Can't catch the three-way handshake? Come grab a bag with me!

Can't catch the three-way handshake? Come grab a bag with me!
Some time ago, I was busy with a robot communication project, in which an important protocol family was TCP/IP (Transmission Control Protocol/Internet Protocol, Transmission Control Protocol/Internet Protocol). I always think that the TCP/IP protocol is really designed. It is so ingenious, it can be said to be the greatest communication protocol on the planet, ranging from WeChat instant messaging to aerospace and other automatic control industries, it is everywhere, it is with TCP/IP that we Every Internet message sent can reach the other party safely and undamaged (for example, have you ever thought that you are in Beijing, open WeChat to send a blessing phrase to a friend in Shanghai, what happened to your message during this period, and why it is accurate? ground), a TCP/IP protocol, half of the history of computer networks, so I think every computer practitioner or computer-related practitioner should take some time to study the TCP/IP protocol.
The road is simple, today we use a packet capture tool Wireshark to capture a data packet, and then peel it off, and gradually uncover the mystery of TCP/IP!

In December 1997, US President Bush awarded the US National Medal of Technology to Robert Kahn (middle), the father of TCP/IP.
The Internet originated from a decentralized command system that the U.S. Department of Defense prepared to study during the U.S.-Soviet struggle for hegemony. It consists of countless nodes. When some nodes are destroyed, they can still communicate with each other through other nodes. It is a topological structure. The information you send from Beijing to Shanghai can take many paths. The magic of TCP/IP is that it can make your information arrive accurately.
What is a "protocol"? The original meaning of "Xie" refers to the cooperation of many people, and the latter "Yi" means a style of writing in ancient Chinese, so the combination is a style of writing that many people cooperate and abide by, and later extended to the mutual agreement of both parties to abide by. of a rule. There are many agreements in life, such as the tripartite agreement you signed when you just graduated, and the lease agreement when you rented a house. Let’s go a little further. After Qin Shihuang unified China, in order to facilitate national exchanges, he formulated the "cars on the same track, books on the same text" "rule, this should be the earliest national standard in Chinese history. It is an agreement that both parties must abide by.
With the agreement, our communication is greatly facilitated. For example, when we make a call, we usually say "Hello, hello". After the other party confirms the answer, it means that both parties are indeed connected, and then start a formal call. The same is true for TCP. In the process of establishing a connection, TCP needs to perform a three-way handshake, and the two parties will communicate with each other after they are fully confirmed:
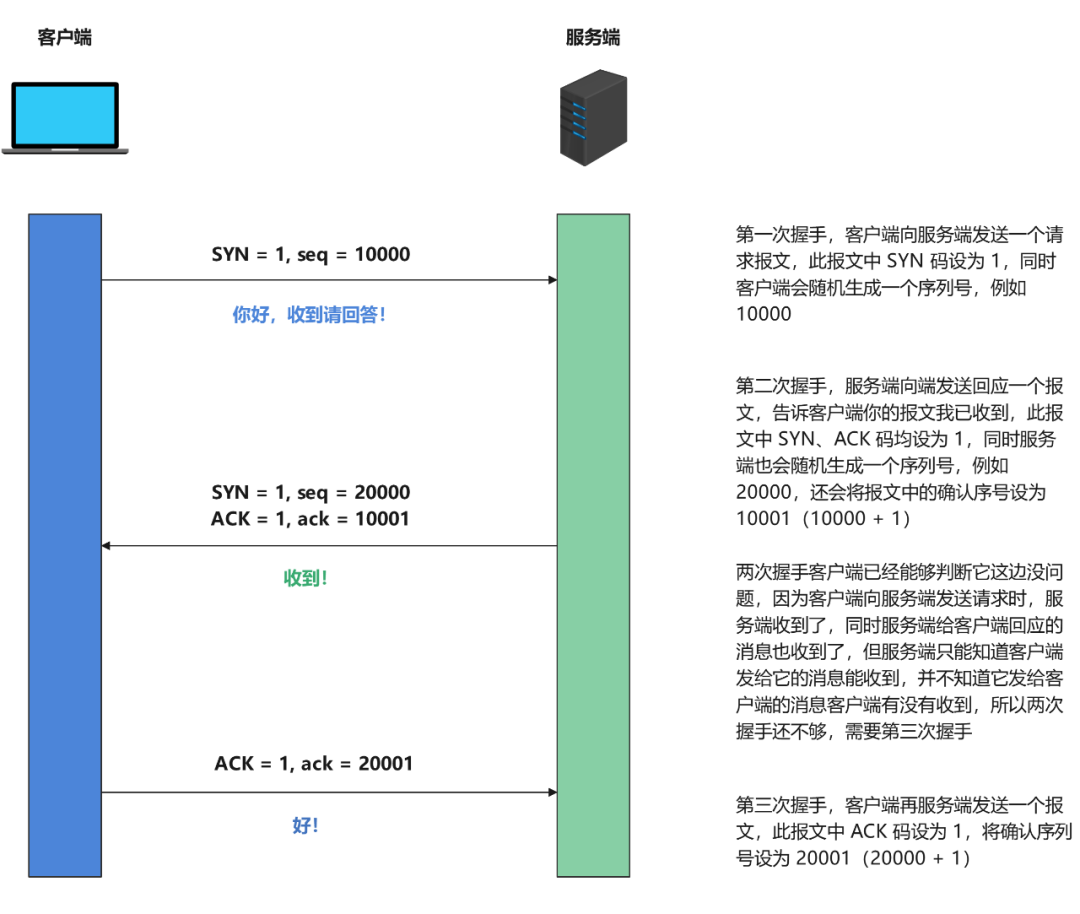
Three-way handshake diagram
With the message of this picture, let's go on a bag grabbing trip!
