Industrial wireless network physical layer security technology

Industrial wireless network physical layer security technology
1. Industrial wireless network development and security issues
With the continuous development of Industry 4.0, there is a greater demand for communication systems and higher standards, requiring more efficient, reliable, fast and flexible communication systems. In the current industrial production environment, wired communication technology is mainly used, which has the advantages of high reliability, strong anti-interference and high security, but has high installation and maintenance costs, complex layout and poor scalability disadvantage. Compared with wired communication technology, wireless communication technology breaks these limitations. It has flexibility, scalability and multi-functionality, and can adapt to industrial development. At the same time, wireless communication technology does not require complicated wiring, which greatly reduces the cost of network maintenance. [1]. But these advantages are accompanied by a fatal disadvantage, wireless communication technology is unsafe communication. The reason for the poor security of wireless communication technology lies in the openness of its transmission, so the signal is easily intercepted or interfered by others maliciously [2]. Therefore, it is necessary to take security measures against the above problems. The premise of the security measures adopted must meet the requirements of industrial wireless networks in terms of delay and reliability, but these strict requirements also make most traditional security protection methods unusable. For example, latency requirements conflict with complex encryption architectures, so control latency requirements are strictly controlled within a few milliseconds or even lower. It is also reflected in the robustness of the encryption method, which is generally related to the size of the information packet, and in many industrial situations, the information packet size is very short, resulting in poor robustness. There are also some types of attacks related to lower network layers, such as jamming attacks. In such cases, encryption methods cannot deal with it, and security tools at PHY layer and MAC layer are required [1].
2. Attack threats on the physical layer and MAC layer of the wireless system
Wireless is an inherently insecure field. Radio propagation exposes the process of exchanging information between authorized users to active and passive malicious threats. The general requirements of wireless security are confidentiality, authenticity, availability and integrity [2], as shown in Figure 1.
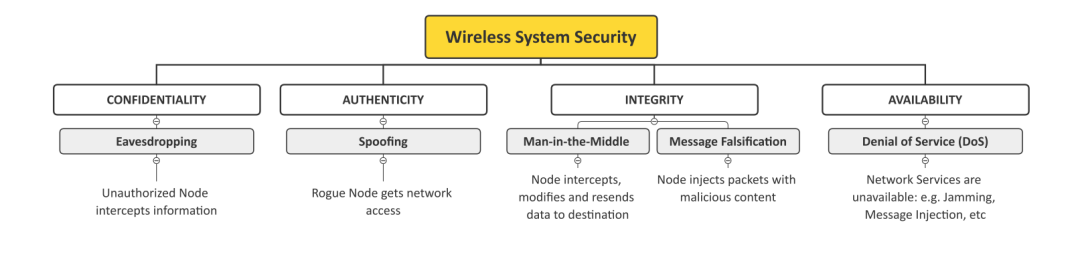
Figure 1 Wireless Communication Functions and Targeted Attacks
There are two types of attacks related to the physical layer of wireless communication systems: eavesdropping attacks and jamming.
Eavesdropping is easier to achieve than other attacks due to the broadcast nature of wireless transmissions. The accessibility of the transmitted waveform to the listening receiver makes it more difficult to prevent unauthorized access to the wireless content. Eavesdropping may be possible without affecting the intended transmission link, which would make the breach of confidentiality undetectable and thus more harmful [3].
Countermeasures to prevent eavesdropping are divided into two categories: encryption technology and enhanced channel advantage technology. Encryption techniques are widely used in general wireless systems, usually using protocols that belong to the upper layers of the OSI model. The encryption/decryption process is done through an algorithm that may involve the exchange of different hash keys between the server component and the secure infrastructure device, specific to the secure infrastructure. These algorithms are often complex and cause significant processing delays. In a nutshell, CSI-based encryption uses channel reciprocity to obtain a secret shared key at both ends of the communication. This fact is a significant challenge because the assumption of reciprocity is based on quasi-static channels, a condition that cannot be guaranteed in wireless links. The other is that the attacker can also imitate the CSI of the main communication link to steal [4]. The second protection technology is to enhance the channel advantage, that is, to effectively improve the secrecy rate of the main communication channel by reducing the eavesdropping channel or increasing the capacity of the main channel. Examples of these techniques are artificial noise generation, secure beamforming precoding, cooperative secure transmission, and power allocation.
