F5 full data path protection capabilities, escort the digital transformation of enterprises
2021.05.25

[51CTO.com original manuscript] Affected by factors such as the epidemic, the process of corporate digital transformation has been pressed for shortcuts. In the process of digital transformation, enterprises are also facing many challenges. The first to bear the brunt is the complex application portfolio. Take the financial industry as an example. In the past, transactions could be conducted through counters and simple computer terminal operations. Today, more and more businesses tend to be Internet-based and mobile, giving birth to more types of terminals and more types of transaction methods. This requires changes in the environments that support these applications: cloud environments, multi-cloud environments, microservices, containerization, and so on. It is impossible for customers to immediately abandon all the IT architectures that have been used for many years, because the cost, time, and risk are uncontrollable. Therefore, more enterprise users build new IT environments to support new applications, and the new and old IT environments coexist. For operation and maintenance personnel, managing a complex environment is a major challenge they face.
The second is the surge in security risks. With the deepening of the digital transformation process, more businesses can only be handled online, or more customers choose to handle online, and subsequently more and more security attacks have occurred, which has brought financial companies Huge safety pressure.
Third, the lack of visualization. More and more corporate strategies are shifting from product-centric to customer-centric. Customers pursue better user experience and need to feedback and monitor the progress of business processing at all times.
In addition, the safety supervision policy has also undergone great changes. From early static reinforcement to passive confrontation, different strategies are adjusted according to the application to meet compliance requirements, to security situation awareness, active confrontation protection, compliance and active confrontation have become the foundation of security.
In the face of many challenges, traditional security architecture has exposed a series of problems: encrypted traffic causes security blind spots and high-performance consumption; all traffic flows through all security devices, resulting in waste of resources; high latency affects user access experience; security devices The strategy remains the same; the security equipment has poor scalability and is difficult to expand; and the cloud-native security capabilities for "east-west" traffic are insufficient. Enterprises need full data path security protection to solve these problems. The so-called full data refers to the application from the customer to the back, whether it is north-south traffic or east-west traffic inside containers and cloud natives, it needs to have the capability of security protection.
F5 Perceives controllable, on-demand application protection means
As the world's leading application delivery network manufacturer, F5 has been providing comprehensive security protection solutions for enterprise applications for more than 20 years. In recent years, through the acquisition of NGINX and Shape Security, F5's product line has been continuously enriched, helping customers build a system and architecture that can achieve full data path protection. Chen Liang, Technical Director and Deputy General Manager of the Security Business Department of F5 China, gave a detailed introduction.

Chen Liang, Technical Director of Financial Business Department and Deputy General Manager of Security Business Department, F5 China
First of all, F5 is a manufacturer with a natural security gene under a full-agent architecture. When traffic arrives, the F5 solution will first judge and identify whether the traffic is reliable, credible, and safe, and then transmit it to the background server. The content returned by the server will be delivered to the client only if the traffic is judged to be safe. This is a full proxy process. If you are doing distribution, you need F5 load balancing products; if you are doing port IP layer protection, you need F5 firewall products; if you judge the seven-layer application before forwarding, it is the seven-layer load balancing; if it is judged that the application layer has a lot of security Risk, you need to use WAF to block. It is F5's role as a bridge between the network and the application that makes F5 inherently possess this kind of full agent security gene.
Second, at the cloud-native level, NGINX is currently the world’s most downloaded and most used open source reverse proxy software for WEB servers. After F5 acquired NGINX, because NGINX already has a lot of cloud-native application security-related and API application security-related capabilities, F5+NGINX already has the ability to protect the full data path from the customer to the code. With the acquisition of Shape Security in 2019, in terms of business prevention capabilities, F5 is based on artificial intelligence, machine learning and other technologies, and its anti-fraud and business-level security protection capabilities have also been effectively improved, truly realizing a full data path Under the protection ability. It is worth noting that F5 security protection products can be deployed in all environments: data centers, containers, hybrid clouds, and multi-clouds.

From the architectural point of view, at the basic layer, it is the cleaning of traffic and the protection of boundary security. When a request comes in, F5's security products can visualize and fine-divide the traffic, and distribute the traffic to other security device gateways for processing as needed. In this way, the dual-mode security model can play a better role in compliance and confrontation.
At the application layer, F5 has full-end security protection including cloud native, API, containerization, and microservice architecture.
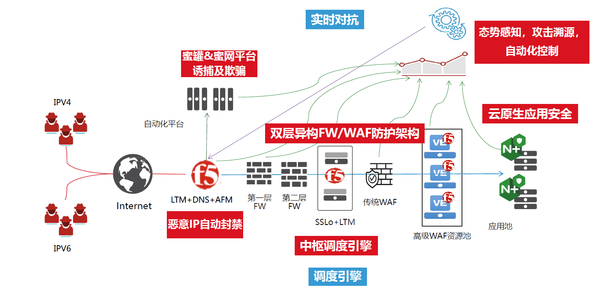
It is worth noting that F5's telemetry technology can transmit transaction requests, delayed requests, customer access request data, security attack event data, etc. generated by the client to the brain of F5, or the data created by the customer. The platform, in conjunction with customers, can also use F5's own AI brain to flow, so as to improve visualization, support the business, and realize situational awareness and dynamic defense. After all traffic is judged by the AI brain, the issued strategy will be more accurate and more dynamic.
Professional service team and security industry alliance
In addition to a complete set of security solutions, F5 also has a global experienced team with security certification to ensure 7*24 hours of response and protect users from security attacks in real time. In addition, F5 also provides professional threat intelligence and security services. F5's professional team monitors all traffic worldwide, conducts security analysis based on big data and AI, distinguishes normal traffic from malicious traffic, conducts behavior analysis and terminal Analyze and work with security industry experts to jointly defend against various security threats and provide customers with unified threat analysis services to deal with application risks and application health protection in a multi-cloud environment
As a "small and beautiful" manufacturer, F5 has established a security industry alliance with many security vendors in the industry, hoping to give customers better choices.
In short, as F5 continues to integrate product lines such as NGINX and Shape, its full data path protection capabilities have also been further improved. In terms of application layer security, traffic visibility and fine separation, infrastructure security, and trusted application access, etc., Both have demonstrated stronger protection capabilities and have been fully verified in past customer practices.
[51CTO original manuscript, please indicate the original author and source as 51CTO.com for reprinting on cooperative sites]
Hongmeng official strategic cooperation and co-construction-HarmonyOS technology community
【Editor in charge: Zhao Lijing TEL: (010) 68476606】