Preparations before packet capture
The first step, first of all, we download a packet capture software Wireshark, this software Baidu, there are many online, just download it directly;
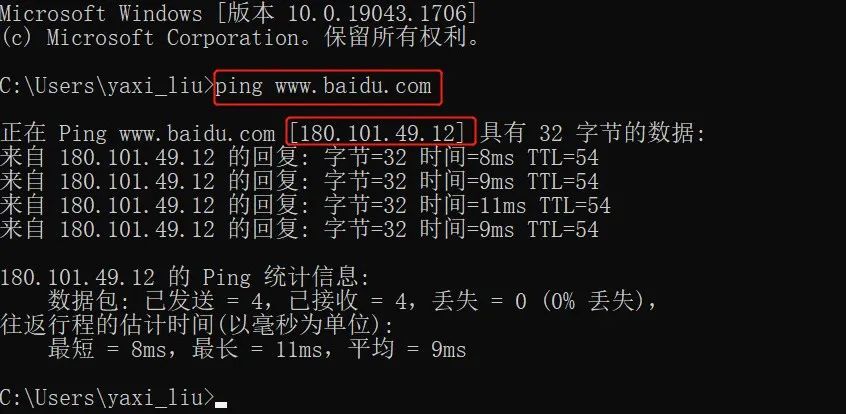
The second step, and then we ping Baidu’s domain name on our computer: www.baidu.com, so that we can know the IP address of Baidu’s server. Of course, Baidu must have more than one server in the country, so the address everyone pings out It may be different. For example, I pinged 180.101.49.12.
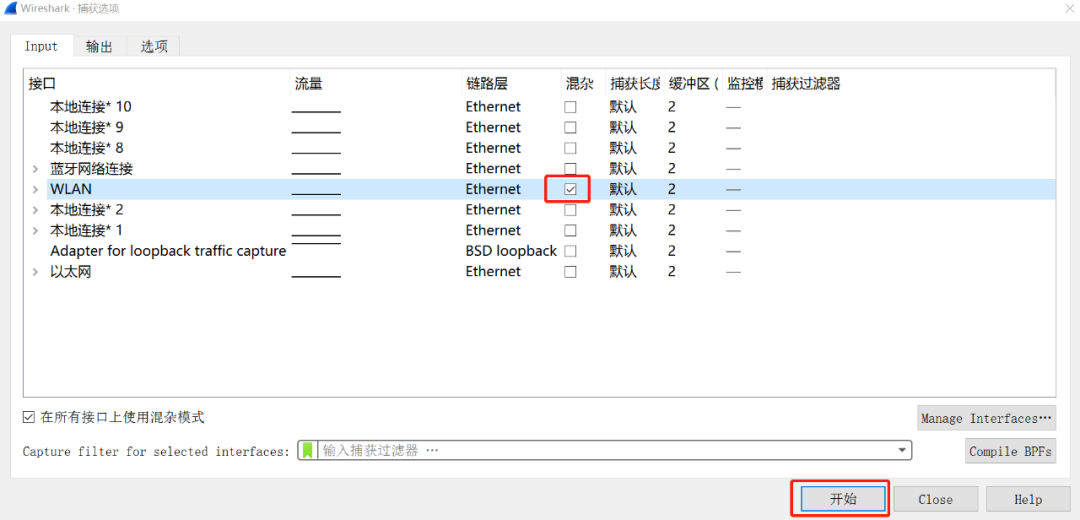
The third step, we open the packet capture software, select your network interface in the options, and then click Start, Wireshark will start to capture packets for you;
The fourth step, we open the browser, enter the IP address of the Baidu server that we just pinged, enter the address bar and press Enter, and then open the Baidu homepage. In fact, the URL we usually enter is also converted into an IP after being parsed by the DNS server. visited. That's right, we captured the message information of both parties after typing Enter by visiting a Baidu website.
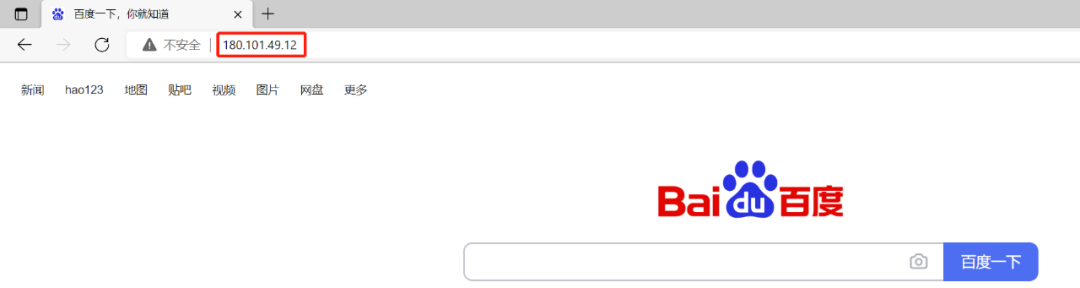
In the fifth step, we enter the ip.addr == 180.101.49.12 and tcp command in the search box of the packet capture software to help us filter out redundant information:
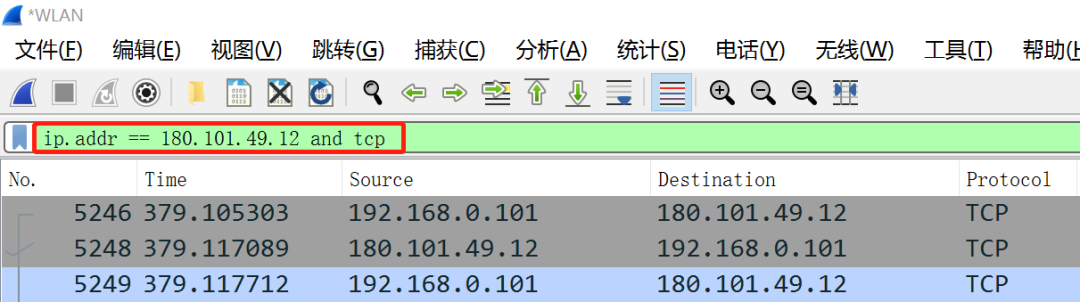
Well, it can be seen that we have captured a lot of information, but we only need the first three, because the first three are the message information transmitted between the two parties during the process of establishing a connection (three-way handshake).
