protection. Because slicing is a new concept for mobile networks, design and implementation errors similar to those of service-based architecture (SBA) can occur. In the lifecycle management of slices, slice templates, slice configuration APIs, and user data processing can all be targeted. When slices run, they can be exposed to risks such as denial-of-service (DoS) attacks, performance attacks, data breaches, and privacy violations. Potential attack points cover user devices, service interfaces, sub-slices, slice managers, network functions, and various network resources involved in network slicing. The inter-slice communication scenario also brings additional security risks to the network [10]. In addition, new network functional areas, such as slice management, slice isolation, security differentiation between slices, and the interaction between the Evolved Packet Core (EPC) and the 5G Core Network (5GC) during the slicing process, are also facing potential mobile network security threats [11].
Network slicing security solutions
In order to provide consistent and efficient security for all 5G network slices, special attention should be paid to methods and technologies that ensure end-to-end slice security, slice isolation, and slice resource management and orchestration. For different slicing scenarios, new trust models need to be developed to facilitate resource sharing among various actors and networks participating in slicing [10]. At the same time, it is necessary to establish a strong isolation mechanism, because a strong isolation mechanism can minimize the impact of one malicious slice on other slices and the hypervisor [12]. By actively monitoring network traffic, identifying suspicious and malicious activities in a timely manner, and leveraging the SDN concept to stop inbound traffic, the security of different slices in the network can be improved.
4. Security challenges of software-defined networking
The separation of the data plane from the control plane, centralized control, and network programmability (via programmable APIs) pose security challenges for SDN [13]. For example, an attacker might use interplane communication channels to disguise one plane and launch an attack on another. In addition, it is a potential target for DOS and resource exhaustion attacks due to the presence of centralized controllers, which has been demonstrated by fingerprinting the timestamp [14] or round-trip time [15] of real-time packets in the network. As a result, attacks against network control points in SDN are relatively easy to implement. In addition, SDN allows applications to program or change the characteristics of network behavior, which may give malicious programs the opportunity to surreptitiously manipulate network resources, such as redirecting traffic to botnets or hackers or stealing user traffic. In virtual mobile networks (VMNs), malware that is able to manipulate the network is more threatening because it is more difficult to find malware.
Solutions for software-defined networking
To protect your network from SDN attacks, you first need to overcome the weaknesses of traditional SDN architectures. For example, by logically centralizing but physically decentralizing network control, it is possible to prevent resource exhaustion attacks and ensure that network control points remain always available in the data plane [16]. To achieve this resilience, a variety of strategies can be employed, including disaggregating controller functions such as implementing local decision-making [17], adopting hierarchical controllers [18], increasing and increasing resource capacity, and leveraging intelligent security systems equipped with machine learning (ML) to take proactive preventive action before attacks reach cyber vulnerabilities [12].
In addition, SDN can be used to improve the security of virtual networks [19]. By utilizing SDN's virtual machine (VM) migration technology, resources can be moved to a secure zone. For example, in the face of DoS attacks, VM migrations can be performed efficiently in real-time by monitoring the load status in the SDN forwarding plane, such as packet counter values in the flow table, improving scalability. Compared with traditional networks, SDN successfully solves the challenges of unpredictable network status and limited VM migration to local area networks (LANs) faced by real-time VM migration through programmable APIs that program real-time networks on a centralized control platform and are independent of the layered IP protocol stack. Therefore, strengthening the resilience of SDN can help improve the security of virtual mobile networks (VMNs) [13].
5. Summary
This article delves into the key security issues of virtual mobile networks (VMNs), with a particular focus on the cybersecurity challenges posed by emerging technologies such as 5G, Network Functions Virtualization (NFV), software-defined networking (SDN), and network slicing. The introduction of 5G has enabled VMNs to share physical infrastructure more flexibly, but it has also introduced new security concerns, such as the surge in flash network traffic, the security of wireless interfaces, and the integrity of user planes. The application of network slicing facilitates resource sharing, and the application of NFV and SDN provides greater flexibility to the network, but they make VMNs more complex and bring new security threats.
The article also explores security solutions to address these challenges, including protection against NFV, end-to-end security assurance for network slicing, and attack prevention measures in SDN. The importance of proper authentication, authorization, accountability mechanisms, and security verification checks was emphasized, and measures such as distributed control, resource addition, and machine learning in SDN were pointed out to improve the resilience and security of the overall network.
summary
[1]B. Yi, X. Wang, S. K. Das, K. Li, and M. Huang, ''A comprehensive survey of network function virtualization,'' Comput. Netw., vol. 133, pp. 212–262, Mar. 2018.
