After reading the article, do you think the network surveillance cameras at home are still safe?

It has not been updated for almost a week. It is mainly a matter of time. Today I went through the study notes of the previous two years and sorted out the notes on passive information collection in penetration testing. It is enough for everyone to understand. There is no need for non-professionals to learn because If you don’t learn to use this thing properly, accidents can easily happen! ! ! Learn from the Internet what penetration testing is, what active information collection is, and what passive information collection is... Just a basic understanding will be helpful to you in the future, because many networks are attacked, systems are attacked, phished, and systems are hacked. Hackers and mobile phone hackers all use this technology. Everyone should learn to do defensive work on their mobile phones, systems, and networks in the future.
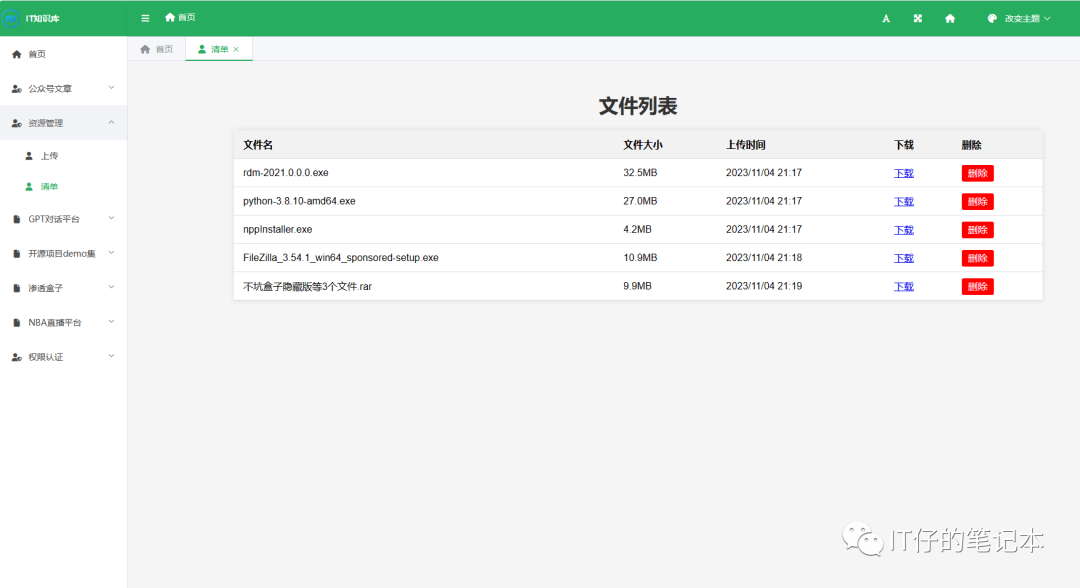
Then, the basic framework of my small website is almost the same. It mainly integrates several frequently used platforms. If you have any good suggestions, you can put forward them.
Warning case:
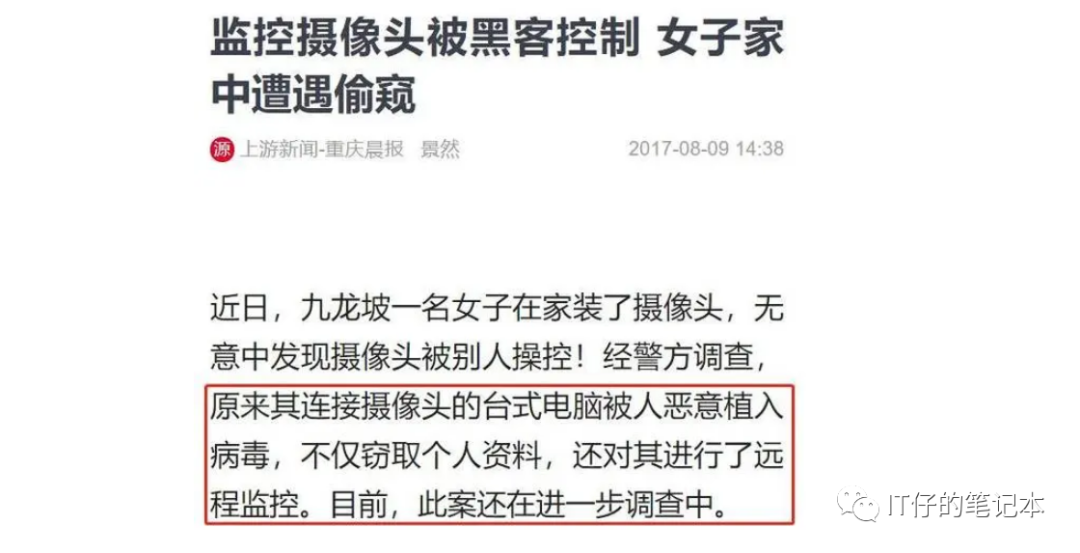
To give an example: If security work is not done well, the camera in your home may be exposed here, and then everyone can see it... It is scary to think about it.
passive information collection
In today's digital era, information security issues have become increasingly prominent, and penetration testing has become one of the important means to ensure network security. As one of the key steps in penetration testing, passive information collection can help security experts gain an in-depth understanding of the target system and discover potential loopholes and weaknesses. As an operation and maintenance personnel, you may not be able to penetrate, but you must know something, know or understand the relevant principles. In the future operation and maintenance process, you can reduce more security incidents and make your network and system safer. , data is more secure.