Before analyzing these three messages, let's recall the message structure in each layer of the TCP/IP network model:
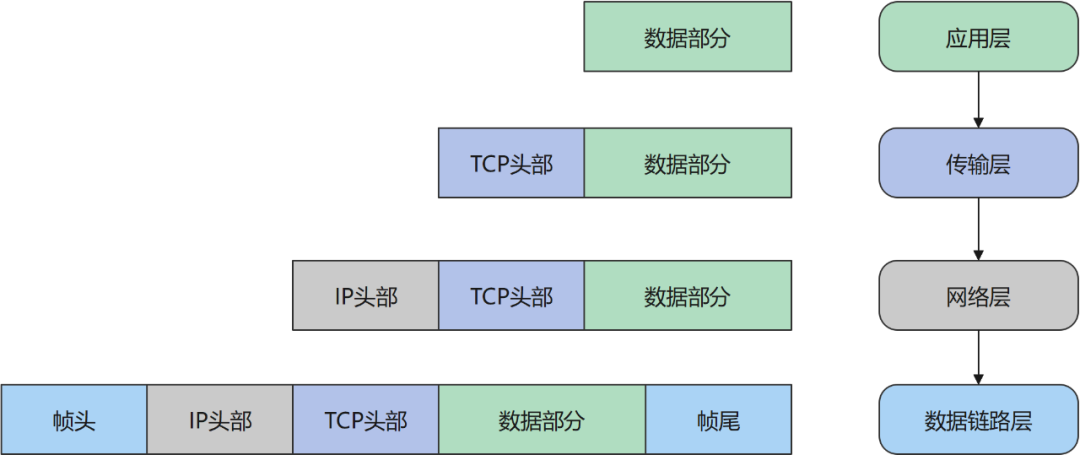
Each layer model adds a header to its own data and sends it to the next layer:
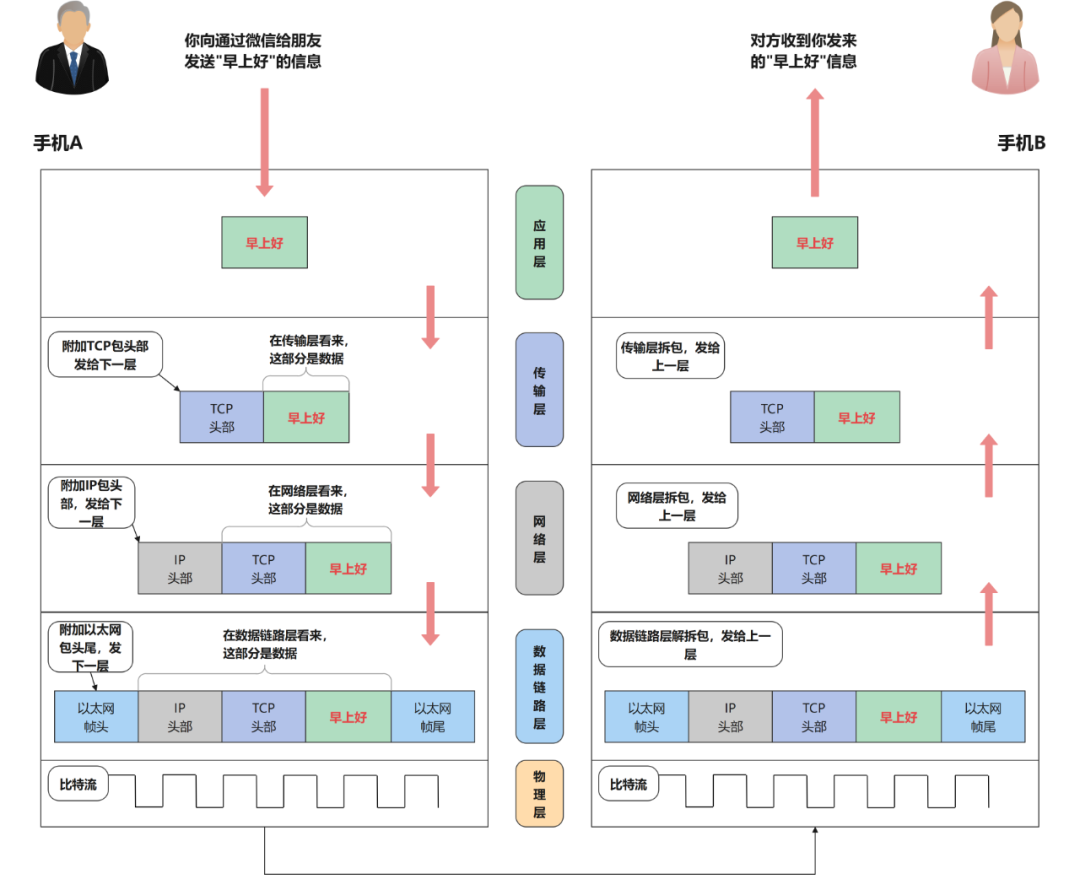
This is the model of WeChat sending messages (all TCP/IP protocols are like this). Of course, WeChat is definitely not directly transmitted end-to-end to another mobile phone, but first transmitted to the Tencent server, and then retweeted to the other party, but the principle is the same of.
