Introduction to Socks5 proxy protocol

Introduction to Socks5 proxy protocol

Part 01. Socks5 protocol concept
Socks5 is a proxy protocol that plays an intermediary role between front-end machines and servers that use TCP/IP protocol communication, allowing front-end machines in the intranet to access servers in the Internet network. Compared with earlier SOCKS protocol versions, SOCKS5 has the following main functions and features:
(1) Support IPv4 and IPv6 : The SOCKS5 protocol can support both IPv4 and IPv6 addresses to adapt to the needs of different network environments.
(2) User authentication: SOCKS5 supports multiple user authentication methods, such as username/password authentication, GSS-API authentication, etc., which increases the security of the connection.
(3) Data encryption : The SOCKS5 protocol can encrypt data through encryption protocols such as TLS/SSL to protect data security.
(4) UDP forwarding : Compared with the SOCKS4 protocol, the SOCKS5 protocol supports UDP forwarding and can transmit UDP data in the proxy connection.
Commonly used socks5 proxy software includes the following types.
- Shadowsocks : an open source proxy software that provides encryption and tunneling technology to protect the security of data transmission
- Proxifier : A popular proxy software that connects web applications to target servers through a SOCKS5 proxy
- Dante : a high-performance SOCKS5 proxy server that supports multiple authentication methods and flexible configuration options
- PuTTY : An SSH and Telnet client that can also be used as SOCKS5 proxy software to provide secure proxy connections through SSH tunnels
- OpenSSH : An open source software for remote login and file transfer, which can also be configured as a SOCKS5 proxy server
- Tor : An anonymous network tool that can connect to the Tor network through a SOCKS5 proxy to protect user privacy and anonymity.
Part 02. Sock5 protocol interaction process
