Graphical network: access control list ACL, the function is comparable to a firewall

In the world of computer networking, an ACL is one of the most fundamental security components, a function that monitors incoming and outgoing traffic and compares it to a defined set of statements.
ACLs mainly exist in network devices with packet filtering functions, including routers and switches.
In this article, Rui Ge will take you to uncover the mystery of the ACL in the form of a diagram.
Let's jump right in!
What is an ACL?
- English full name: Access Control List
- Chinese name: Access Control List
An ACL is a list of rules that specifies which users or systems are allowed or denied access to specific objects or system resources. Access Control Lists are also installed in routers or switches, and they act as filters to manage which traffic can access the network.
ACL type
There are generally two types of ACLs:
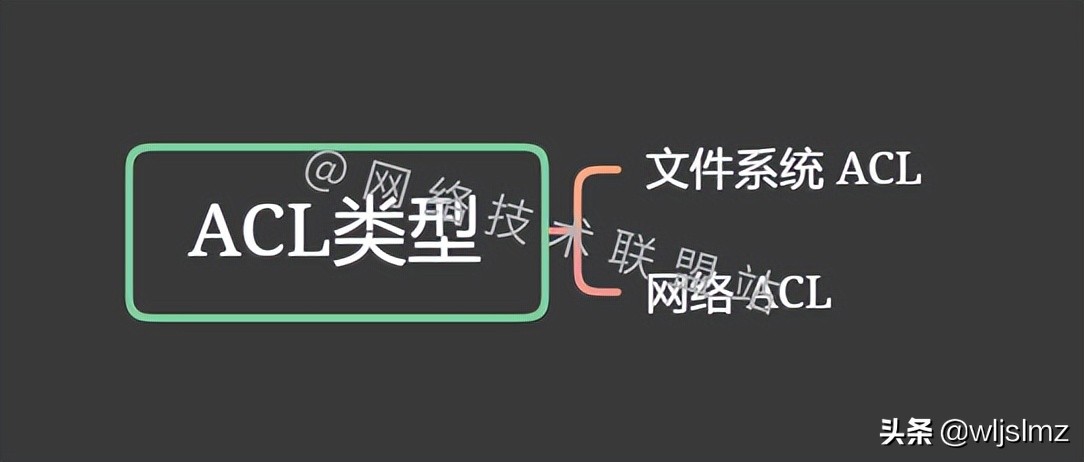
ACL type
- Filesystem ACLs: Generally filter access to files and/or directories.
- Network ACL: Filter access to the network, generally used for network devices, such as routers, switches, etc.
This article focuses on network ACLs.
ACL Advantages
ACL has many advantages, such as:
- Helps improve network performance by limiting network traffic
- Provides security by defining permissions and access rights
- Provides granular control over traffic entering the network
Why use ACLs?
ACLs play a role in maintaining the normal flow of network traffic, this kind of regulation of network traffic is the main way to maintain the security of an organization or network, access control lists help to limit the traffic that does not seem to be suitable for the security of the organization, thus ultimately achieving a better network performance.
The main reason for using an access control list is to maintain the security of the network and protect it from vulnerable and dangerous attempts. If messages travel through the network unfiltered, the chances of putting an organization at risk are Increase.
By using access control lists, the network is granted a specific level of security to regulate all those servers, networks and services that are authorized and not authorized for use by users, in addition, ACLs help to monitor all data entering and leaving the system.