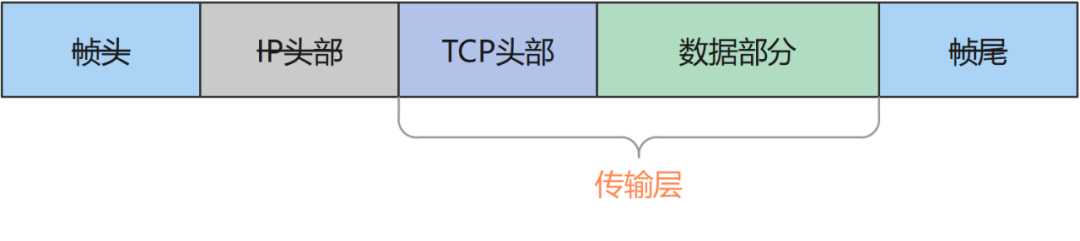
It can be seen that each layer is encapsulated data, which is processed (usually with a header) and then transmitted to the next layer, and finally transmitted to the other party's computer by the transmission medium of the physical layer (such as optical fiber), and the other party receives it and returns it. Come over and analyze, peel off the header of each layer, and finally reveal the data part, which is the data we really want. Therefore, the packets we capture are all in the bottom Ethernet frame, including the data packets of the frame header, frame tail, IP header, and TCP header, so we must first analyze from the last layer.
data link layer
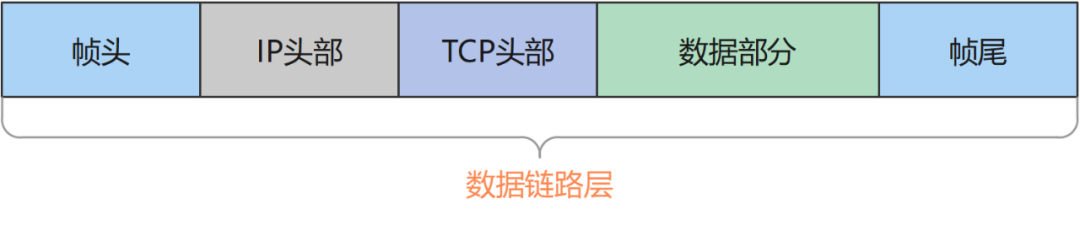
The header structure of the Ethernet frame we received at the data link layer is as follows (for the convenience of description, the width and bit length of the picture below are not drawn to scale):
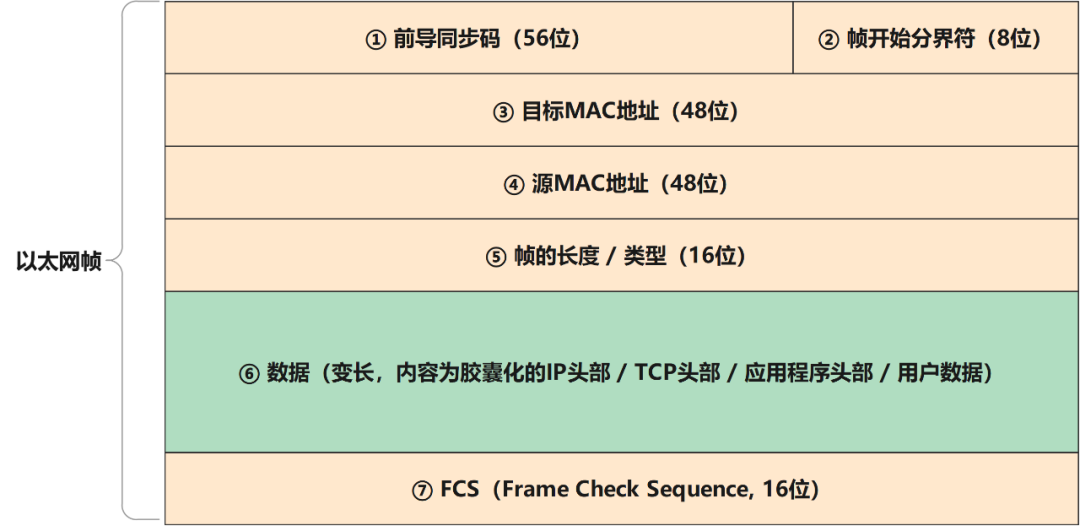
Briefly explain the meaning of several fields:
- Preamble
Remind the receiving system that a frame is coming, write 10101010 seven times;
- start of frame delimiter
Indicates that the transmission of the frame officially starts from the next datagram, and the sequence of binary numbers is 10101011;
- Frame length/type
The content is the frame length (in bytes) or the information handed over to the upper layer protocol. The specific content depends on the type of Ethernet.
