The Network Is So Smart Wireless Network Construction Experience Sharing

The Network Is So Smart Wireless Network Construction Experience Sharing
introduction
In recent years, Bank G has focused on the strategic goal of building a wealth management bank around the digital transformation of business, and proposed a "123+N" digital banking development system to support the digital transformation and long-term development of business. The financial technology sector combines various needs, whether it is external services or internal operations. , use digital means to integrate into more internal and external scenarios, and enable technology to serve more internal and external customers. In terms of internal network operation, starting from 2022, G Bank has carried out wireless network construction based on WiFi6 technology, integrating new wireless network and intelligent operation and maintenance technologies such as intelligent wireless operation and maintenance and integrated certificate ification system, demonstrating that G Bank is promoting digital transformation, intelligent Now, I would like to share the experience of building this wireless network with you.
WiFi6 (formerly known as: IEEE802.11ax) is the sixth generation of wireless network technology, the name of the WiFi standard, and a wireless local area network technology created by the WiFi Alliance based on the IEEE802.11 standard. WiFi6 will allow communication with up to 8 devices at a maximum rate of 9.6Gbps. Compared with the previous generations of WiFi technology, the new generation of WiFi6 has the characteristics of faster speed, lower delay, larger capacity, more security and power saving, and has broad application prospects in industrial fields, such as industrial parks and office buildings. , shopping malls, hospitals and airports, etc.
1. Wireless network architecture design
This wireless network transformation and construction mainly covers the office building with full wireless WiFi6 coverage, so that users can obtain more stable and secure network access and a higher access rate. At the same time, according to management requirements, the wireless network is strictly isol at from the internal network, and considering the possibility of wireless Internet demand in multiple venues in the same city in the future, the architecture design mainly has the following characteristics:
- 01 -
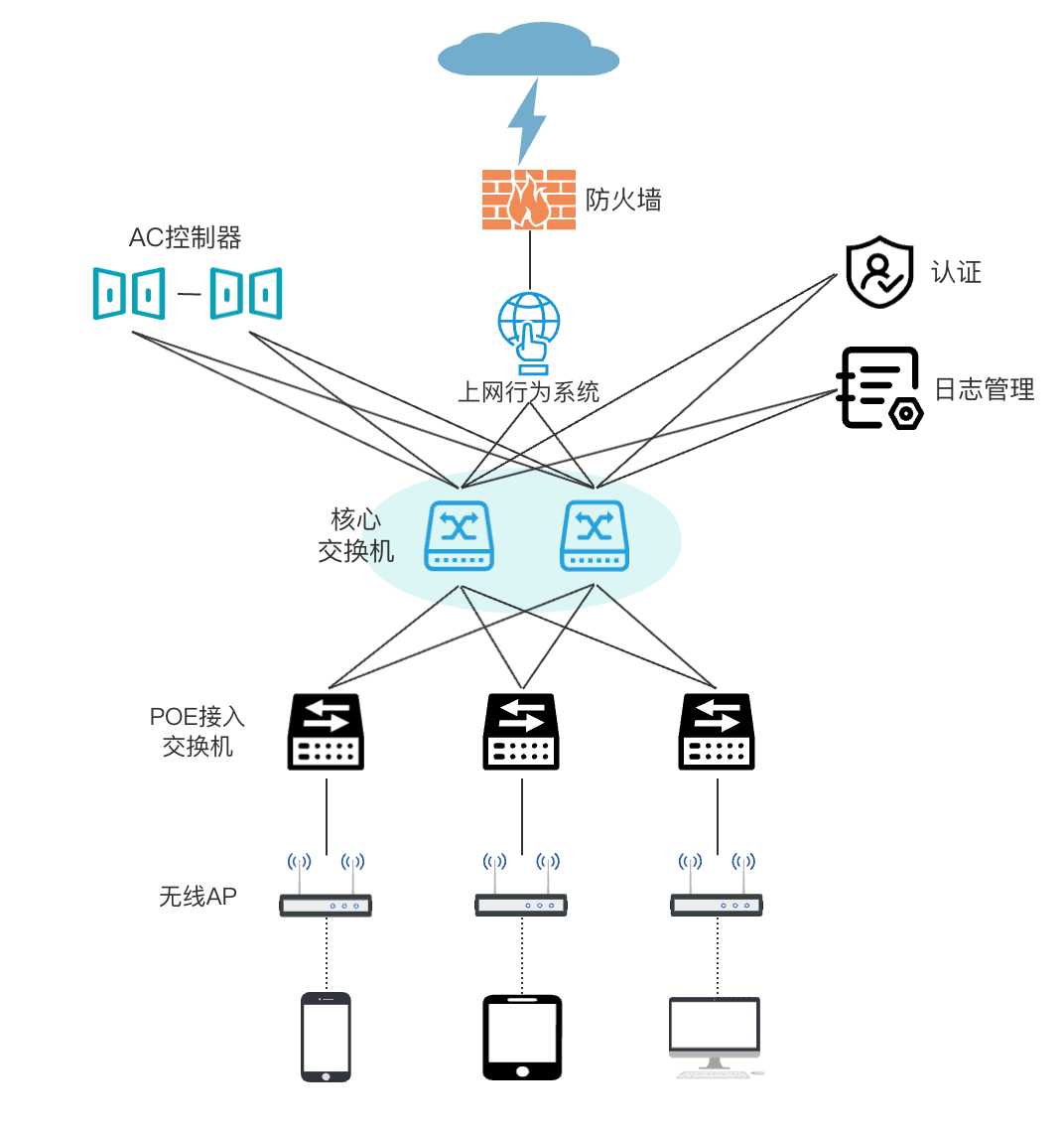
The main network architecture adopts a star structure, and all access points are aggregated through a core switch. The subsequent support uses bare optical fibers or dedicated lines to achieve three-layer interconnection through the OSPF routing protocol. The Internet exit uses the Internet leased line of the construction office building as the exit, which can be based on traffic Flexible expansion is required to meet the overall bandwidth requirements;
- 02 -
Deploy firewalls, online behavior systems, authentication and log management and other system equipment to perform login authentication, authority management, behavior management and policy control for users, and realize intelligent unified management and operation and maintenance of basic network equipment in the wireless environment;
- 03 -
In the wireless environment, all thin AP devices that support the WiFi6 standard are used. Installation and replacement can realize zero-configuration AC unified management. The traffic is forwarded locally by the AP. The AC controller is only responsible for management, security and auth enticement , not for traffic forwarding, reducing AC control. While reducing server performance consumption, it can greatly improve user access efficiency and network access speed;
- 04 -
The core switches of the wireless network are deployed in a stacking manner to improve management efficiency and achieve equipment redundancy;
- 05 -
The authentication server adopts cluster deployment to achieve system redundancy and high reliability. The authentication system performs access authentication and permission grouping for users through user name, IP, MAC address and other information, and is linked with the Internet behavior system to implement diff erent behavior strategies According to group permissions, can realize flexible management and control of different group behavior strategies, realize real-name authentication + real-name audit of users, and meet compliance requirements;
- 06 -
The wireless mobile roaming adopts the two-layer roaming method, and the user can realize fast and smooth switching between different APs in the WiFi coverage area, and cooperates with the user's non-perceptual authentication to avoid frequent user logins from affecting the user experience.