Jamming is a special case of DoS attacks. A jammer transmits a specific waveform (noise-like, periodic, aperiodic, pulsed, or continuous) with the intention of disrupting communications between legitimate nodes in the network. The physical layer jamming technology can be combined with the MAC layer jamming technology to improve attack efficiency. Against jamming attacks, techniques to improve the robustness of communication systems include spread spectrum (direct sequence, frequency hopping, bandwidth hopping, and parallel sequences), ultra-wideband modulation, power control, and multi-antenna systems.
MAC layer attacks can be classified into MAC forgery, MAC spoofing, MAC identity theft, MAC man-in-the-middle and MAC interference. MAC forgery is the use of legitimate MAC addresses for malicious purposes. MAC spoofing is to change the original MAC address of the device to hide its true identity and pretend to be a legitimate node to obtain authorization to access the destination device in the network. MAC identity theft is when malicious nodes eavesdrop on network node traffic and steal MAC identities to access confidential information on victim nodes. MAC man-in-the-middle attack is to intercept the addresses of two legitimate nodes, pretend to be the relay of the two, and steal the data exchanged by the two. In addition, interference can also be performed at the MAC layer. To interfere with the MAC layer, it is necessary to understand the protocol of the system, which can improve the severity and efficiency of the attack. Interference with the PHY layer also reduces energy consumption [5]. The current jamming methods are divided into two categories, statistical jammers and protocol-aware jammers. Statistical jammers observe the distribution time between packet arrivals and effectively disrupt communications. The usual approach to counteract statistical disturbers is to randomize the transmission schedule or data transfer size, but both approaches involve associated delays, hardware requirements (memory), and high overhead [6]. Protocol-aware jammers know the details of the MAC layer and can block legitimate node access to communication channels. There are many countermeasures to solve, which can be combined with hidden node wake-up time, delivery time, frame length or channel technology for communication [7]. Another type of MAC interference is network injection, where malicious nodes establish unwanted ad-hoc paths to some victim nodes and send useless traffic, thus wasting wireless bandwidth and resources of the victim network.
3. PHY Layer Security in Factory Automation Wireless Systems
Too many security measures in current wireless communication systems involve complex operations and upper-layer protocols, which will cause communication performance that does not meet the requirements of factory automation. The latency of algorithms and processes for security measures should always be kept below the specifications of factory automation wireless systems. Figure 1 presents a classification of security techniques for PHY-specific attacks. The classification covers three areas: spoofing, jamming and eavesdropping.
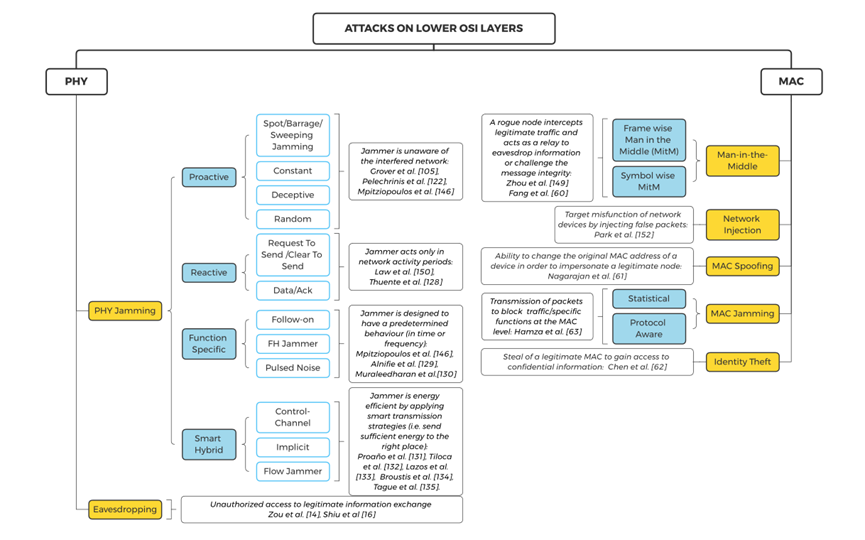
Figure 2 Taxonomy of PHY layer security technologies
The basic measure to prevent eavesdropping attacks in wireless communication is information-theoretic security. Secret key management requires a dedicated architecture, which is not always feasible in sensor-actuator networks. Wyner solved this problem by proposing a confidential wiretapping model [8]. The model is applicable to Gaussian channels, fading channels, and MIMO communication systems. PHY security technology uses artificial noise to disrupt the eavesdropper's channel without affecting the communication link. Using multiple antennas or cooperating relays can generate noise for selective jamming. Beamforming can also be a tool to increase the protection of wireless systems [9]. Basic goal: improve the desired link performance while creating interference (reducing SNR, creating interference, etc.) on the eavesdropping link, thereby maximizing the confidentiality of the communication. Encryption is an alternative method that guarantees the confidentiality of information exchanged over wireless links. Although the upper-layer cryptography uses complex algorithms to make the decryption time for eavesdroppers very long, the performance of the transmission will also be