5 Easy Ways to Check Open Ports on Linux

An open network port is the easiest access point to a network. Many times we need to run unwanted services on ports that are visible from outside the Internet. With massive daily scans of the entire internet looking for vulnerable services on open ports, our networks are constantly under threat of attack if those services are vulnerable.
Learn how to scan and view open ports on your Linux system to protect your network from threats.
What is a network port?
A network port is a logical access point to the system and can be used as a channel to host multiple services. Ports are represented by 16-bit integers, so the maximum port number is 65535.
We can think of ports as the doors and windows of a house, and all the doors and windows are all the different entry points to the computer. There are three types of ports: system ports (1-1023), registered ports (1024-49151), and ephemeral or dynamic ports (49152-65535).
When you start an application that needs to connect to the Internet, it uses dynamic ports to transmit and receive data over the network. However, when you start a web server or SSH server, it usually binds to a system port or a registry port.
The default system port is 80 for the HTTP serving web server and 22 for SSH. These regulations, such as port ranges, are set by the Internet Assigned Numbers Authority (IANA). We can browse the RFCs about ports to get a complete list of all ports and their capabilities.
It's important to know the most common vulnerable ports so you can make sure they are closed or protected.
1. Use netstat to check open ports
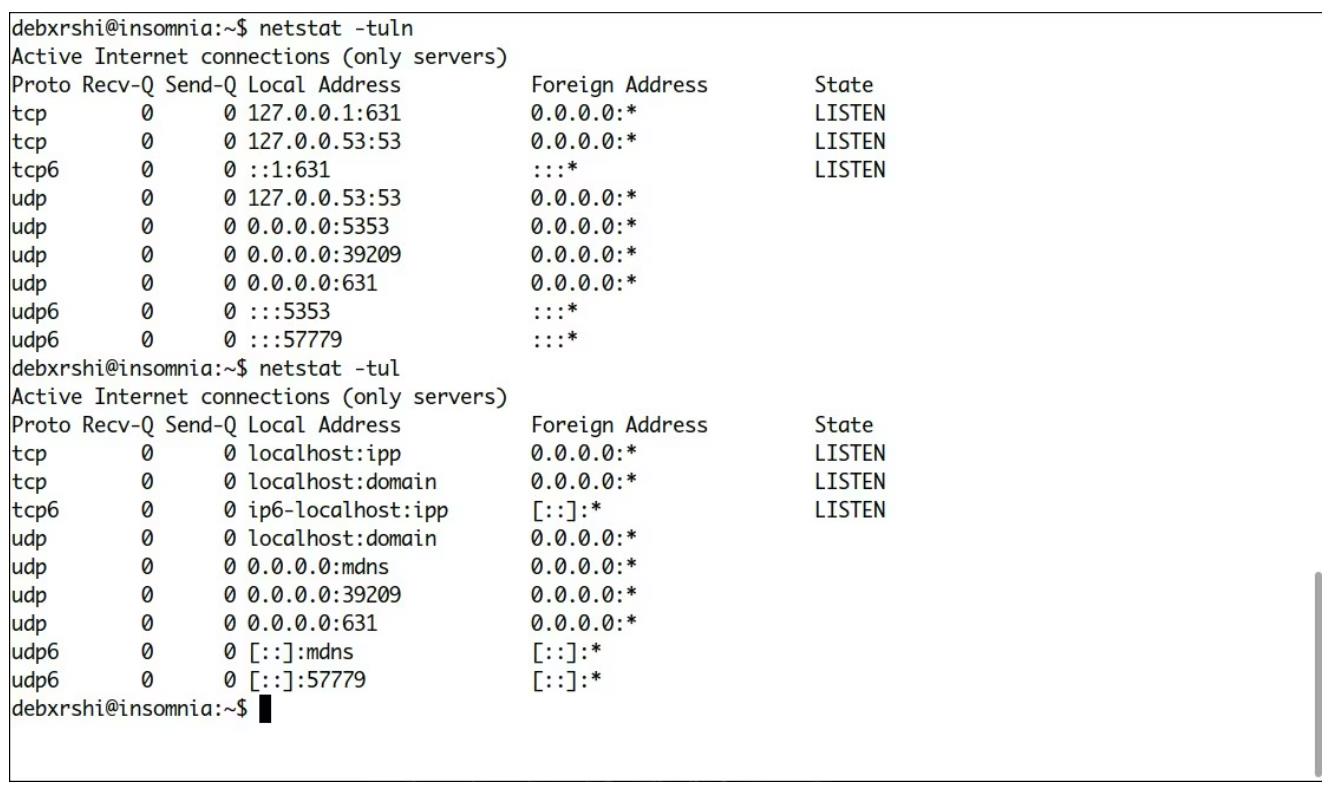
netstat is a popular utility that we can use to view network statistics of a Linux system. It is part of the net-tools package.