2. Wireless network security isolation
In order to avoid introducing new security threats during wireless network construction, for example: open network environment, becoming an attack tool to provide convenient means for attack, illegal user access, user data leakage, DDoS attack on wireless AP, illegal AP a access and other issues, the security design of the wireless network should be carried out from two aspects: wireless network design management requirements and terminal security control requirements:
(one)
In terms of wireless network design and management requirements, firstly, the wireless network must be strictly physically isolated from the office and business network of the unit. From the perspective of management requirements, the construction of office WLAN and production WLAN connected to the office and production network in the industry is prohibited, and key considerations should be given to the construction of Internet WLAN. Three aspects of network security, coverage, and physical layer security management:
1. Network Security
Wireless users are divided into independent network segments and VLANs, and each VLAN is logically isolated to prohibit mutual visits; security protection devices (FW, Internet behavior management and other devices) are deployed at key network nodes for isolation and access control, and log records are made to meet the requirements of in-line logs. Requirements related to storage duration are easy to trace afterwards; the internal and external networks maintain strict physical network isolation; the necessary layer 2 anti-ring strategy is enabled to prevent illegal dev ice access;
2. Coverage
The transmission power is adjusted on demand, and the network is optimized to shrink the coverage to the business demand area; the same scene has a unified SSID (without sensitive information), which is conductive to the deployment of security policies;
3. Physical layer security
Securely encrypt wireless communication channels; establish security baseline management (alarms for configuration changes or changes in wireless-related services); strengthen management account and password security for wireless network devices; disseminated information can detect potential safety hazards in time .
(two)
At the level of terminal security management and control, two aspects of terminal information authentication and user information authentication are mainly considered:
1. Terminal information identification
It is forbidden to mix internal and external networks for terminals. When intranet terminals use Internet WLAN, they are vulnerable to security threats from the Internet. For example, some intranet terminals that access the Internet are implanted with Trojan horses by hackers to steal business data of When reconnecting to the intranet, the Trojan horse poses a threat to the intranet. Therefore, the security tools for terminal information identification should be used to identify the characteristics of the intranet machine, and the mixed use of internal and external networks for various terminals is prohibited;
2. User information identification
Through real-name authentication such as user name or SMS verification code/password, real-name authentication is performed on users accessing the Internet WLAN. The authentication system is linked with the export Internet behavior audit equipment to record Internet access behavior in real name.
This wireless network construction is designed around the design and control of the above two aspects for security protection design, through control means such as network equipment security control, user authentication and escape security control, Internet exit control and user aud it security control, AC controller security control, etc., to ensure wireless security. Network security runs smoothly, as follows:
- All non-network device interconnection interfaces on network devices are configured with edge ports, and functions such as BPDU Guard, Root Guard, and DHCP Snooping are enabled to prevent illegal device access from causing Layer 2 loops and ARP spoofing, and at the the same时间, all network devices except SSH are turned off Port and limited network segment management to ensure the security of network device login;
- The WAP3 security protocol is used for users to access wirelessly. After access, users are distinguished to meet the wired and wireless authentication requirements of different roles. Different wired and wireless Internet access permissions are set for different user identities. Wireless users pass portal authentication , and wired users enable 802.1 X security access authentication to prevent illegal user login. The access policy is linked with the security management of PC terminals according to the requirements to detect and find non-compliant PC terminal access in time. At the same time, There are escape channels for wireless and wired authentication to ensure that authentication fails. One-key escape can be performed to reduce the impact on users;
- Firewalls are deployed at Internet exits for security policy control, Internet behavior auditing controls access restrictions on illegal websites and illegal applications, and controls and log records users' online behaviors;
- Appropriately deploy wireless security suppression control equipment, strengthen the detection of counterfeit wireless networks, and prevent network security attacks such as spoofing and illegal phishing.
3. Wireless network intelligent operation and maintenance
"Three points for construction and seven points for operation and maintenance", because the deployment points of the wireless network are widely distributed along the floor and the site, and the number of devices is relatively large, which means more operation and maintenance management needs, requiring a certain amount of manpower input and management costs. At the same time, wireless network troubleshooting is also a difficult point. In the process of wireless applications, there are many factors that affect the experience of wireless networks. The traditional operation and maintenance method only starts from the abnormal alarms of network devices and wire less ACs/APs, and is useful for troubleshooting large-scale network faults. It is effective, but it cannot accurately locate the problems that affect the user's wireless network experience, and can only wait for the user's report or complaint, which makes the wireless network Operation and maintenance students often work in a passive state. In order to solve this problem, this transformation plan deployed an intelligent analysis system for the wireless network for the first time, which supports early warning, fault location, fault analysis, and trend analysis of the wireless environment from the macro to the micro. model has changed to an intelligent operation and maintenance model centered on user experience.