The socks protocol interaction process is as follows. The interaction details are shown in Figure 1, and the data packet format is shown in Figure 2.
(1) PC initiates a connection request to access the server.
(2) The connection request is intercepted by the socks5 client, and then the socks5 client actively establishes a TCP connection with the socks5 proxy server.
(3) The socks5 client actively authenticates with the socks5 proxy server.
(4) After the authentication is passed, the socks5 proxy server actively establishes a connection with the server. If the PC initiates a TCP request, a TCP request connection is established, otherwise a UDP request connection is established.
(5) After requesting to establish a connection, data exchange occurs between the socks5 proxy server and the server.
(6) The socks5 proxy server forwards the data to the socks5 client through the socket.
(7) socks5 client forwards data to PC.
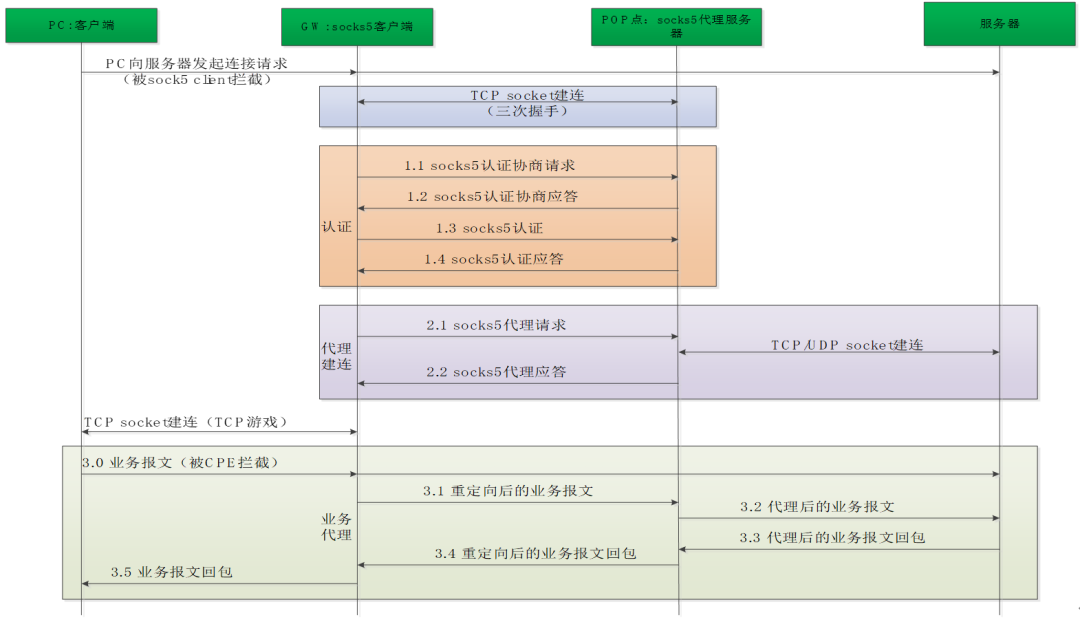 Figure 1 socks5 protocol interaction process
Figure 1 socks5 protocol interaction process
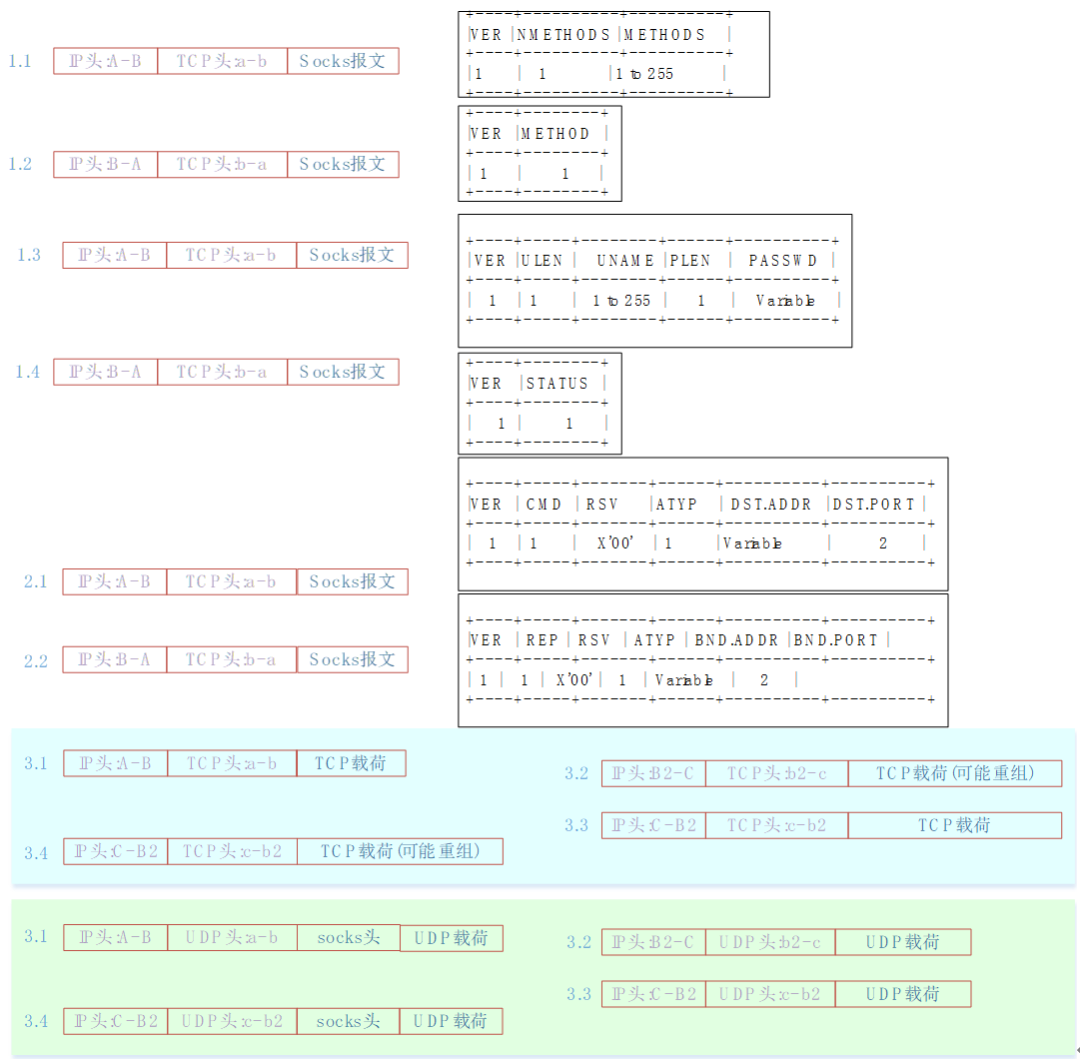 Figure 2 socks5 protocol packet format
Figure 2 socks5 protocol packet format
Part 03. Sock5 application scenarios
The SOCKS5 protocol plays an important role in a variety of application scenarios. The following are some common application scenarios:
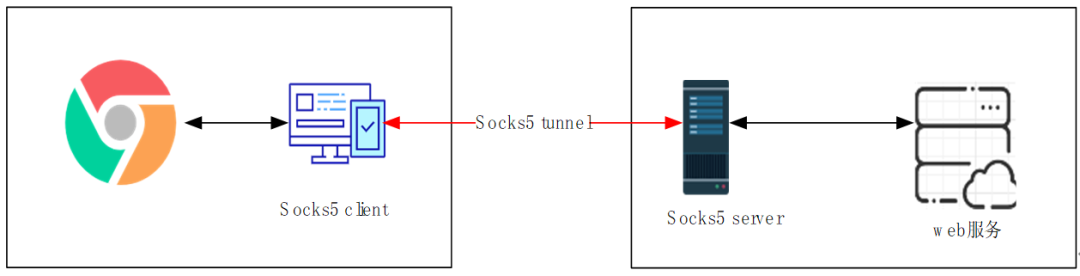 Figure 3 Socks5 general deployment topology
Figure 3 Socks5 general deployment topology
- Bypassing network blocks : In some regions or organizations, there may be network blocks that restrict users from accessing specific websites or services. By using a SOCKS5 proxy, users can bypass these blocks and access restricted content.
- Accelerate network connections : Sometimes, users may experience slow network connections or high latency. By using a SOCKS5 proxy, you can choose a faster proxy server, thereby improving network connection speed and response time.