The net-tools package is now depreciated due to lack of proper maintenance by the developers. This is also why you may encounter "ifconfig: command not found" errors when running the popular ifconfig command on Linux.
Therefore, on modern systems, the net-tools package must be installed before the netstat command can be run. Here's how to check for open ports with netstat:
netstat -tuln- 1.
Command explanation:
- -t Displays the TCP port.
- -u Display UDP port.
- -l Displays the listening port. Replace this with a if you want to see all ports regardless of their status .
- -n Displays the numerical value of the port, rather than resolving to a service name. For example, port 22 is shown instead of SSH, the service running on that port.
2. Check for open ports with ss
ss is a modern version of the netstat utility. We'll find it pre-installed on all modern Linux distributions. The syntax for checking open ports using ss is the same as netstat.
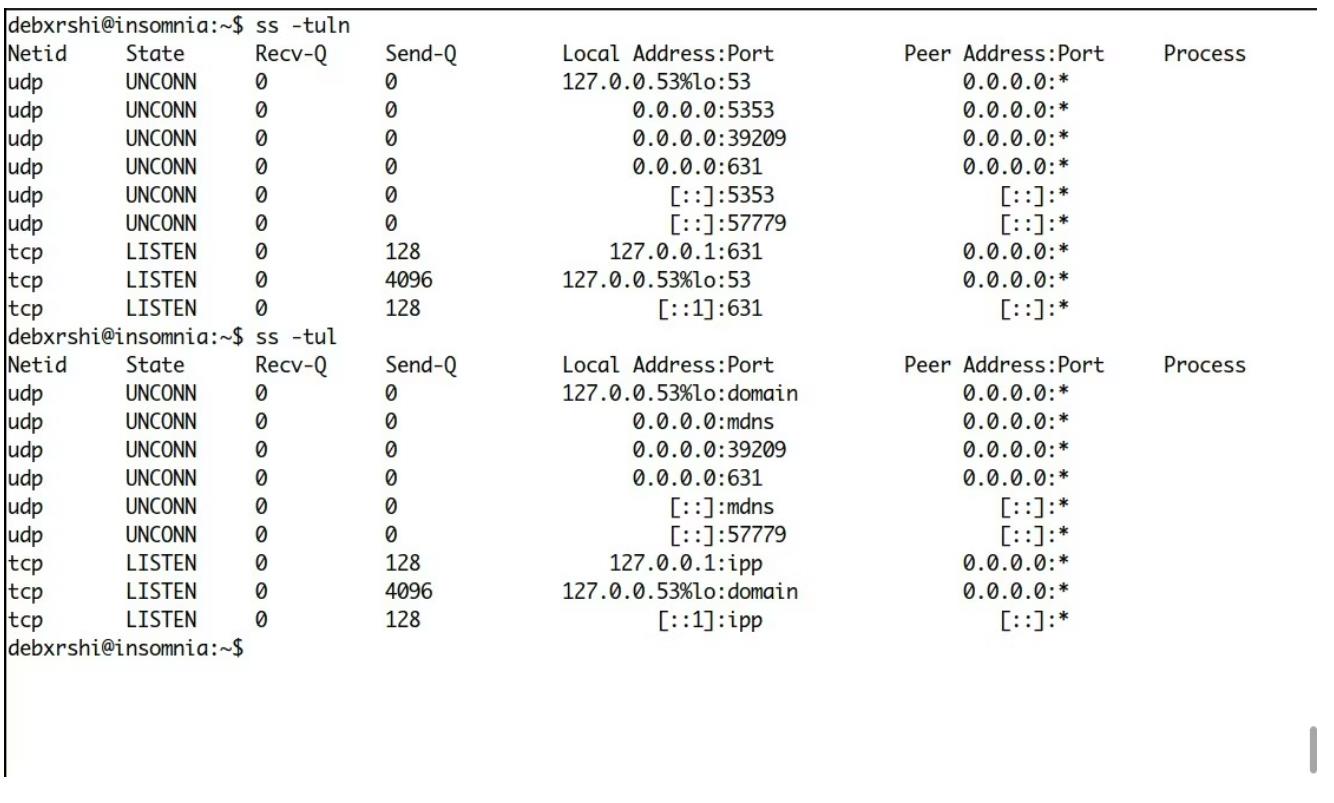
Here's how to check for open ports with ss:
ss -tuln- 1.
Command explanation:
- -t Displays the TCP port.
- -u Display UDP port.
- -l Displays the listening port. Replace this with a if you want to see all ports regardless of their status .