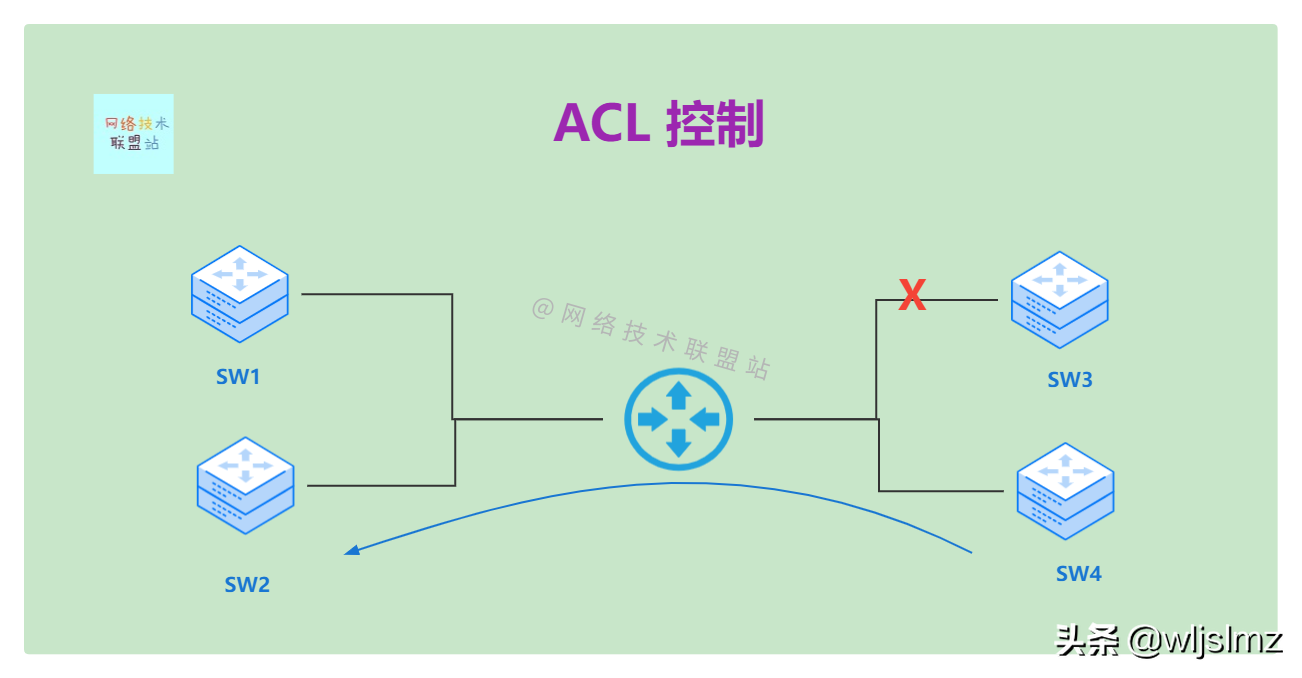
ACL control
As shown in the figure, SW3 and SW1 do not allow access due to ACL control, and SW4 to SW2 allow access.
Composition of ACL
An ACL is a set of rules or entries, and each device can set up an ACL with single or multiple entries, where each entry can have different rules that allow or deny certain kinds of traffic.
A general ACL has the following parts:
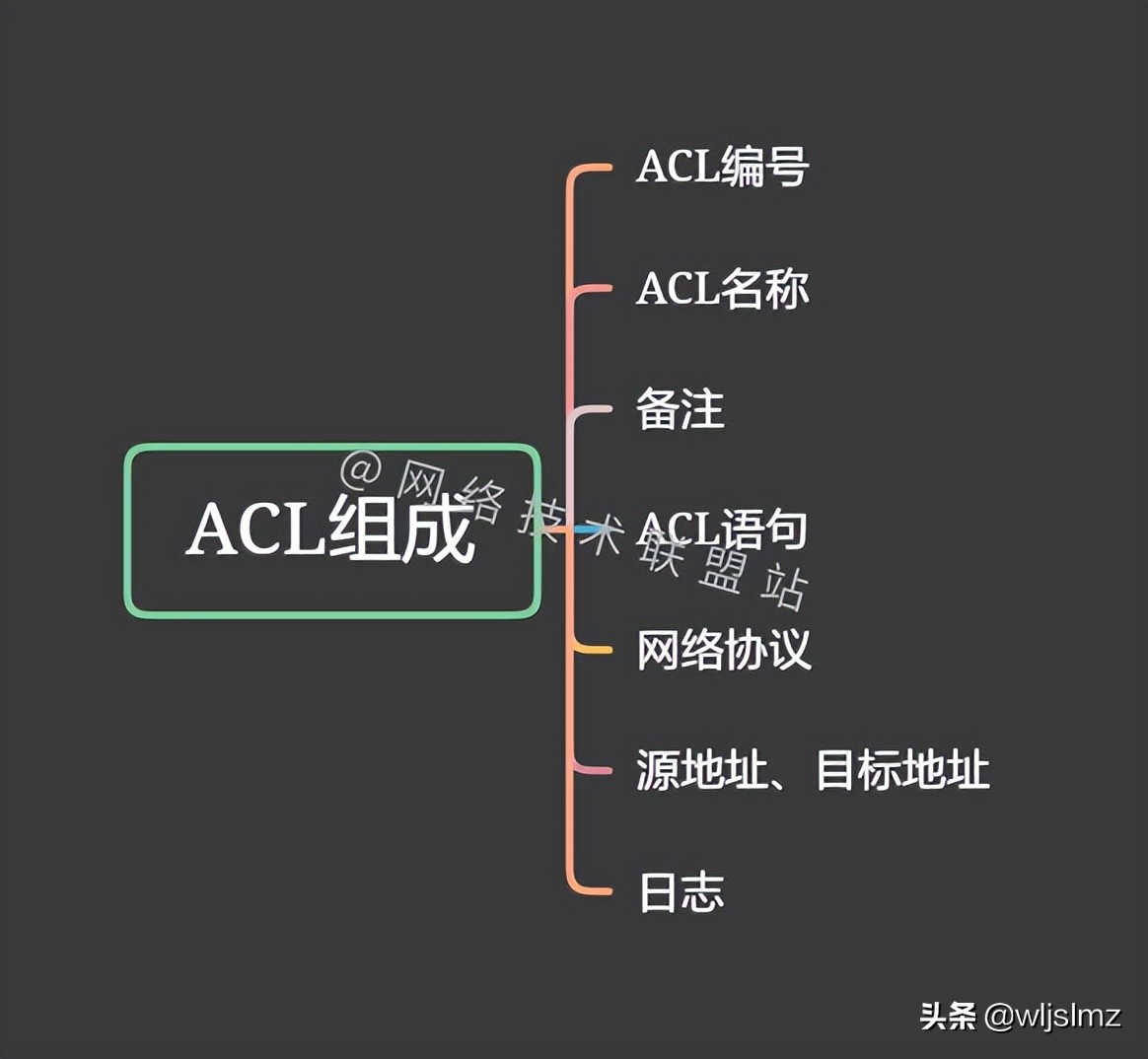
Composition of ACL
ACL number
A code that identifies an ACL entry.
ACL name
ACL names can also be used to identify ACL entries.
Remark
Comments or detailed descriptions can be added for ACl
ACL statement
It is to write some statements that deny or allow traffic. This is very important and will be discussed in detail later.
Network protocol
Such as IP, TCP, UDP, IPX, etc., rules can be written according to these network protocols.
source address, destination address
These are the inbound and outbound addresses targeted by these ACL rules. For example, if your computer accesses the company's server, then your computer is the source address, and the company's server is the destination address.

source address, destination address
log
The incoming and outgoing traffic can be recorded by the ACL log function for statistics or troubleshooting of network problems.
