F5's 2022 State of Application Strategy Report shows that edge deployment and workload security are the focus of attention in Asia Pacific

Digital transformation is in full swing and technology is evolving rapidly. However, as digital transformation continues, applications, integrations, and environments explode, creating complexities that are increasingly difficult to manage. Recently, F5 released its annual survey report "2022 Application Strategy Status Report" for IT decision makers, revealing several cutting-edge trends in the field of application security and delivery, and interpreting the challenges faced by enterprises and the technologies of concern.
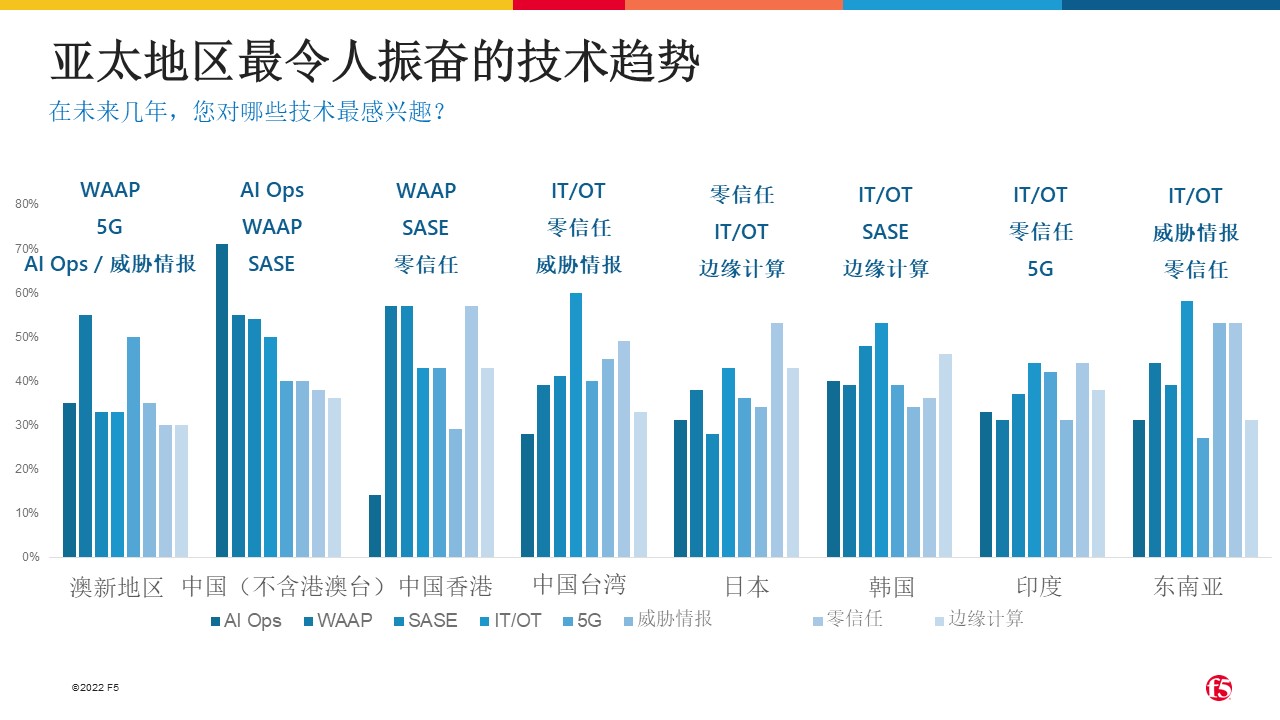
The Most Exciting Tech Trends in Asia Pacific for 2022
Globally, the deep convergence of IT and operational technology (OT) is the most anticipated technology trend by respondents. This result is expected due to the many benefits that the convergence of IT and OT can bring to reduce operational costs, enhance security coordination, and improve operational efficiency.

In addition to this, respondents in the Asia-Pacific region selected technologies that would be security-related in the "Most Exciting Technology" category. The survey results show that Mainland China and Hong Kong Special Administrative Region of China have shown higher interest in Web Application and API Protection (WAAP).
In the wake of the pandemic, 90% of businesses have been actively adapting their security protections, raising awareness through training, and exploring other solutions and approaches to reduce complexity. Last year, for example, 48 percent of organizations put more emphasis on vulnerability management and automation. Other key strategies include adopting cloud security protection, enhancing employee training and integrating security vendors. In the future, most enterprises will need to use a combination of the above strategies to effectively manage the risk of security breaches.