- -n Displays the numerical value of the port, rather than resolving to a service name. For example, port 21 is shown instead of FTP, the service running on that port.
3. Check for open ports using Nmap
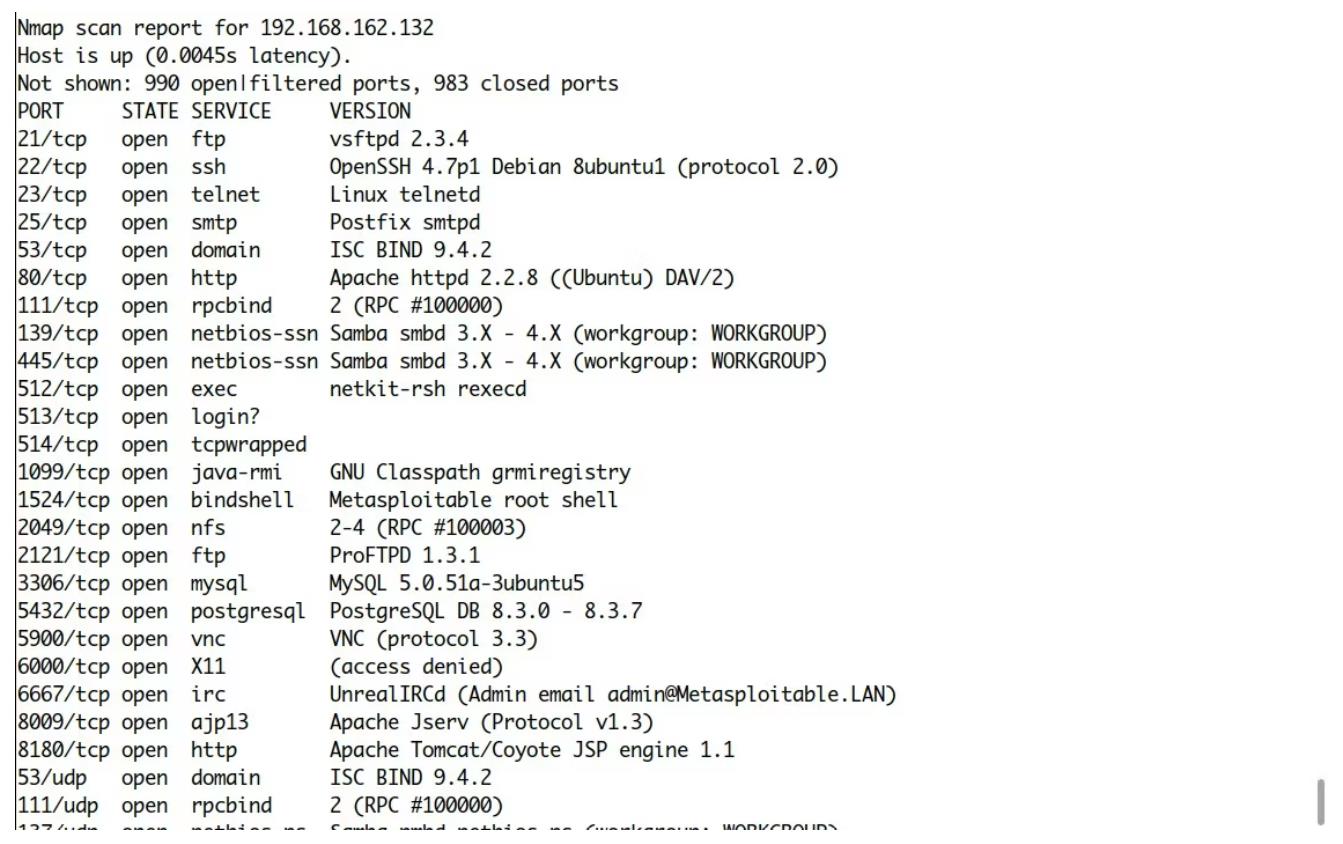
Nmap is one of the most popular tools in the world of cybersecurity and networking. It is a major name when it comes to cybersecurity penetration testing. Its main use case is port scanning, so you can get information not only about ports that are open in your system, but also whether they are vulnerable and exploitable.
Also, if you wish to check for open ports in remote systems that have IDS/IPS and firewalls set up, don't worry because Nmap can also bypass firewalls and IDS/IPS with the right switches.
Check out this comprehensive guide to Nmap for beginners to explore Nmap's various features and how to use them. While possible, trying to bypass the firewall is not recommended as it is not completely reliable, so it is better to connect to the remote server via SSH and run Nmap locally.
Here is the command to check for open ports using Nmap:
nmap -sTU -sV <ip-address> -T 5 --min-rate 9000 --min-parallelism 9000 --initial-rtt-timeout 50ms --max-rtt-timeout 3000ms --max-retries 50 -Pn --disable-arp-ping -n --script vuln,exploit,auth -v -oX <filename>- 1.
Command explanation:
- -sTU sets scan type to TCP connection and UDP scan.
- -T 5 sets the timing template to aggressive for extremely fast scans (not recommended on unprotected systems as this may lead to DoS attacks).
- -sV Turn on service scanning.
- --min-rate 9000 tells Nmap to send 9000 packets per second.
- --initial-rtt-timeout 50ms tells Nmap to first wait 50ms for a response to every SYN packet it sends.
- --max-rtt-timeout 3000ms tells Nmap to wait for a response for at most 3000ms.
- --min-parallelism 9000 Set the minimum number of concurrently running scripts to 9000.
- --max-retries 50 tells Nmap to retry 50 times to connect to the port.
- -Pn disables ping detection.
- --disable-arp-ping Disable ARP probing.
- -n disables DNS resolution.
- --script vuln,exploit,auth Run three scripts to test for different types of vulnerabilities in discovered ports.
- -v returns verbose output.
- -oX save the results to an XML file.
- -6 Optional parameter to scan for IPv6 addresses.