Classification of ACLs
In general, ACLs are divided into four categories:
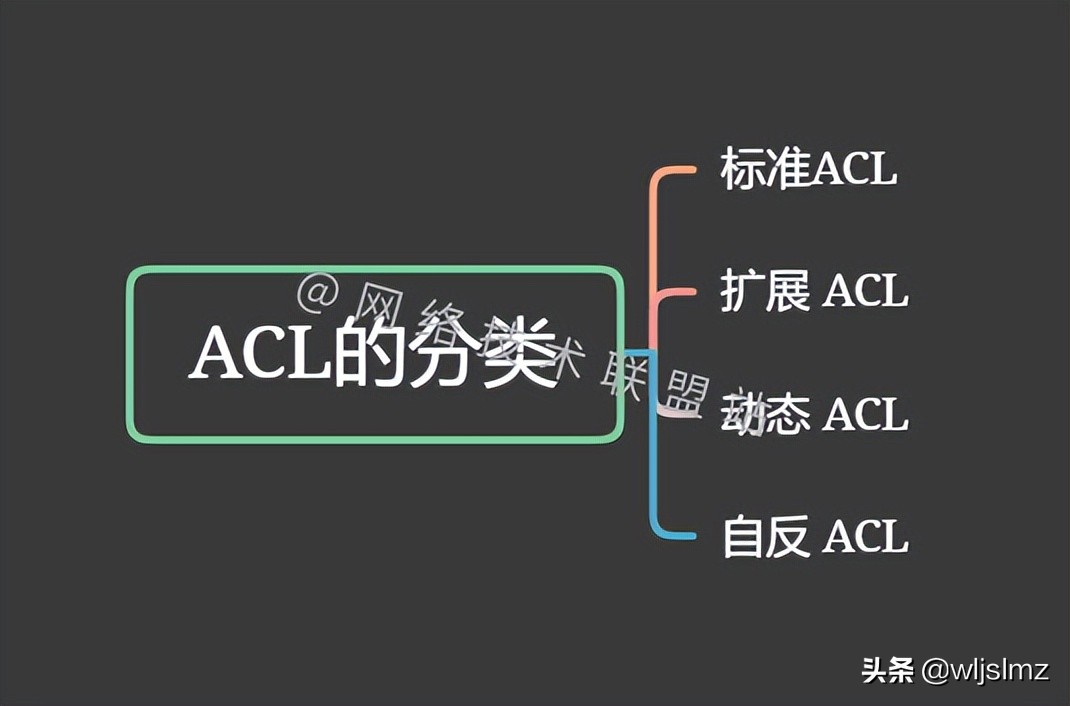
Classification of ACLs
Standard ACL
This is the weakest basic ACL, looking only at the source address.
The following is the ACL number 5, which is a standard ACL and allows the network of 172.16.1.0/24:
access-list 5 permit 172.16.1.0 0.0.0.255- 1.
Extended ACL
More advanced ACLs capable of blocking entire networks and traffic based on their protocol information.
The following is an ACl numbered 150 that allows all traffic from the 172.16.1.0/24 network to any IPv4 network if the target has HTTP port 80 as the host port:
access-list 200 permit tcp 172.16.1.0 0.0.0.255 any eq www- 1.
Dynamic ACL
A more secure ACL, which utilizes authentication, extended ACLs, and Telnet, allows users to access the network only after an authentication process.
Reflexive ACL
Adding session filtering to another ACL type of packet filtering, also known as IP session ACLs, uses upper-layer session details to filter traffic.
Reflexive ACLs cannot be applied directly to interfaces, are usually nested in extended named access lists, and do not support applications that change port numbers during a session, such as FTP clients.
ACL rules
- ACL rules are matched in order. If there are multiple lines, they must start from the first line and go to the last line.
- There is an implicit deny at the end of every ACL, if no condition or rule matches, the packet will be dropped.
- Generally, there are outbound and inbound ACLs. Only one ACL can be assigned to each interface per protocol in each direction, that is, only one inbound and outbound ACL is allowed per interface.
- Whenever possible, use notes and logs to provide detailed information about the ACL for later troubleshooting and memorization.
ACL usage scenarios
ACL usage scenarios
Generally, there are three situations:
NAT
During address translation, a large number of ACLs are set to control network traffic due to internal and external network security considerations.
firewall
Needless to say, what the firewall does is the ACL rules.
QoS
This is generally more common in traffic policies, which control the access rights of users on different network segments to traffic.
Generally speaking, ACL usage scenarios cannot escape these three situations. Even if there are other situations, these three situations can definitely be used to make general associations.
Summarize
An ACL is a set of rules that allow or deny access to a computer network. Network devices, namely routers and switches, apply ACL statements to inbound and outbound network traffic, thereby controlling which traffic can pass through the network.