Let's first look at the data of the first handshake
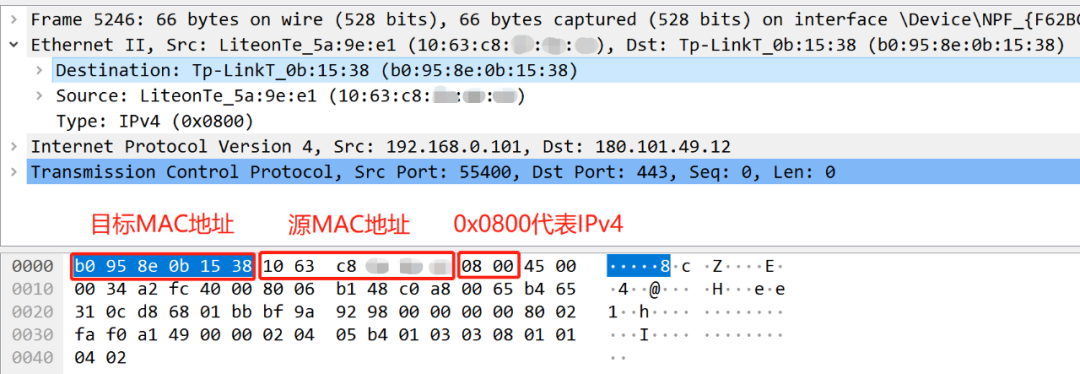
The first red box b0 95 8e 0b 15 38 represents the target MAC address, which is the network card address of Baidu server;
The second red box 10 63 c8 ff ff ff represents the source MAC address, which is the network card address of my own computer. The last three bytes ff ff ff are my virtual ones, including the mosaic in the above picture. Why, Because I am afraid that hackers will attack my computer after knowing the address of my network card;
The third red box 08 00 represents the IPv4 protocol.
Wait, you may ask, why are the preamble synchronization code and frame start delimiter of the frame header not displayed?
This is because the network card at the physical layer first removes the preamble synchronization code and the frame start delimiter, and then performs a CRC check on the frame. If the frame checksum is wrong, the frame is discarded. If the checksum is correct, it is judged whether the destination hardware address of the frame meets its receiving conditions (the destination address is its own physical hardware address, broadcast address, receivable multicast hardware address, etc.), and if so, the frame is handed over to " Device Driver" for further processing. At this time, our packet capture software can capture the data. Therefore, the packet capture software captures data other than the preamble synchronization code, frame start delimiter, and FCS.
Network layer
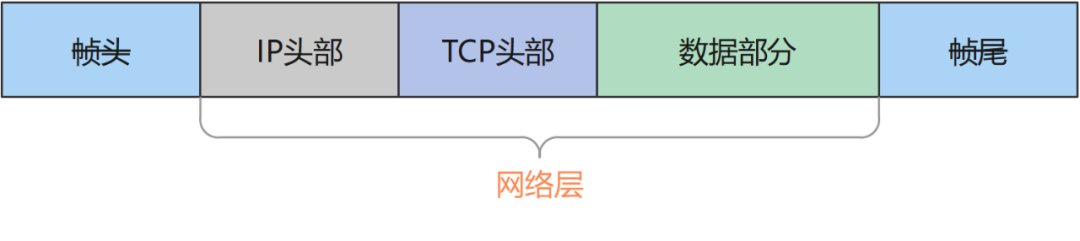
Let's first look at the network layer, which is the header structure of the IP layer:
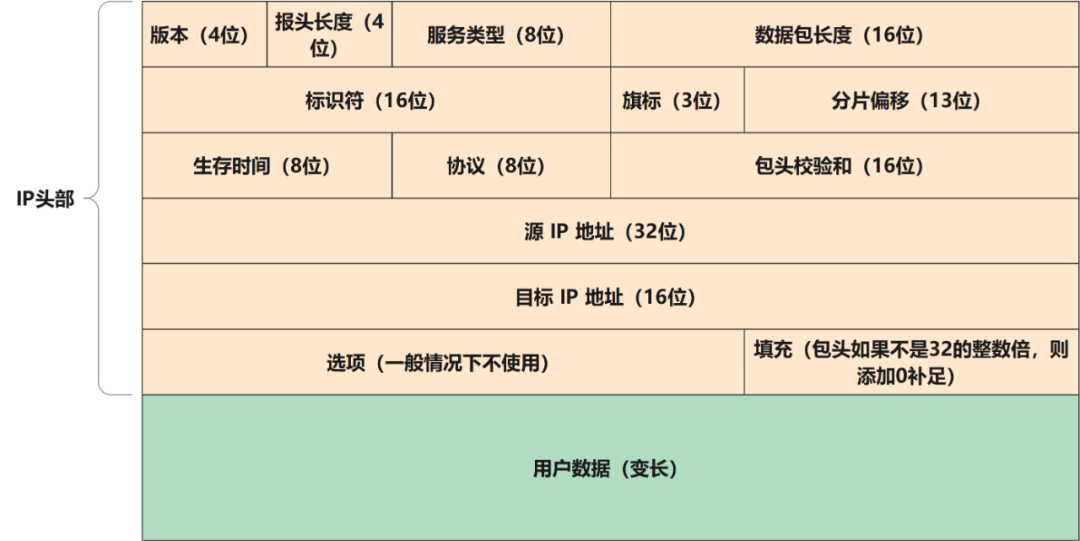
First, let’s briefly explain the meaning of each field:
- version
If it is IPv4, fill in 4, if it is IPv6 (of course, the structure of the header is different from that of IPv4), then fill in 6.
