The ultimate guide to SD-WAN architecture

Software-defined wide area networks (SD-WAN) have been widely adopted by enterprises in recent years and are a cost-effective way for branch offices to connect to data centers and other cloud applications. This paper will focus on the SD-WAN basics, how it works, good practices and troubleshooting, and analyze the future development of SD-WAN architecture.
Introduction to SD-WAN
For multinationals or large enterprises with branches in multiple cities, the high cost of fast and reliable application performance, the high cost of private network circuitry, and the complexity of day-to-day tasks such as configuration, monitoring, and management are magnified in the WAN, and while WAN optimization and traffic shaping can be a real help, they do not solve all the problems at the edge of the network, and the cost of dedicated circuits is still high and can take months to deploy. Additional staff may also be required to manage devices at branch offices and remote locations.
SD-WAN products and services typically have the ability to connect WAN to virtualization, centrally monitor policies, orchestrate, and dynamically manage traffic. Some vendors claim to offer SD-WAN products, but in fact they offer only a small fraction of the typical functionality of the technology, which is not really SD-WAN. SD-WAN provides redundancy between WAN connections and automatically fails over to another path if the primary path fails or becomes unavailable. SD-WAN can also use load balancing across multiple connections to improve application and network performance. SD-WAN has many advantages that can solve the problem of managing and maintaining WAN configurations.
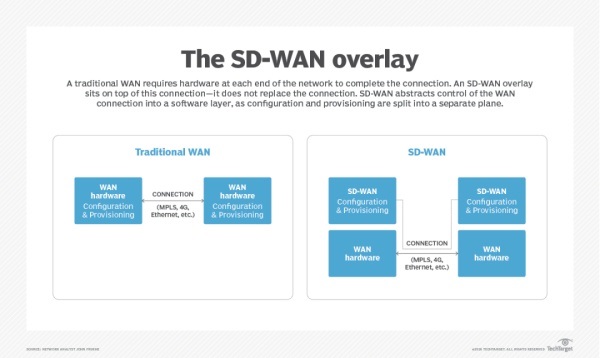
SD-WAN and traditional WAN
SD-WAN has built-in many traditional WAN features, such as load balancing and disaster recovery. However, in a traditional WAN, adding these features can be time-consuming and complex. SD-WAN supports real-time, automated, and standardized configuration changes that significantly reduce human error caused by manual configuration of traditional WAN.
The SD-WAN architecture relies on virtualization overlay, which makes it easier to shift and replicate policies between distributed edge devices. For example, as the organization evolves, it can use a location for existing WAN connections to SD-WAN devices to remotely manage site policies through a centralized controller. This agility provided by virtualization is critical to meeting business needs.
When SD-WAN is put together with a virtual private network, the difference is obvious. For example, a typical virtual private network is ideal for enterprises with a single IP backbone, but when voice and video or network blocking is introduced, the architecture crashes. SD-WAN's fine-grained support gives it an edge over basic Internet virtual private networks in terms of quality of service (QoS). Similarly, virtual private networks do not always provide the optimization and advanced security required for cloud-based services for Internet connections. SD-WAN also automatically detects network conditions and provides network visibility.
SD-WAN 与 MPLS
MPLS has been the organization's trusted choice for connectivity for decades, but it is also expensive and has some lack of flexibility. The SD-WAN architecture enables organizations to continue to use MPLS while increasing efficiency and saving costs by adding alternative, lower-cost links, such as broadband or wireless. MPLS still has the advantage of being a dedicated connection to end-to-end QoS. MPLS providers can offer a relatively comprehensive SLA.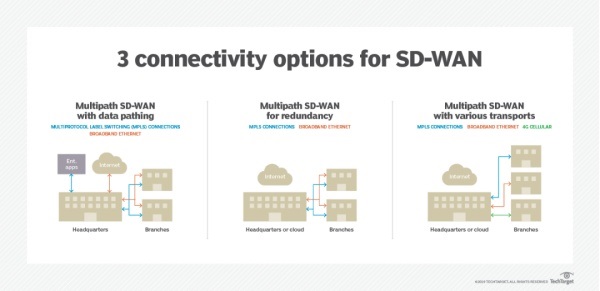
SD-WAN challenge
Although SD-WAN has many advantages, its disadvantages must also be considered comprehensively. For example, while SD-WAN should reduce connection costs in the long run, cost savings are often minimal in the short term.