- Bypass geographical restrictions : Some websites or services may be restricted based on the user's geographical location. By using a SOCKS5 proxy, users can disguise their IP address, bypass geographical restrictions, and access restricted content.
- Enterprise internal network : In the enterprise internal network, using SOCKS5 proxy can achieve access control and management of internal resources, improving network security and management efficiency.
Part 04. Application of Sock5 protocol in home broadband
In a home broadband network environment, in order to solve the problem of slow network connection speed or high delay and provide a differentiated and high-quality network experience, China Mobile provides intelligent network intelligent acceleration service, which imports user traffic into the accelerated network through socks5 tunnel. Reduce the latency of game access and solve problems such as lag and packet loss. In this scenario, the socks5 client and socks5 server have been modified. The client directly initiates a socks5 request, and the server receives the request and acts as a proxy.
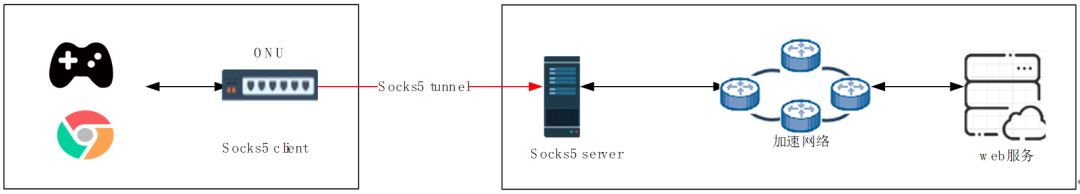 Figure 4 Socks5 topology in home broadband scenario
Figure 4 Socks5 topology in home broadband scenario
Part 05. Summary
The SOCKS5 protocol is an application layer protocol used to establish proxy connections between clients and proxy servers. It supports TCP and UDP transport protocols and can proxy connections for various application layer protocols. The SOCKS5 protocol forwards client requests through a proxy server, providing functions such as bypassing network blocks, improving network security, accelerating network connections, and bypassing geographical restrictions. Through encryption protocol, SOCKS5 protocol can protect the security of data. In general, the SOCKS5 protocol has extensive applications in network proxy and tunnel technology, providing users with a safer and freer network access experience.