Talk about the five tables and five chains of Iptables, have you learned it?

Talk about the five tables and five chains of Iptables, have you learned it?
overview
iptables is a command-line tool for configuring the Linux kernel firewall. It is based on the kernel's packet filtering framework netfilter and is mainly used to manage packet filtering and NAT rules.
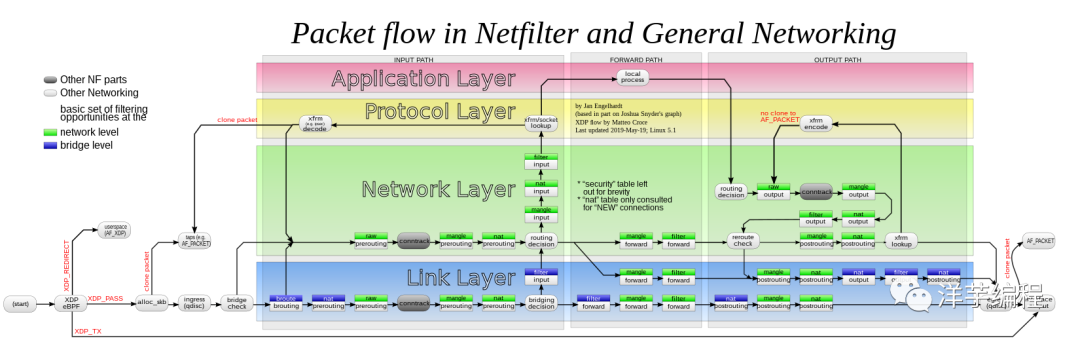
Image source: https://upload.wikimedia.org/wikipedia/commons/3/37/Netfilter-packet-flow.svg
iptables interacts with the packet filtering hooks in the protocol stack to get the job done. These kernel hooks form the netfilter framework. Each packet (received or sent) entering the network system will trigger these hooks when passing through the protocol stack, and the program can process network traffic on some key paths by registering hook functions. iptables-related kernel modules register processing functions at these hook points, so you can configure iptables rules to make network traffic comply with firewall rules.
Understanding iptables is the basis for learning the implementation of network functions in open source projects such as Docker and Kubernetes.
rule
Rules are the conditions predefined by the network administrator. The general definition is that if the packet header meets the current conditions, the packet is processed, otherwise the next judgment condition is executed. The rules are stored in the filter table of the kernel space, and these rules specify Source address, destination address, transport protocol (such as TCP, UDP, ICMP) and service type (such as HTTP, FTP, SMTP), etc. When the packet matches the rule, the kernel will perform specific actions.
The main job of configuring a firewall is to add, modify, and delete rules.
Behavior
action | describe |
ACCEPT | receive packets |
DROP | Discard the data packet. After this action, the detection process will be interrupted directly, and no other rules will be detected. |
REDIRECT | Redirect the packet to another port (PNAT). After this action, continue to compare other rules. This function can be used to implement transparent proxy or to protect application server |
SNAT | source address translation |
DNAT | destination address translation |
MASQUERADE | IP masquerading (NAT), for ADSL |
LOG | logging |
SEMARK | Add SEMARK mark for Intra-Domain Mandatory Access Control (MAC) |
QUEUE | Pass the packet to user space |
REJECT | Intercept the data packet and return the data packet to notify the other party |
RETURN | The firewall stops executing subsequent rules in the current chain and returns to the calling chain to continue detection |
5 strands
Chain is the path for data packets to propagate, and there can be N rules (N >= 0) in each chain. When a data packet reaches a chain, iptables will start to check from the first rule in the chain. If the data packet meets the conditions defined by the rule, the system will perform specific actions, otherwise iptables will continue to check the next rule. If the packet does not match any of the rules in the chain, iptables will process the packet according to the predefined default policy of the chain.
name | describe |
INPUT | Process received packets |
OUTPUT | Process sent packets |
FORWARD | Handle forwarded data packets, often used in |
PREROUTING | Modify the data packets that arrive and have not yet been forwarded, often used in |
POSTOUTING | Modify the data packet before sending, often used |
5 tables
A table has N chains, and a chain has N rules.
Most scenarios only need to use Filter table and NAT table.
Raw table
The Raw table is used to process packets before connection tracking, NAT and routing table processing, and contains 2 built-in chains:
• PREROUTING
• OUTPUT
Because the priority is the highest, if the Raw table is used, after the Raw table is processed, the NAT table and ip_conntrack processing will be skipped, that is, connection tracking, NAT and routing table pre-processing will be avoided.