Edge application security and delivery technologies gain traction
As more and more businesses choose not to host applications on-premises, understanding where application-enabled technologies are deployed becomes critical. To better understand this issue, we asked respondents where they host application services that are critical to their IT and digital platforms.
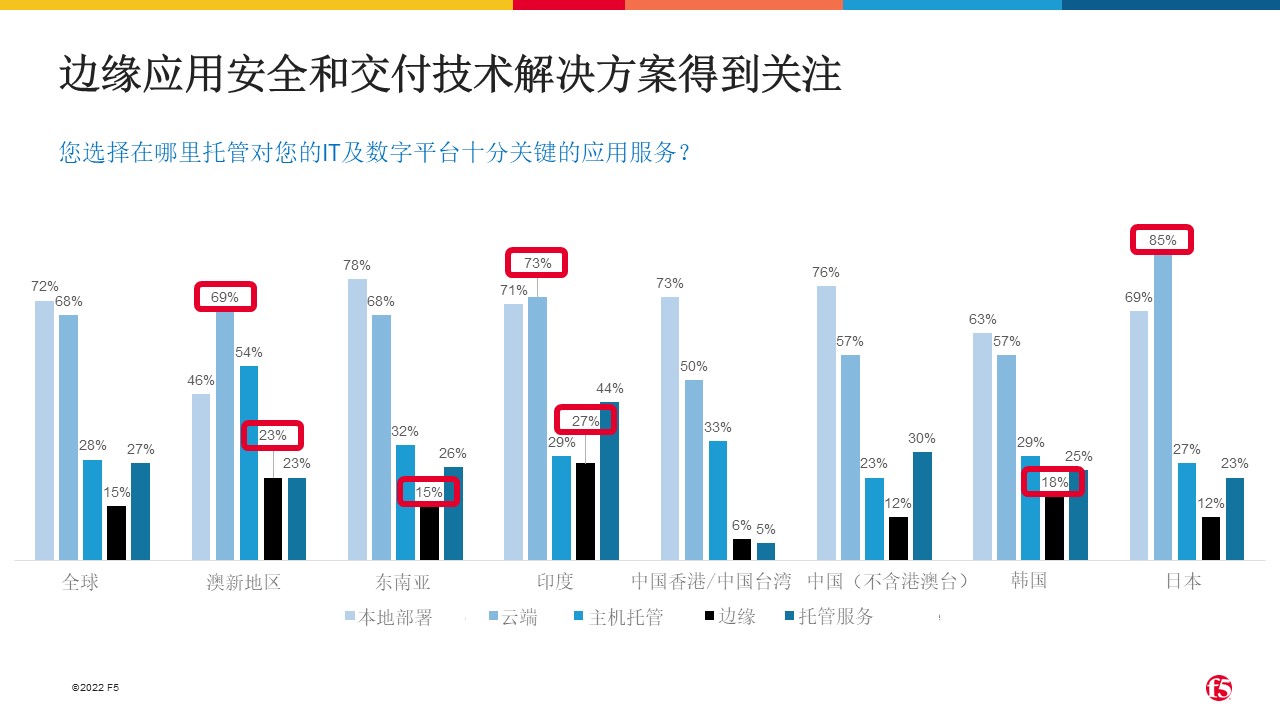
Globally, more than four in five respondents (84%) plan to deploy workloads to the edge to enhance employee and customer experience. Looking at the results across different regions, we found that Australia, New Zealand and India, as pioneers in Asia Pacific, are leading the movement of workloads from the public cloud to the emerging edge, and they are the two regions with the highest levels of edge deployment .
Compared to last year's survey results, edge deployments in Asia Pacific are showing an overall growth trend. Growth in regions such as China, Hong Kong, and Taiwan has been impressive. This shows that the deployment of application enabling technologies is also migrating to the edge.
Not surprisingly, the consensus on edge deployments is that they want their applications to be secure, fast, and readily available. Security services such as DDoS and API gateways provide optimal performance at or near the edge, preventing attacks from affecting the entire network. Likewise, identity-based access control is likely to work best when deployed as close as possible to users—whether those users are using mobile devices or microservices.