- Header Length
The size of the IP header, the header length refers to the total length of the IP header, because there is an optional part of the Option, usually 20 bytes, ranging from 20 to 60 bytes, note that the unit of this field is a 32-bit word (1 A 32-bit word is 4 bytes), so when the length of the ip header is 1111 (15), it is a maximum of 60 (15*4) bytes. It must be noted that the unit of this field is special and it is easy to make mistakes.
- Service Type (Differentiated Services Field)
Displays the priority when sending messages.
- Total length of data packet (Total Length)
The overall size of the IP header and data, indicating the total length of the sum of the IP header and data. The total length is 16 bits, and the maximum length of a data is 65535 bytes; the link only allows 1500 bytes, if it exceeds, MTU fragmentation is required. A data packet is composed of IP header and data, and the IP header is 20---60 bytes, so there will be no pure data in a data packet exceeding 1480 bytes.
- Identifier (Identification)
The value used when restoring the fragmented IP packet, and the flag field and offset field are used for IP packet fragmentation. If the size of the original packet exceeds the MTU (<1480B), the original data must be fragmented. Each fragment is smaller than the MTU. The fragmented packets of the same original file are marked with the same mark, which is also used to determine whether the traffic comes from the same host. The IP software maintains a counter in memory. Every time a data packet is produced, the counter is incremented by 1 and assigned to the identification field. After the data message is fragmented, the identification value of each fragment is the same as that of the original data packet, and the fragments with the same identification value at the receiving end can finally be correctly reassembled into the original data.
- Flags
Information about packet segmentation:
the first bit is not used;
The second bit is not fragmented (DF), when the DF bit is 1, it means that the router cannot fragment the packet; the third bit is multi-fragmented (MF), when the router fragments the packet, except for the last fragment The MF bit of the slice is set to 0, and the MF bit of all other slices is set to 1, so that the receiver will not receive the slice until the MF bit is 0.
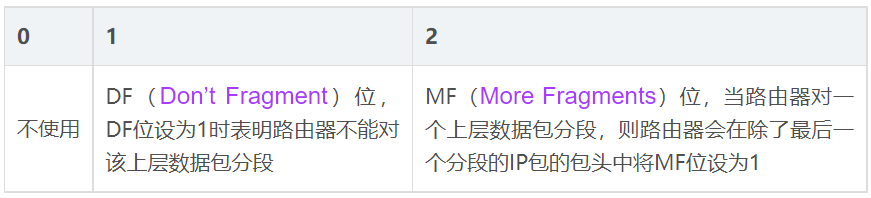
For example, if the packet is split into two segments, the first flags will be 101 and the second flags will be 100.
- Fragmentation offset
The order of the data to be split identifies the position of the slice in the group.
- Time to live (TTL)
The maximum number of routers allowed to pass through, that is, how many hops a data packet can pass through. The default maximum TTL value of different operating systems will be different. The purpose is to prevent IP data from being forwarded infinitely when the route forms a loop. The TTL value will be reduced by 1 every time it passes through a router, and the packet will be discarded when the TTL is 0.
- Protocol
Upper-level protocol, which identifies the protocol of the data carried by the data, and identifies the transport layer address or protocol number, such as 1 for ICMP, 6 for TCP, and 17 for UDP.
- Header checksum (Header checksum)
The value to confirm whether the IP header is damaged is used to check whether the IP header is discrepant.
- Options
Optional field (0--40B) The Option field is rarely used and is used for control, forwarding requirements, testing, etc.
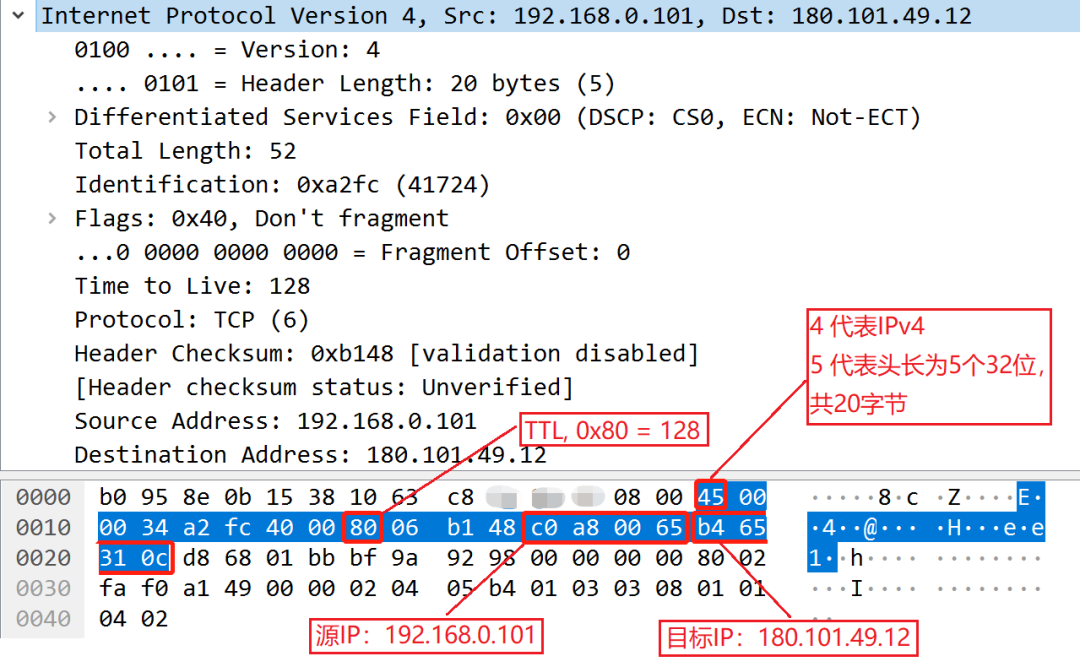
There is a lot of information on the network layer, so let’s just pick up a few important information:
The conversion of c0 a8 00 65 in the second line into decimal is 192.168.0.101. This is the IP of my computer. Note that this is the LAN IP. The following b4 65 31 0c is converted into decimal to 180.101.49.12, which is the target IP, which is the Baidu server IP.