Filter table
Filter is the default table of iptables, which is used to filter packets. If no table is defined, the Filter table will be used, including 3 built-in chains:
- • INPUT
- • OUTPUT
- • FORWARD
In the Filter table, only the operations of accepting and discarding data packets are allowed, but the data packets cannot be changed.
NAT table
NAT is used to implement network address translation and contains 3 built-in chains:
• PREROUTING
• POST-ROUTING
• OUTPUT
Mangle table
Mangle is used to modify, mark or redirect specified packet headers, including 5 built-in chains:
• INPUT
• OUTPUT
• FORWARD
• PREROUTING
• POST-ROUTING
Security table
Security is used to mark packages with SELinux, thereby affecting the behavior of SELinux or other systems that can interpret SELinux security contexts for processing packages. These tags can be based on individual packets or connections.
Table and chain relationship diagram
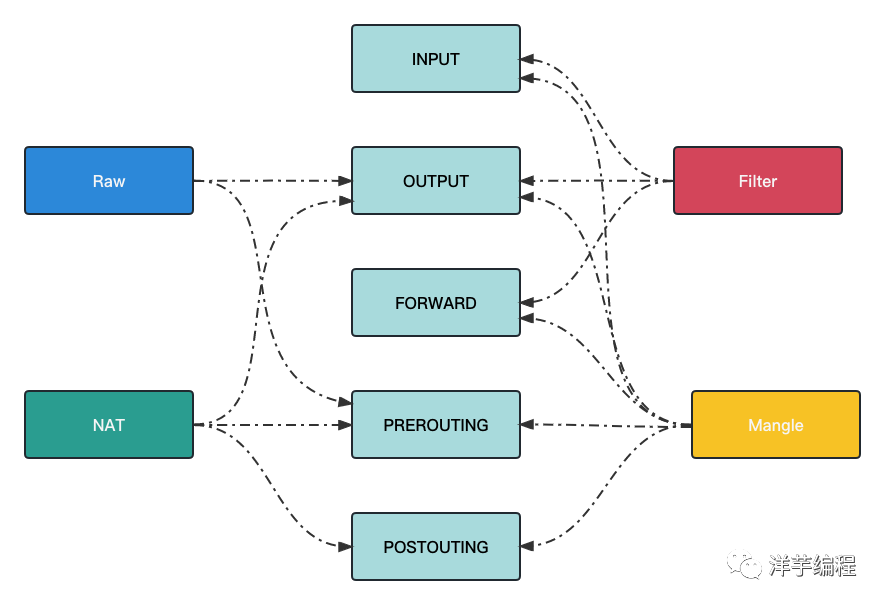
Table and chain relationship diagram
The detection priority of the table
Raw -> Mangle -> Nat -> Filter
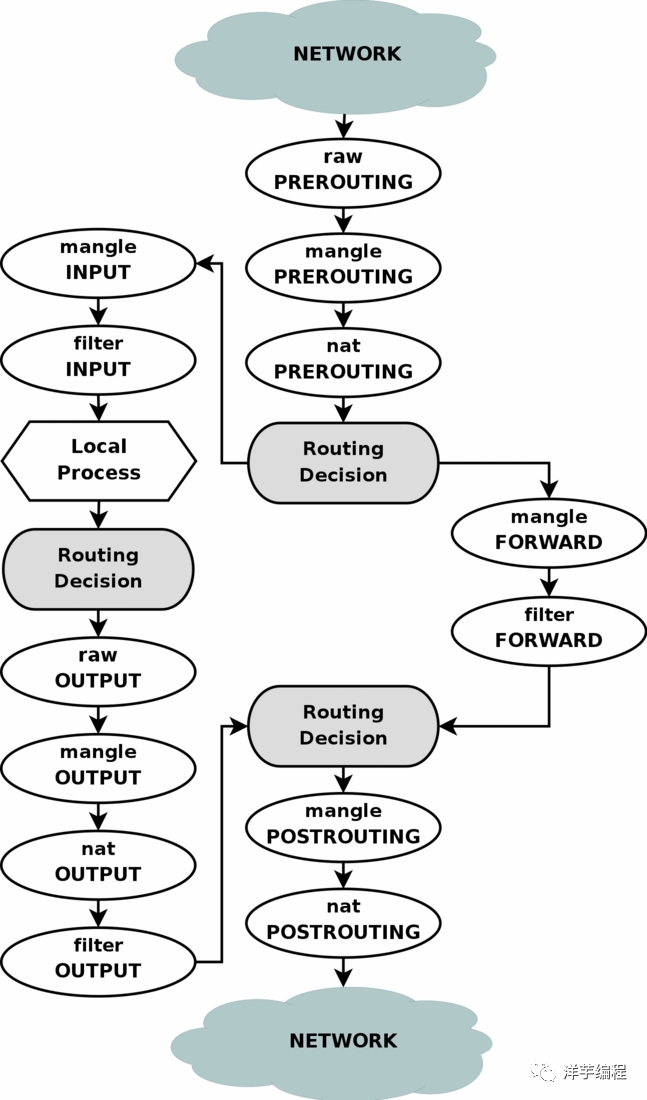
Image source: https://www.frozentux.net/iptables-tutorial/images/tables_traverse.jpg
Any data packet must pass through one of the five chains.