Adding a layer to a WAN can create new vulnerabilities that must be closely monitored and managed. SD-WAN can get connectivity from multiple vendors, which can make management more difficult. Organizations cannot ignore the expertise needed to deploy and manage SD-WAN technologies, and as vendors try to simplify most of the processes surrounding SD-WAN, the enterprise itself still needs to carefully consider the requirements of each feature they want to roll out, as well as the overall security plan. 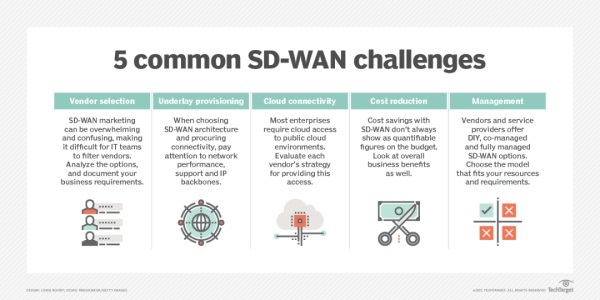
According to IDC, the SD-WAN market is growing rapidly and is expected to reach $5.25 billion by 2023. Still, it's difficult to tell exactly what's in each vendor's or service provider's product. The first thing an organization needs to do is determine which products or services are best suited to their network and business needs.
Deploy SD-WAN
Once an organization has identified a vendor and is ready to bring SD-WAN to the network, it needs to examine their existing network and determine whether their hardware can support SD-WAN, or whether they need to upgrade or purchase new devices. Some businesses may need to purchase hardware-based devices or virtual server software.
Preparations may involve in-depth details, such as which routing protocol is most effective in which location. Not all agreements apply anywhere, so organizations must carefully consider options.
Before deploying SD-WAN, users should perform proof-of-concept testing to measure important metrics such as failover speeds from a failure link to an operational path, isolation of traffic types for different links, and how to increase throughput by using multiple parallel links.
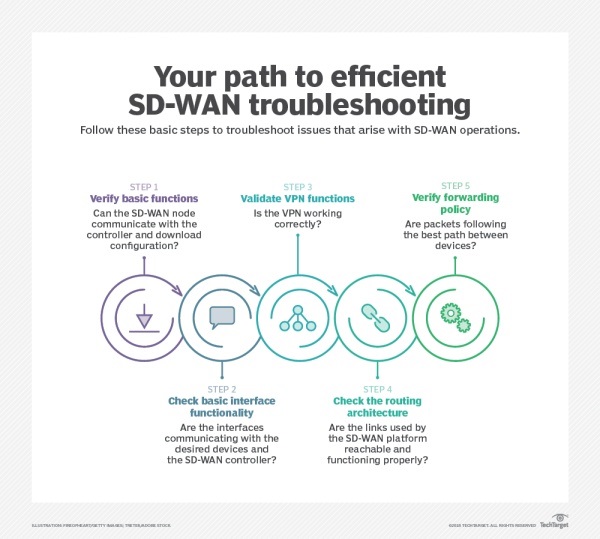
In addition, it is equally important to develop stable troubleshooting and monitoring strategies. Network teams need to consider event handling, active path testing, physical state, and topology, all of which are essential for troubleshooting.
SD-WAN security
While security is not the primary reason for adopting SD-WAN, vendors and providers have addressed security issues by supporting IP security standards and working with top security vendors to integrate protection into their products and services.
One of the basic capabilities organizations want to see in SD-WAN products or services is to securely integrate new devices into SD-WAN to prevent malicious devices from accessing their WAN traffic. Other features include data plane encryption and control plane encryption.
Organizations should fully understand the details of the security policy of the SD-WAN vendor or provider and ensure that it meets business needs. For example, to evaluate whether SD-WAN software logs invalid connection attempts or warns administrators of unauthorized access or malware, this type of log can detect and prevent DoS attacks.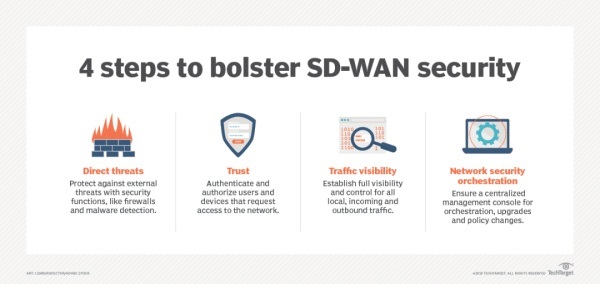
The future of SD-WAN
SD-WAN is a technology that works well with 5G and the Internet of Things (IoT). At present, enterprise 5G services and equipment has not been widely used, but the potential of 5G can not be underestimated. 5G has lower latency than 4G, creating faster and better connections. SD-WAN promises to intelligently simplify communications from IoT edge devices to centralized data centers, especially when matching low latency in 5G. With the advent of new technologies such as SASE, the future of SD-WAN will flourish. The first task for an organization is to weigh whether SD-WAN makes sense in its corporate environment.