4. Check for open ports with lsof
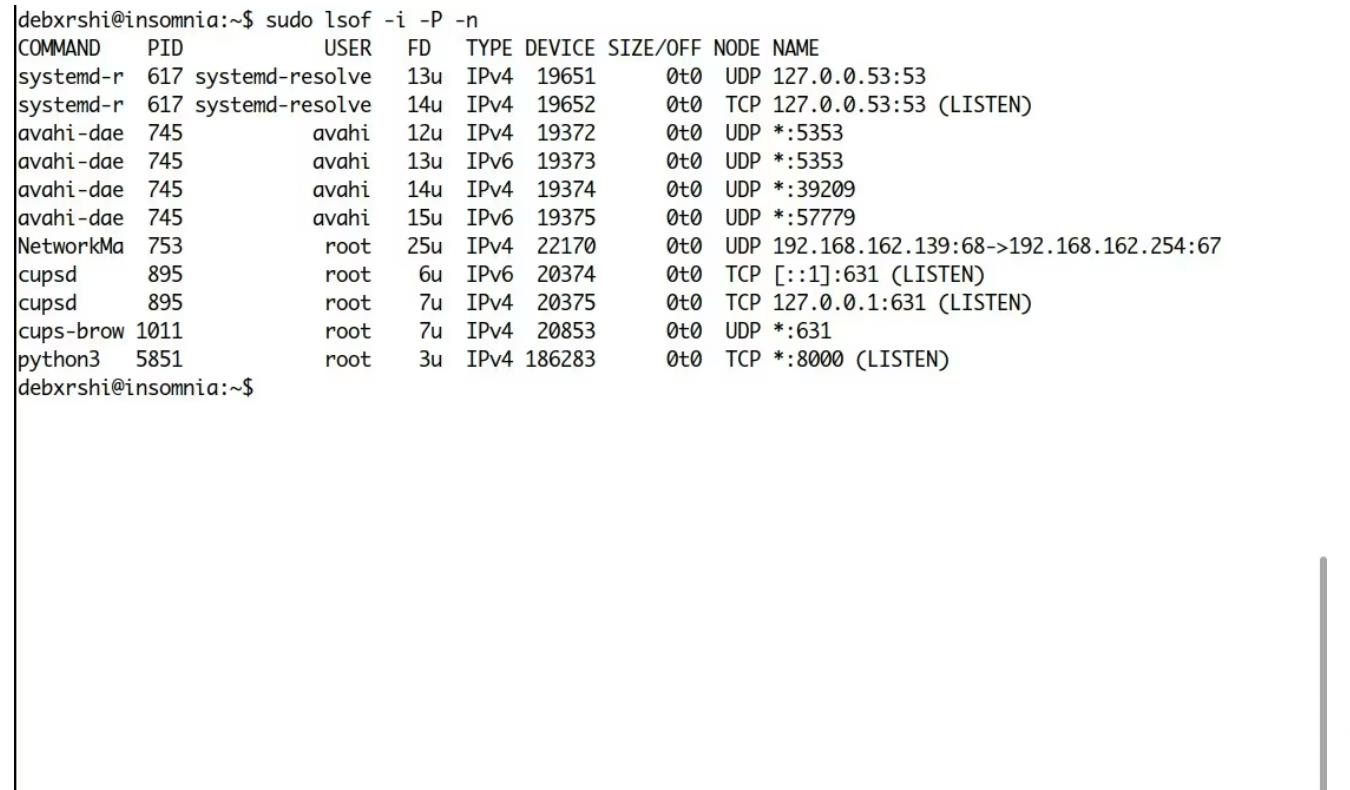
The lsof command in Linux is used to list open files. However, if we add some switches to it, we will be able to see the internet connections and ports open on our local machine. Here's how to check for open ports with lsof:
lsof -i -n- 1.
Command explanation:
- -i lists all network and Internet files.
- -n Do not resolve hostnames.
5. Check for open ports using netcat
netcat is a command-line utility that allows you to read and write from TCP/UDP connections. Note that this is only a feature of netcat. You can view its man page with the man netcat command to explore all its features and how to use them.