• When a data packet enters the network card, it first enters the PREROUTING chain, and the kernel judges whether it needs to be forwarded according to the destination IP of the data packet
• If the data packet enters the local machine, it will move down the graph and reach the INPUT chain. After the data packet reaches the INPUT chain, any process will receive it, and the program on the machine can send the data packet. The package will go through the OUTPUT chain, and then reach the output of the POSTROUTING chain
• If the packet is forwarded, and the kernel allows forwarding, the packet will go through the FORWARD chain and then reach the output of the POSTROUTING chain
Common commands
view class
# 查看所有防火墙规则
$ iptables --list
# 示例输出如下
Chain DOCKER (8 references)
target prot opt source destination
ACCEPT tcp -- anywhere 172.27.0.2 tcp dpt:10010
ACCEPT tcp -- anywhere 172.22.0.2 tcp dpt:http
ACCEPT tcp -- anywhere 172.29.0.4 tcp dpt:memcached
ACCEPT tcp -- anywhere 172.17.0.2 tcp dpt:redis
ACCEPT tcp -- anywhere 172.17.0.2 tcp dpt:nginx
ACCEPT tcp -- anywhere 172.17.0.4 tcp dpt:8080
ACCEPT tcp -- anywhere 172.17.0.5 tcp dpt:mysql
ACCEPT tcp -- anywhere 172.17.0.5 tcp dpt:http
# 查看 mangle 表规则
$ iptables -t mangle --list
# 查看 nat 表规则
$ iptables -t nat --list- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
Field Name | describe |
target | regular behavior |
prot | protocol |
opt | options |
source | source IP address |
destination | Destination IP address |
Operation class
# 查看说明
$ iptables --help
# 查看命令
iptables -L:查看规则链
# 规则管理命令
iptables -A:在规则链的末尾加入新规则
iptables -D:删除某个规则
iptables -I:在规则链的头部加入新规则
iptables -R:替换规则链中的规则
# 链管理命令
iptables -F:清空规则链
iptables -Z:清空规则链中的数据包计算器和字节计数器
iptables -N:创建新的用户自定义规则链
iptables -P:设置规则链中的默认策略
# 通用匹配参数
-t
对指定的表 table 进行操作
如果不指定此选项,默认的是 filter 表
-p 协议
指定规则的协议,如 tcp, udp, icmp 等,可以使用all来指定所有协议
如果不指定 -p 参数,默认的是 all 值
-s 源地址
指定数据包的源地址
参数可以使IP地址、网络地址、主机名
例如:-s 192.168.1.101 指定IP地址
例如:-s 192.168.1.10/24 指定网络地址
-d 目的地址
指定数据包的目的地址,规则和 -s 类似
-j 执行目标
指定规则匹配时如何处理数据包
可能的值是ACCEPT, DROP, QUEUE, RETURN 等
-i 输入接口
指定要处理来自哪个接口的数据包,这些数据包将进入 INPUT, FORWARD, PREROUTE 链
例如:-i eth0指定了要处理经由eth0进入的数据包
如果不指定 -i参数,那么将处理进入所有接口的数据包
如果指定 ! -i eth0,那么将处理所有经由eth0以外的接口进入的数据包
如果指定 -i eth+,那么将处理所有经由eth开头的接口进入的数据包
-o 输出
指定了数据包由哪个接口输出,这些数据包将进入 FORWARD, OUTPUT, POSTROUTING链
如果不指定-o选项,那么所有接口都可以作为输出接口
如果指定 ! -o eth0,那么将从eth0以外的接口输出
如果指定 -i eth+,那么将仅从eth开头的接口输出
# 扩展参数
-sport 源端口
针对 -p tcp 或者 -p udp,默认情况下,将匹配所有端口
可以指定端口号或者端口名称、端口范围,例如 –sport 22, –sport ssh,–sport 22:100
从性能上讲,使用端口号更好, /etc/services 文件描述了映射关系
-dport 目的端口
规则和 –sport 类似
-tcp-flags TCP 标志
针对 -p tcp
可以指定由逗号分隔的多个参数
取值范围:SYN, ACK, FIN, RST, URG, PSH, ALL, NONE
-icmp-type ICMP 标志
针对 -p icmp
icmp-type 0 表示 Echo Reply
icmp-type 8 表示 Echo- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
Command option input order
iptables -t 表名 <-A/I/D/R> 规则链名 [规则号] <-i/o 网卡名> -p 协议名 <-s 源IP/源子网> --sport 源端口 <-d 目标IP/目标子网> --dport 目标端口 -j 动作- 1.
example
The following commands are used with caution in a production environment.