1. Definition of passive information collection
Passive information collection is during the penetration testing process, by observing and collecting information actively exposed by the target system without conducting active attacks. This information may include the network topology of the target system, domain name information, subdomain names, IP addresses, email addresses, employee names, etc. The purpose of passive information collection is to obtain a more comprehensive understanding of the target system and provide valuable clues for subsequent penetration testing efforts.
2. The importance of passive information collection
Passive information collection plays an important role in penetration testing and can provide the following benefits:
(1) Discover potential vulnerabilities
Through passive information collection, penetration testers can obtain relevant information about the target system to discover potential vulnerabilities and weaknesses. For example, by collecting the subdomain names of the target system, you can further detect possible security vulnerabilities in the subdomain names, such as unauthorized access, leakage of sensitive information, etc.
(2) Construct an attack path
Passive information collection can help penetration testers build attack paths and understand the network topology, service and application architecture of the target system, etc. This helps to conduct targeted penetration testing on the target system and improves the efficiency and success rate of penetration testing.
(3) Assisted social engineering attacks
Passive information collection can also support subsequent social engineering attacks. By collecting employee names, email addresses and other information on target systems, penetration testers can conduct phishing attacks, targeted social engineering, etc., making it easier to obtain sensitive information or system access.
3. Tips and Tools for Passive Information Gathering
When conducting passive information gathering, the following tips and tools may be helpful to penetration testers:
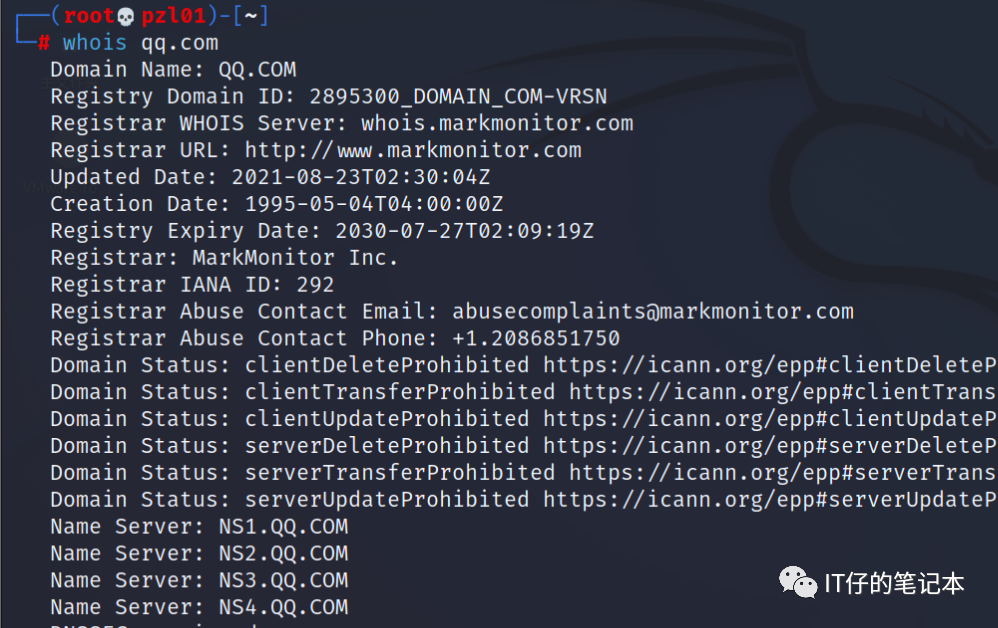
(1) WHOIS query
WHOIS query is a method of querying domain name registration information. You can obtain the domain name owner information, registration date, expiration date, etc. by querying the domain name registrar. This is useful for understanding the domain name information of the target system.
(2) Subdomain enumeration
Subdomain name enumeration is to query the main domain name of the target system and obtain all its subdomain names. Commonly used subdomain enumeration tools include Sublist3r, Amass, etc., which can help penetration testers discover possible vulnerabilities in the target system.
(3) Web crawler
Web crawlers can help penetration testers obtain sensitive information in the target system, such as sensitive files, directory structures, etc. Commonly used web crawler tools include Wget, Burp Suite, etc.
(4) Maltego collects subdomain names
Analyze real-world relationships between data accessed via the Internet, footprinting Internet infrastructure and people and organizational data, through the use of OSINT (Open Source Intelligence) technology, social networks, DNS records, and more
(5) Social media intelligence collection
Social media is a valuable source of information. Penetration testers can obtain some potentially useful clues by collecting social media information of people related to the target system.
[The above content is for learning purposes only!!!]
in conclusion
Passive information collection is an indispensable part of penetration testing. It provides penetration testers with valuable clues and information, helping them better understand the target system and discover potential vulnerabilities. When conducting penetration testing, we should make full use of various techniques and tools to conduct comprehensive and effective passive information collection. Only by in-depth understanding of the target system can we better ensure network security and prevent potential threats. To do a good job in network security, start with defense.