[2] F. Z. Yousaf, M. Bredel, S. Schaller, and F. Schneider, ''NFV and SDN— Key technology enablers for 5G networks,'' IEEE J. Sel. Areas Commun., vol. 35, no. 11, pp. 2468–2478, Nov. 2017.
[3] G. Biczok, M. Dramitinos, L. Toka, P. E. Heegaard, and H. Lonsethagen, ''Manufactured by software: SDN-enabled multi-operator composite services with the 5G exchange,'' IEEE Commun. Mag., vol. 55, no. 4, pp. 80–86, Apr. 2017.
[4] J. Matias, J. Garay, N. Toledo, J. Unzilla, and E. Jacob, ''Toward an SDN-enabled NFV architecture,'' IEEE Commun. Mag., vol. 53, no. 4, pp. 187–193, Jan. 2015.
[5] I. Ahmad, T. Kumar, M. Liyanage, J. Okwuibe, M. Ylianttila, and A. Gurtov, ''Overview of 5G security challenges and solutions,'' IEEE Commun. Standards Mag., vol. 2, no. 1, pp. 36–43, Mar. 2018.
[6] E. Marku, G. Biczok, and C. Boyd, ''Towards protected VNFs for multioperator service delivery,'' in Proc. IEEE Conf. Netw. Softw. (NetSoft), Jun. 2019, pp. 19–23.
[7] W. Yang and C. Fung, ''A survey on security in network functions virtualization,'' in Proc. IEEE NetSoft Conf. Workshops (NetSoft), Jun. 2016, pp. 15–19.
[8] M. Pattaranantakul, Y. Tseng, R. He, Z. Zhang, and A. Meddahi, ''A first step towards security extension for NFV orchestrator,'' in Proc. ACM Int. Workshop Secur. Softw. Defined Netw. Netw. Function Virtualization, New York, NY, USA, Mar. 2017, p. 25.
[9] Tosca Simple Profile for Network Functions Virtualization (NFV) Version 1.0, TOSCA, Atlanta, GA, USA, 2015.
[10] R. F. Olimid and G. Nencioni, ''5G network slicing: A security overview,''IEEE Access, vol. 8, pp. 99999–100009, 2020.
[11] J. Cao, M. Ma, H. Li, R. Ma, Y. Sun, P. Yu, and L. Xiong, ''A survey on security aspects for 3GPP 5G networks,'' IEEE Commun. Surveys Tuts., vol. 22, no. 1, pp. 170–195, 1st Quart., 2020.
[12] M. Liyanage, I. Ahmad, A. B. Abro, A. Gurtov, and M. Ylianttila,A Comprehensive Guide to 5G Security. Hoboken, NJ, USA: Wiley, 2018.
[13] I. Ahmad, S. Namal, M. Ylianttila, and A. Gurtov, ''Security in software defined networks: A survey,'' IEEE Commun. Surveys Tuts., vol. 17, no. 4, pp. 2317–2346, 4th Quart., 2015.
[14] A. Azzouni, O. Braham, T. M. Trang Nguyen, G. Pujolle, and R. Boutaba, ''Fingerprinting OpenFlow controllers: The first step to attack an SDN control plane,'' in Proc. IEEE Global Commun. Conf. (GLOBECOM), Dec. 2016, pp. 1–6.
[15] H. Cui, G. O. Karame, F. Klaedtke, and R. Bifulco, ''On the fingerprinting of software-defined networks,'' IEEE Trans. Inf. Forensics Security, vol. 11, no. 10, pp. 2160–2173, Oct. 2016.
[16] E. Sakic, N. Ðerić, and W. Kellerer, ''MORPH: An adaptive framework for efficient and Byzantine fault-tolerant SDN control plane,''IEEE J. Sel. Areas Commun., vol. 36, no. 10, pp. 2158–2174, Oct. 2018.
[17] J. C. Mogul, J. Tourrilhes, P. Yalagandula, P. Sharma, A. R. Curtis, and S. Banerjee, ''DevoFlow: Cost-effective flow management for high performance enterprise networks,'' in Proc. 9th ACM SIGCOMM Workshop Hot Topics Netw., 2010, pp. 1–6.
[18] M. A. Togou, D. A. Chekired, L. Khoukhi, and G.-M. Muntean, ''A hierarchical distributed control plane for path computation scalability in large scale software-defined networks,'' IEEE Trans. Netw. Service Manage., vol. 16, no. 3, pp. 1019–1031, Sep. 2019.
[19] M. Liyanage, I. Ahmad, M. Ylianttila, A. Gurtov, A. B. Abro, and E. M. de Oca, ''Leveraging LTE security with SDN and NFV,'' in Proc. IEEE 10th Int. Conf. Ind. Inf. Syst. (ICIIS), Dec. 2015, pp. 220– 225.