View the added iptables rules
$ iptables -L -n -v
Chain INPUT (policy DROP 48106 packets, 2690K bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
191K 90M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
1499K 133M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4364K 6351M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
6256 327K ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3382K packets, 1819M bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
Clear all current rules and counts
$ iptables -F # 清空所有的防火墙规则
$ iptables -X # 删除用户自定义的空链
$ iptables -Z # 清空计数- 1.
- 2.
- 3.
set default rules
$ iptables -P INPUT DROP # 配置默认的不让进
$ iptables -P FORWARD DROP # 默认的不允许转发
$ iptables -P OUTPUT ACCEPT # 默认的可以出去- 1.
- 2.
- 3.
open designated ports
$ iptables -A INPUT -s 127.0.0.1 -d 127.0.0.1 -j ACCEPT # 允许本地回环接口(即运行本机访问本机)
$ iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT # 允许已建立的或相关连的通行
$ iptables -A OUTPUT -j ACCEPT # 允许所有本机向外的访问
$ iptables -A INPUT -p tcp --dport 22 -j ACCEPT # 允许访问22端口
$ iptables -A INPUT -p tcp --dport 80 -j ACCEPT # 允许访问80端口
$ iptables -A INPUT -p tcp --dport 21 -j ACCEPT # 允许ftp服务的21端口
$ iptables -A INPUT -p tcp --dport 20 -j ACCEPT # 允许FTP服务的20端口
$ iptables -A INPUT -j reject # 禁止其他未允许的规则访问
$ iptables -A FORWARD -j REJECT # 禁止其他未允许的规则访问- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
whitelist
$ iptables -A INPUT -p all -s 192.168.1.0/24 -j ACCEPT # 允许机房内网机器可以访问
$ iptables -A INPUT -p all -s 192.168.140.0/24 -j ACCEPT # 允许机房内网机器可以访问
$ iptables -A INPUT -p tcp -s 183.121.3.7 --dport 3380 -j ACCEPT # 允许 183.121.3.7 访问本机的 3380 端口- 1.
- 2.
- 3.
blacklist
iptables -I INPUT -s 123.45.6.7 -j DROP # 屏蔽单个 IP
iptables -I INPUT -s 123.0.0.0/8 -j DROP # 屏蔽 IP 网段 从 123.0.0.1 到 123.255.255.254
iptables -I INPUT -s 124.45.0.0/16 -j DROP # 屏蔽 IP 网段 从 123.45.0.1 到 123.45.255.254
iptables -I INPUT -s 123.45.6.0/24 -j DROP # 屏蔽 IP 网段 从 123.45.6.1 到 123.45.6.254- 1.
- 2.
- 3.
- 4.
Prevent SYN flood attacks
$ iptables -A INPUT -p tcp --syn -m limit --limit 5/second -j ACCEPT- 1.
summary
In the process of writing this article, the author found that the Chinese content almost said four tables and five links. I don’t know if the author deliberately skipped the Security table, or the homogeneity caused by plagiarism is too serious. Although the Security table is not a common feature, we cannot ignore its existence.
Reference
- • Traversing of tables and chains[1]
- • iptables(8) - Linux man page[2]
- • iptables[3]
- • Detailed explanation of iptables[4]
- • iptables command[5]
- • In-depth understanding of iptables and netfilter architecture[6]
- • iptables basic knowledge and command quick reference
quote link
[1] Traversing of tables and chains: https://www.frozentux.net/iptables-tutorial/iptables-tutorial.html#TRAVERSINGOFTABLES[2] iptables(8) - Linux man page: https://linux.die.net/man/8/iptables
[3] iptables: https://wiki.archlinuxcn.org/wiki/Iptables
[4] Detailed explanation of iptables: https://lixiangyun.gitbook.io/iptables_doc_zh_cn/
[5] iptables command: https://wangchujiang.com/linux-command/c/iptables.html
[6] Deep understanding of iptables and netfilter architecture: https://arthurchiao.art/blog/deep-dive-into-iptables-and-netfilter-arch-zh/