Is facial recognition going to be finished? The first “face hijacking” banking Trojan is born

For years, biometrics have been promoted as the ultimate in identity verification because each person's face, fingerprints and iris information are unique and difficult to forge. However, with the explosive development of artificial intelligence technology, biometric technology, especially facial recognition technology, is facing a huge threat.

Recently, network security company Group-IB discovered the first banking Trojan capable of stealing faces (identification data), which was used to steal users' personal identification information and phone numbers, as well as facial scan information. These images are then replaced with AI-generated deepfake images that can easily bypass facial recognition authentication on bank apps.
Researchers revealed that the "facejacking" Trojan was used in Vietnam earlier this month, where attackers lured victims into a malicious app, had them scan their faces, and then withdrew approximately $40,000 from their bank accounts. funds.
Sharmine Low, a malware analyst with Group-IB's Asia-Pacific threat intelligence team, revealed in a blog post: "Hackers have developed a new malware family specifically designed to collect facial recognition data. In addition, they have also developed a tool that This allows victims to communicate directly with cybercriminals posing as bank call centers."
The hard-to-prevent “face hijacking” Trojan attack
The Group-IB research team recently discovered a new Trojan program that can "hijack faces", codenamed GoldPickaxe.iOS. It is specifically targeted at iOS users. It can intercept text messages and collect facial recognition data and identity documents. Hackers can use this sensitive information to create deepfakes, replace synthetic faces with the victim's, and gain unauthorized access to victims' bank accounts.
Researchers pointed out that GoldPickaxe was developed by a large Chinese hacker group called GoldFactory. It is based on the Android banking Trojan GoldDigger previously developed by the organization. GoldPickaxe is the first variant of this series of Trojans to support iOS devices. Previously, it only supported Android devices).
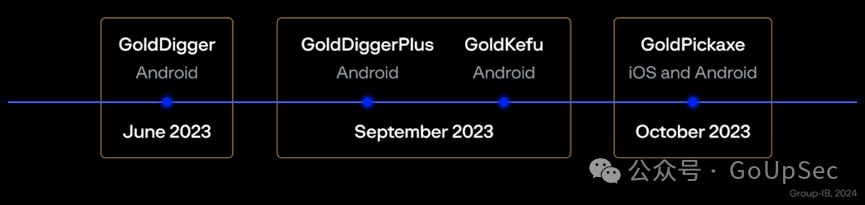 The evolution timeline of the GoldFactory Trojan
The evolution timeline of the GoldFactory Trojan
The GoldPickaxe.iOS distribution scheme is particularly noteworthy, with the hackers initially leveraging Apple's mobile app testing platform TestFlight to distribute the malware. After being kicked off TestFlight, the hackers turned to a more sophisticated, multi-stage social engineering scheme to convince victims to install mobile device management (MDM) profiles. This allows the hacker to take full control of the victim's device.
A common attack tactic for GoldFactory is to use a combination of SMS bombing and phishing techniques, often masquerading as a government service agent (including Thai government services such as the Thai Digital Pension and the Vietnamese Government Information Portal). Researchers say the Trojans are currently targeting older people in the Asia-Pacific region, but there are some "signs" the group is expanding to other regions.
The nightmare of bank APP
Currently, facejacking Trojan attacks have a high success rate in Thailand, as the country now requires users to confirm large bank transactions (over 50,000 baht) via facial recognition instead of a one-time password (OTP). Likewise, the State Bank of Vietnam has expressed its intention to make facial authentication mandatory for all remittances starting in April this year.
In Thailand, hackers disguised GoldPickaxe.iOS as a pension app. Victims are asked to take a photo of themselves and their ID when using the program. In the iOS version, the face hijacking Trojan will even issue some facial information collection instructions to the victim, such as blinking, smiling, turning the head left and right, nodding or opening the mouth.
Stolen videos of users’ faces are then used as raw material for face-swapping AI tools to create deepfake videos, which hackers can use to easily impersonate victims into banking applications.
"This method is often used to create a comprehensive facial biometric profile of the victim, a new technique not observed in other fraud campaigns," the researchers noted.
Is facial recognition really going to be finished?
The emergence of the "face hijacking" Trojan marks that biometric threats have become a reality. According to the latest threat intelligence report released by iProov, face-changing deep fake attacks surged by 704% in 2023. The biometric authentication company also saw a 672% increase in deepfake media used by deception tools and a 353% increase in digital injection attacks using emulators (imitation of user devices) and fraudulent content.
Andrew Newell, iProov’s chief scientific officer, said generative artificial intelligence has significantly improved hackers’ “productivity levels.” He noted: “These tools are relatively low-cost and easily accessible and can be used to create highly convincing synthetic media such as face swaps or other forms of deepfake content that can easily fool the human eye as well as outdated biometric solutions. .”
Gartner predicts that by 2026, 30% of enterprises will no longer trust the reliability of biometric tools. Akif Khan, vice president analyst at Gartner, said: “With the proliferation of hard-to-distinguish deepfakes, enterprises may start to question the reliability of (biometric) identity verification and authentication solutions.”
Additionally, some believe biometrics are more dangerous than traditional login methods—a user's unique biometrics if stolen may be permanently exposed and invalid because users cannot change them the way they can change a password or passkey.
How to protect yourself against biometric attacks
Group-IB offers some recommendations to help users avoid biometric attacks, including:
- Don’t click on suspicious links in emails, text messages or social media posts.
- Only download apps from official platforms like Google Play Store or Apple App Store.
- If you must download a third-party application, please "proceed with caution."
- Carefully review requested permissions when installing new apps, and "be extra vigilant" when they request accessibility services.
- Don't add unknown users to social apps.
- If in doubt, call your bank directly rather than clicking on the bank alert window on your phone screen.
Additionally, security experts advise users to watch for signs of malware infection on their phones:
- Rapid battery drain, slow performance, unusual data usage, or overheating (indicating that malware may be running in the background and consuming resources).
- Unfamiliar applications appear that have not been downloaded and installed (some malware disguises itself as legitimate applications).
- Some apps suddenly have increased permissions.
- Weird behavior, such as the phone making calls on its own, sending messages without consent, or accessing apps without input.