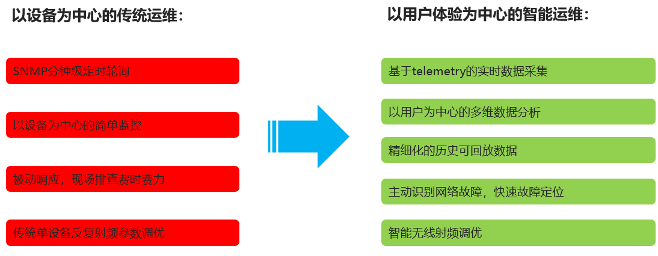
The intelligent operation and maintenance of the wireless network starts from the user experience and takes the overall health of the network as the entry point. The operation and maintenance tools have the key points of fine data collection and display for a single user/terminal, one -key automation of the wireless network, and multi-dimensional intelligent analysis. The ability to help wireless operation and maintenance administrators quickly locate, accurately predict the root cause of problems, and improve user experience. Through the deployed wireless intelligent analyzer, G Bank can view the overall health status of users and predict wireless network problems in advance. When receiving user feedback that the wireless network experience is not good, it can finely view the health of individual users/termin als Degree details, including user health status, online and offline details, terminal radio frequency parameters, AP migration information, interference information, related events, historical traffic curves and other information. At the same time, you can view related device health details for auxiliary analysis.
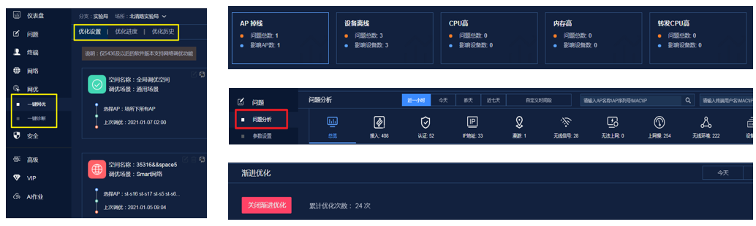
Through wireless user health data and detailed network index information, from experience trends (idle, high quality, poor quality), indicator trends (signal strength, uplink speed selection, downlink speed selection, delay, packet loss rate, retransmission rate) ), problem trends (access, authentication, IP address, roaming, wireless signal, slow Internet access) three-dimensional analysis presents the overall online experience quality of wireless users, locates users with poor quality and their APs, and analyzes and counts the root causes , adjust and optimize in time. For common wireless network problems, the wireless intelligent analyzer can also quickly locate the cause of the problem, such as WLAN co-channel interference problems, remote correlation problems, layer 2 loop problems, etc., which solves the difficulty for oper cation and maintenance personnel to quickly locate wireless network problems problems, and improve the ability to handle wireless problems.
Four. Summary
This intelligent wireless network transformation has achieved significant improvement through the introduction of WI-FI6 technology, increasing network speed and capacity, and bringing users the ultimate wireless network experience; in terms of user experience, innovative deployment of user roam ing, senseless authentication, etc. In terms of security, by standardizing the wireless network architecture design, enabling access and terminal Vlan isolation and other measures, the wireless protection level of the entire network is improved; with the help of intelligent operation and maintenance tools, the wireless network management level is Greatly improved, and according to user needs Make intelligent adjustments to meet the individual needs of special scenarios. In the future, the office network service team of Bank G will continue to work hard to continuously improve wireless network technology and service levels, and provide users with a faster, more stable and secure wireless network experience. Always stand on the user's point of view to create a more convenient and safe experience.