transport layer
The function of the transport layer is to ensure that data is reliably sent from the sending node to the target node. Let's look at its header structure, and we can already see the handshake information carried.
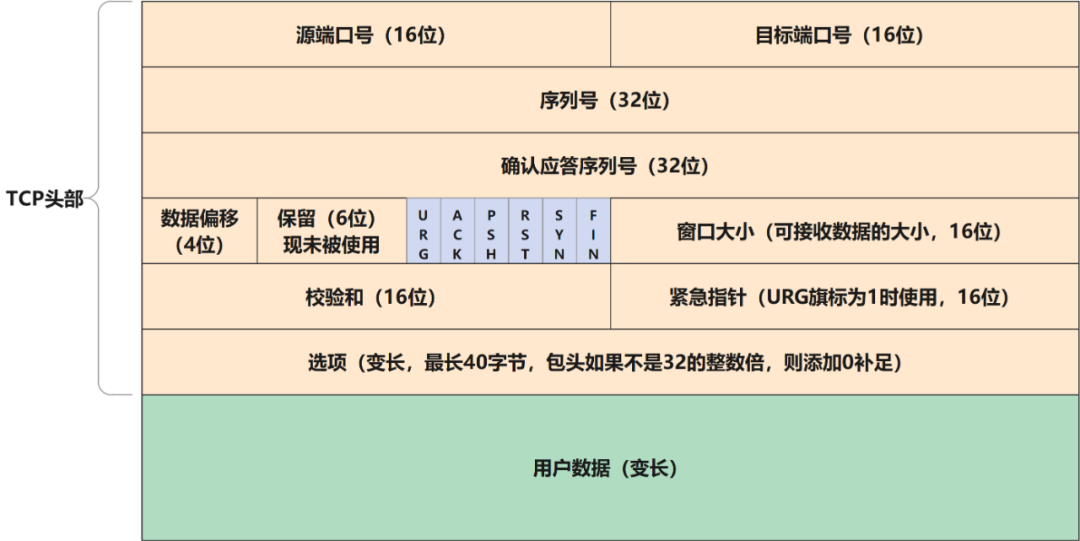
- Sequence Number
Indicates which data is the first among all the data
- Acknowledgment Number
Indicates the number of the next data to be received
Let's look at the captured packet data again, peel off another layer, remove the IP header, and first look at the first handshake:
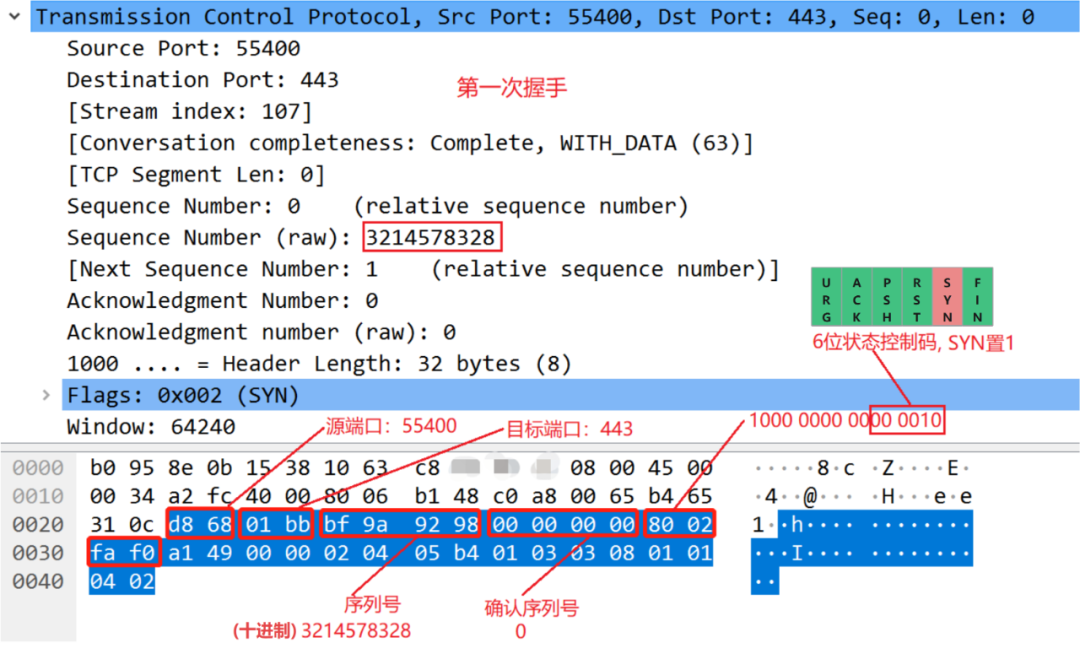
We can see that during the first handshake, the client randomly generates a serial number, which is quite large, and then sets the SYN in the status control code to 1 and sends it to the server.