We see that application security and delivery technologies are increasingly being deployed in separate locations from the applications they serve, and these application enabling services (from DDoS protection to access management to fraud prevention technologies) are increasingly The more it appears, wherever it is best suited for the specific context and function it serves. 92% of enterprises deploy applications on-premises, but only 53% host application security and delivery technologies there. Meanwhile, nearly 52 percent of enterprises deploy enabling technologies in the public cloud or at the edge. This separation of applications and their supporting services is directly attributable to the widespread adoption of cloud technologies, the emergence of edge technologies, the distributed nature of the resulting applications, and the advantages and disadvantages of hybrid deployments of various security and delivery technologies.
Identity and access management technologies are the most popular
Of the many application security and delivery technologies available, identity and access management technologies are now the most common, deployed by 96 percent of enterprises. This change is surprising, given that the previous enterprise preference was for availability technologies such as load balancing or more traditional security technologies such as SSL VPNs and firewalls.
Today, identity and access management technologies are highly sought after, partly reflecting the popularity of zero-trust security and the surge in telecommuting over the past two years, but mostly due to the microservices, scripts, sensors, Workloads, and even refrigerators and lights, have exploded. In the context of applications and their supporting technologies, the definition of "user" has gone far beyond the concept of the user of a device (or even a mobile device). As a result, most, if not all, security solutions are moving to identity-based management to securely authorize users (unlikely employees, and more likely APIs, services, or machines).
The entire legacy security service is the second most commonly deployed technology after identity services, and the third most usable technology. 90% of enterprises deploy all three of these services, and another 85% deploy application delivery technologies aimed at improving performance.
Businesses need to balance performance and security
In the security space, this year's survey results brought some good news, starting with a strong agreement between IT and business leaders on the importance of protecting the overall business and infrastructure and applications. Second, performance remains important, with more than three-quarters of respondents admitting they would be willing to turn off security measures to improve performance if given the choice. Half of the respondents do this even if the performance gain is less than 50%.
This desire to improve performance far beyond security reflects a growing realization that impeccable threat mitigations do not exist, or if they do exist, the cost in terms of operational expenses, user dissatisfaction, or missed opportunities is very high. beyond the company's capacity. Running a secure digital business requires managing a range of risks based on other practical goals. This means businesses need to balance acceptable performance, customer experience and cost with acceptable protection and security compliance.
write at the end
In addition to the State of Application Strategy 2022 report, the F5 Asia Pacific research team has produced a separate report on multi-cloud trends in the Asia-Pacific region, which explores the progress of multi-cloud deployments and the challenges of connecting, running and securing workloads across multiple clouds . Combining the findings of the two reports, we can conclude that the need for multi-cloud and edge deployments stems from the accelerating process of digital transformation and the strong need for enterprises to accelerate their business development.
Finally, we are pleased to see that more and more enterprises in Asia Pacific are making positive progress on the road to digital transformation, and we also encourage enterprises to prioritize security, visibility and control when undertaking digital transformation. options.
For more global coverage and other key core insights, read the following technical blog posts:
2022 State of Application Strategy Report: Modernizing with Intelligent Operation and Maintenance Technology
The Most Exciting Tech Development of 2022: The Convergence of IT and Operational Technology (OT)
In 2022, the legal function has become the focus of the digital transformation of enterprises
About F5
F5 (NASDAQ: FFIV) is a multi-cloud application security and application delivery services technology leader, delivering differentiated, high-performance and secure digital experiences to customers including enterprises, service providers, government and consumer brands. For more information, visit f5.com. You can also follow @F5 China official Weibo on Weibo, or visit our Chinese website at www.f5.cn to learn more about F5, its partners and technologies.
F5 is a trademark or service mark of F5, Inc. in the United States and other countries. All other product and company names herein may be the trademarks of their respective owners.
# # #
This press release may contain forward-looking statements relating to future events or future financial performance that involve risks and uncertainties. Such expressions can be identified by the following words: "may", "will", "should", "anticipate", "plan", "anticipate", "believe", "estimate", "predict", "potential" or "persistent", or the negative form of such or similar words. These statements are projections only, and actual results may differ materially from those projected in these statements depending on a variety of factors, including those identified in the company's filings with the Securities and Exchange Commission.