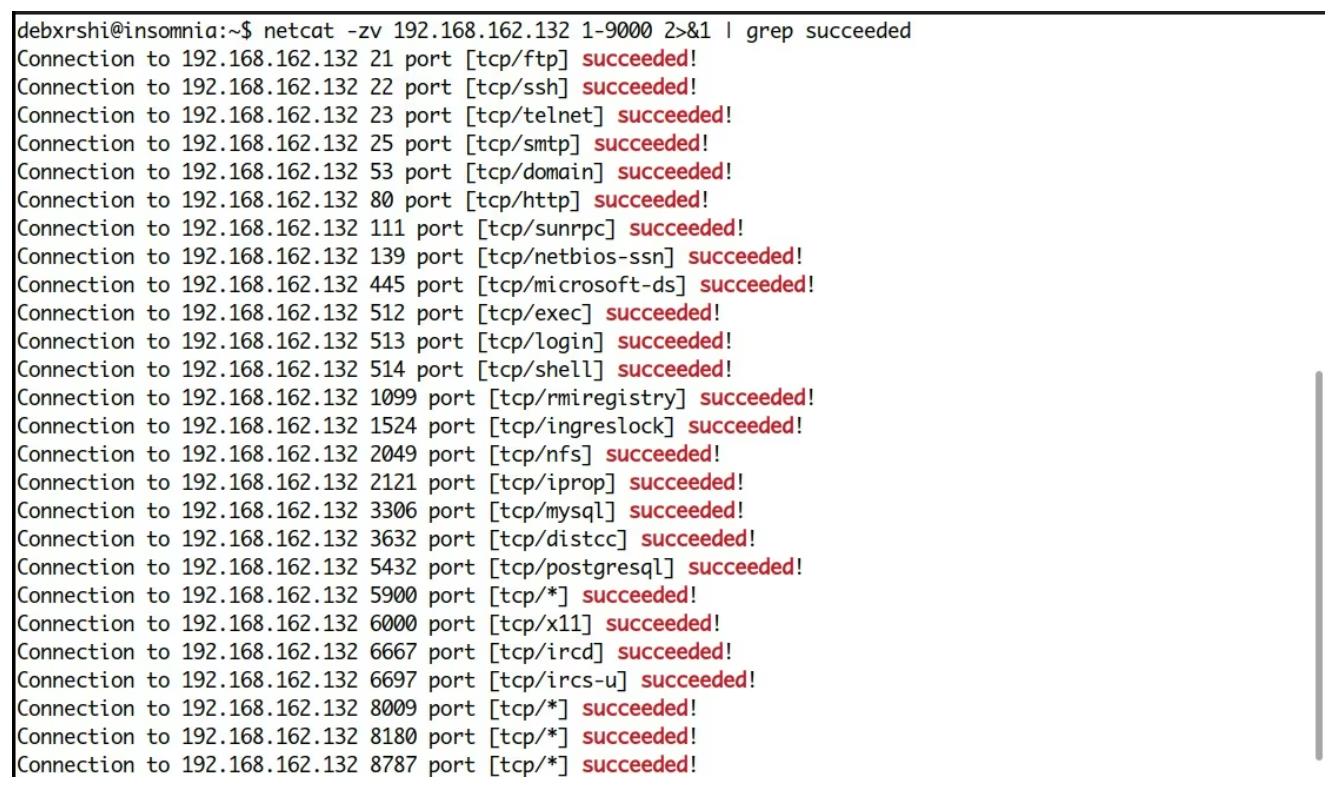
Here's how to scan for open ports with netcat:
nc -zv <ip-address> <start_port-end_port> | grep -v "refused"- 1.
Command explanation:
- -z sets netcat to scanner mode.
- -v returns verbose output.
- grep -v "refused" returns output lines without the word "refused". This is to prevent the terminal from being clogged with "connection refused" messages when netcat receives no output from the port.
- 2>&1 : This is an optional switch that you may need to turn on for grep to work when running netcat in verbose mode. netcat returns output to stderr (denoted by 2). So, to grep output, you have to redirect stderr to stdout (denoted by 1), which is then piped into grep.
The better you understand your network, the better you can protect it
Knowing which ports are open and which services are running on the system is an important step in defending against potential external attacks. This allows us to search for and shut down unnecessary services, find outdated services, and also detect if any malicious files are running on the system, such as bind or reverse shell backdoors.
Original title: 5 Easy Ways to Check for Open Ports on Linux
Original Author: DEBARSHI DAS