Second handshake:
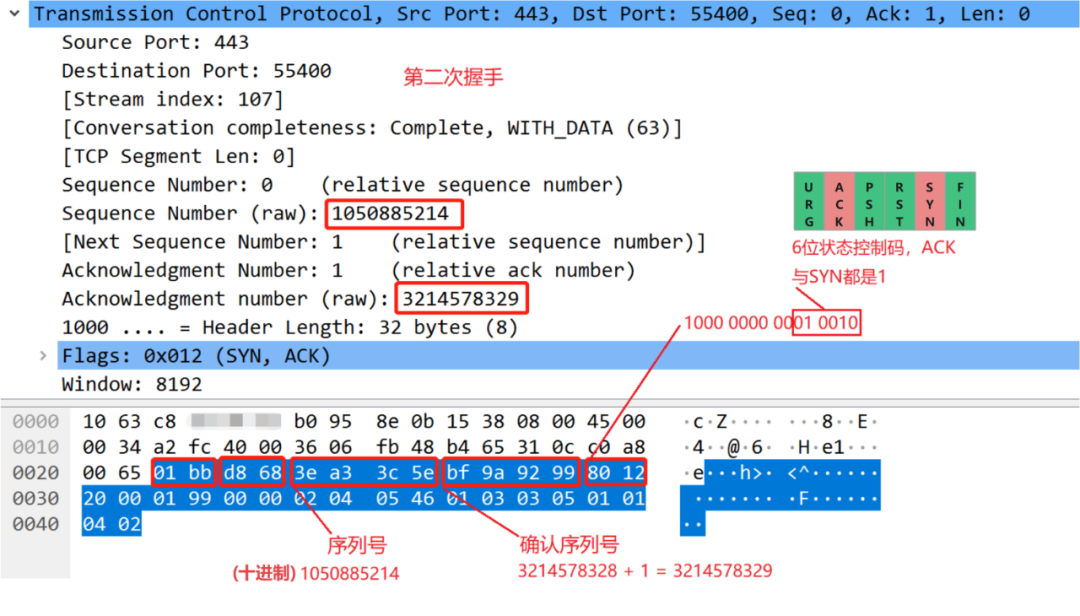
After the server receives the message from the client, the server will give the client a reply. Since the server greets the client, the port numbers are exchanged. Here, the server also randomly generates a serial number, and at the same time the first After a handshake, the serial number of the client is increased by 1, and sent as a confirmation serial number, and the ACK and SYN of the status control code are set to 1, and sent to the client.
The third handshake:
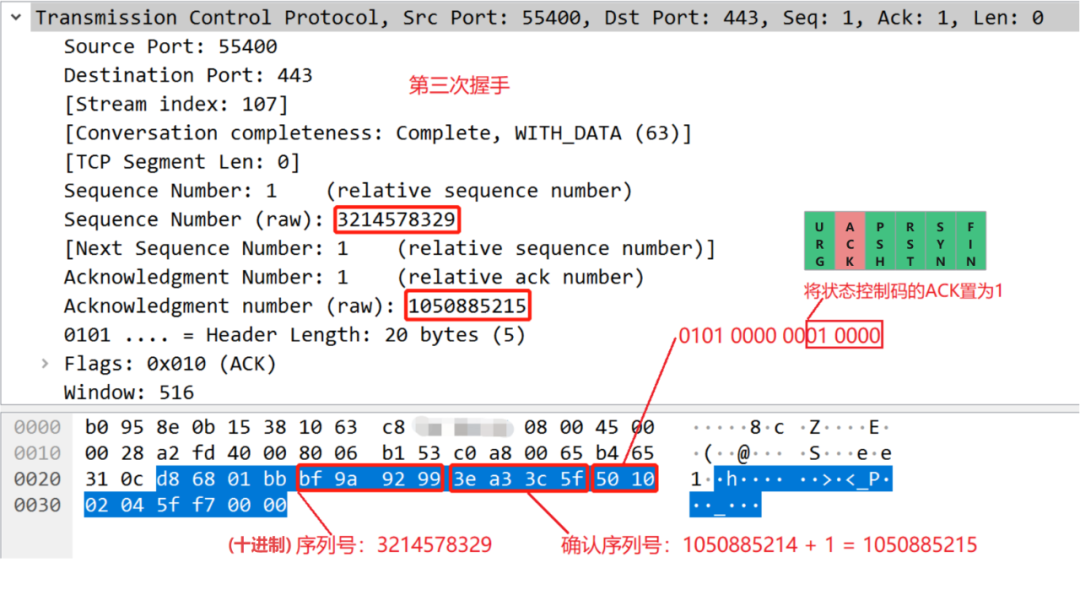
The third handshake is after the client receives the response from the server, and the client responds again. It can be seen that the serial number is the confirmation response serial number sent by the second handshake server, and the confirmation serial number of the third handshake client is the confirmation serial number sent by the second handshake server plus 1.
In this way, the three-way handshake is completed, and the two parties establish a connection and can communicate with each other.
Well, the above is all the content of today. In fact, the three-way handshake is just the tip of the iceberg in TCP. There is a lot of knowledge involved in the actual transmission process, such as timeout retransmission, verification, window mechanism, etc., but today I will talk about it first. Come here, students with weak foundations can digest it first, and I will tell you the following knowledge when I have time.