affected. Therefore, PHY encryption can take advantage of the unpredictable characteristics of the propagation channel to maximize security [10]. PHY encryption does not require expensive computing resources, and the level of security will only depend on the behavior of the propagation channel. Success in this field depends on two factors: key generation and the agreement process between nodes. On the key generation problem, communication devices can measure wireless channel characteristics (usually channel impulse response or received signal strength) and use them as a shared source of randomness to create a shared key. In the key generation process, assuming that the channel is reciprocal between nodes, theoretically, the key obtained at each end will be the same. At the same time, generating secret bits at a high rate requires fast and random channel changes in order to obtain a sufficiently long key with minimal delay in terms of data transmission speed. Therefore, efficient and robust key generation depends heavily on the propagation conditions between nodes.
Spoofing attacks aim to impersonate legitimate nodes. Countermeasures against spoofing at the PHY layer take advantage of the unique capabilities of each wireless communication link. The basic principle of PHY anti-spoofing is the expectation of anomalies in the propagation channel characteristics between two legitimate nodes. System nodes will exchange and analyze predefined waveforms or measurement propagation channels. The results of the analysis are unique to their channel, therefore, no malicious node can fake a legitimate identity to fool any legitimate node. Identity can be defined using each device's unique hardware fingerprint [10]. The reference fingerprints and associated available metrics are varied: jitter, pulse ramp characteristics, clocks, transients, waveform impairments, modulation or combinations thereof. Second, another approach exploits propagation channel variables univocally associated with a node's wireless link to identify legitimate nodes. A malicious node trying to spoof communication will present different propagation channel parameters if it is located at a sufficiently far distance from any legitimate nodes. The most straightforward schemes use RSSI variation statistics as signatures, while more sophisticated strategies use CSI data [11].
A large number of PHY security techniques in wireless systems are devoted to dealing with jamming attacks. Radio frequency (RF), spread spectrum, time synchronization, and combined PHY/MAC techniques. Spread spectrum is one of the most widely used protection strategies, including traditional frequency hopping spread spectrum (fh-ss), direct sequence spread spectrum (ds-ss) and various combinations. Other spreading strategies such as bandwidth hopping spread spectrum (bh-ss) are also under study. Parallel Sequence Spread Spectrum is the latest solution for industrial communication environments. Ultra Wideband (UWB) relies on principles similar to spread spectrum. There is no consensus on the practical use of ds-ss and UWB for preventing interference. Ds-ss hardware complexity, power consumption, and transmission power limitations of currently available standards (IEEE 802.15.4) are major technical drawbacks. Other anti-jamming techniques are related to the radio frequency aspects of protected communication systems. For example, adjusted transmit power, antenna polarization and directional transmission. Time synchronization protects communications from reactive jammers. These attackers attempt to increase energy efficiency by creating interference at selected points in time when communications occur. A reactive jammer must listen to a channel for a certain amount of time to see if a signal is being transmitted. Therefore, the inherent time spent by the attacker checking the channel can be exploited by the communication system to avoid jamming [12]. Finally, some strategies combine PHY and MAC antijamming tools by modifying frame and packet characteristics. In all cases, the goal is to hide the MAC protocol functionality from smart jammers (MAC-level jamming). Another process is to increase data protection against time-selective short disturbances. Other antijamming solutions address the problem in multi-node environments by isolating blocked areas and blocked nodes. In this case, the system uses the remaining nodes to maintain overall network functionality as much as possible.
4 Conclusion
At present, wireless networks are more and more widely used in industrial fields, and security issues are particularly prominent. This paper sorts out the security threats and security measures currently faced in the physical layer security of wireless security, so as to deepen the understanding of the physical layer security of industrial wireless networks.
references
[1] P. Angueira et al., "A Survey of Physical Layer Techniques for Secure Wireless Communications in Industry," in IEEE Communications Surveys & Tutorials, vol. 24, no. 2, pp. 810-838, Secondquarter 2022.
[2] Y. Zou, J. Zhu, X. Wang and L. Hanzo, "A Survey on Wireless Security: Technical Challenges, Recent Advances, and Future Trends," in Proceedings of the IEEE, vol. 104, no. 9 , pp. 1727-1765, Sept. 2016.
[3] Y.-S. Shiu, SY Chang, H.-C. Wu, SC-H. Huang, and H.-H. Chen, “Physical layer security in wireless networks: A tutorial,” IEEE Wireless Commun. , vol. 18, no. 2, pp. 66–74, Apr. 2011.
[4] J. Hua, S. Jiang, W. Lu, Z. Xu, and F. Li, “A novel physical layer encryption algorithm based on statistical characteristics of time-selective channels,” IEEE Access, vol. 6, pp. . 38225–38233, 2018.
[5] T. Hamza, G. Kaddoum, A. Meddeb, and G. Matar, “A survey on intel-ligent MAC layer jamming attacks and countermeasures in WSNs,” in Proc. 84th IEEE Conf. (VTC-Fall), Montreal, QC, Canada, Sep. 2016, pp. 1–5.
[6] A. Hussain, NA Saqib, U. Qamar, M. Zia, and H. Mahmood, “Protocol-aware radio frequency jamming in Wi-Fi and commercial wireless networks,” J. Commun. Netw., vol. 16 , no. 4, pp. 397–406, Aug. 2014.
[7] YW Law, M. Palaniswami, LV Hoesel, J. Doumen, P. Hartel, and P. Havinga, “Energy-efficient link-layer jamming attacks against wire-less sensor network MAC protocols,” ACM Trans Sens. Netw .,vol.5,no. 1, p. 6, Feb. 2009.
[8] AD Wyner, “The wire-tap channel,” Bell Syst. Techn. J., vol. 54, no. 8, pp. 1355–1387, Oct. 1975.
[9] F. Zhu and M. Yao, “Improving physical-layer security for CRNs using SINR-based cooperative beamforming,” IEEE Trans. Veh. Technol., vol. 65, no. 3, pp. 1835–1841, Mar. . 2016.
[10] J. Zhang, TQ Duong, A. Marshall, and R. Woods, “Key generation from wireless channels: A review,” IEEE Access, vol. 4, pp. 614–626, 2016.
[11] K. Zeng, K. Govindan, and P. Mohapatra, “Non-cryptographic authen-tication and identification in wireless networks [security and privacy inmerging wireless networks],” IEEE Wireless Commun., vol. 17, no. 5 ,pp. 56–62, Oct. 2010.
[12] S. Fang, Y. Liu, and P. Ning, “Wireless communications under broad-band reactive jamming attacks,” IEEE Trans. Dependable Secure Comput., vol. 13, no. 3, pp. 394–408, May/Jun. 2016.