Let's talk about the privacy and security of 5G technology

On March 17, 2022, the European Parliament’s Science and Technology Options Assessment (STOA) Task Force released a study titled “Privacy and Security in 5G Technology”. The report focuses on the two main aspects of privacy and security of 5G technology, focusing on the analysis of EU and global cybersecurity risks and threats, privacy challenges and 5G technology opportunities, and the relationship between cybersecurity risks and privacy issues, for the European Parliament Legal Affairs Committee, Internal Market and Consumer Protection Committee, Civil Liberties and Justice and Internal Affairs Committee, Security and Defence Subcommittee and other EU institutions and Member States to consider.
1. Introduction
In an expanding global population, more and more people are accessing services online. In 2020, global traffic peaked at 700 MB/s. More than 73% of visits are made while on the move - via a mobile phone network or wireless connection. The huge traffic burdens and strains the existing network, so it is necessary to upgrade it. 5G is expected to meet growing demand in Europe and beyond, and will connect everyone and everything, everywhere.
5G's unparalleled capabilities and flexibility are enabled by a decades-long convergence between computing and telecommunications. Amid this ongoing epoch-making shift, a broad debate over privacy and security has unfolded. On the one hand, the right to privacy is a fundamental right of citizens, secured and strengthened by extensive social safeguards and evolving regulatory frameworks within and outside Europe, guaranteeing individuals (data subjects) ownership and control of their personal data and protecting their personal identities s right. On the other hand, the security rules and measures of the digital world clarify the protection of data, thus guaranteeing the trustworthiness of the ecosystem, thanks to reliable data access (availability) only by authorized persons, and protection of storage and exchange Information is not subject to unauthorized access (confidentiality) or unauthorized modification (integrity).
After illustrating the importance and necessity of ensuring fundamental human rights such as the right to privacy, this report presents the findings of a study focused on the privacy and security of 5G technology.
In practice, five generations of mobile communication networks with increasing data speeds have been deployed over the past 40 years. Although each generation has different specific standards, protocol stacks, technical architectures and radio modulation schemes, 5 generations of mobile communication technologies can be divided into 3 different categories according to the additional services they can provide, and mobile networks have evolved from connecting people. to connect the machine. In fact, in the 5G standard, people are no longer considered the primary end user of the communication network, but probably machines - the Internet of Things.
2. Privacy and security in the context of 5G technology
The complexity of the 5G ecosystem requires an in-depth understanding of its major components, especially how each component affects each other in terms of privacy and security. Therefore, in order to accurately describe the privacy and security issues in the 5G ecosystem, this report first defines a 5G research concept map, which contains the keys to analyze the components and their relationships, as shown in Figure 1.
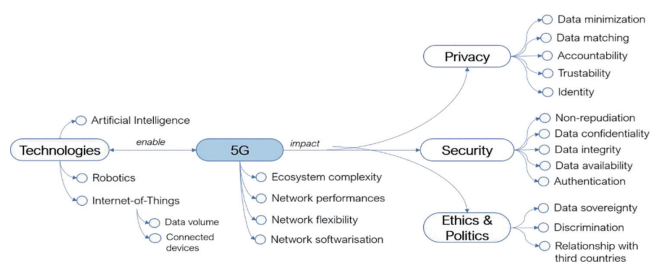
Figure 1 Concept map of 5G research
5G can be seen as a complex ecosystem, closely related to other related technologies, especially AI, IoT and robotics. Coupled with the fact that robotics and IoT are 5G-enabled technologies, the flexibility and programmability of 5G networks will enable wider deployment, which will enable robotics and IoT to be supported by better performance.
2.1 The relationship between security and privacy
In 5G systems, which are primarily characterized by digitization and data communications, the term "privacy" has the meaning of respecting and protecting individuals in the handling of their personal data. The European Union's General Data Protection Regulation (GDPR) is the cornerstone of services for individuals, and data subjects often use tools and methods to exercise their rights.
Those responsible for the collection, processing and storage of data (data controllers/processors) must establish the necessary rules and deploy appropriate tools to protect the data from unauthorized manipulation, thereby compromising the authenticity, integrity and confidentiality of the data To have an impact, these rules and tools fall under data security.
The right to privacy is a fundamental right of citizens, data protection is a means of recognizing this right, and security is a means of protecting this right. Data processing systems require specific safeguards throughout the design and validation process, as is the case with 5G.
In addition, compliance with ethical principles and related legal frameworks regarding privacy and security must employ the principles of "by design for confidentiality" and "by design for security".
2.2 Privacy and data protection legal framework
Currently, the EU data protection legal framework consists of Regulation 2016/679 General Data Protection Regulation, Directive 2016/680, Regulation 2018/1725 and the Proposed Electronic Privacy Regulation. These legal frameworks do not elaborate on the technical aspects, which means that they are not designed to regulate specific technical solutions, but to all activities.
3. Document-based impact assessment
3.1 Privacy Risks and Challenges
3.1.1 Cross-border data flow and 5G
5G is a complex ecosystem whose functions are carried out under a combination of virtual and physical infrastructure, therefore, 5G may require the cooperation of various providers in Europe or other countries. This has implications for privacy management, which must be considered for two reasons: First, EU Regulation No. 2016/679 expands the territorial privacy boundaries of the European Union (EU), whether legal entities in the EU or other countries, Both must comply with the provisions of the GDPR; the second is that the GDPR imposes restrictions on the transfer of personal data to third-party countries or international organizations outside the EU to ensure that the level of personal protection provided by the GDPR is not compromised.
3.1.2 High Data Rates
High expectations are placed on 5G mobile networks because of their high data rates and low latency, which ultimately lead to massive increases in data volumes and data transfer capabilities. The risks posed by high data rates and big data are often associated with the "three VS" attributes - capacity, speed and variety of processed data. Capacity refers to the amount of data processed, diversity refers to the variety of data types, and speed refers to the speed at which data is processed.
3.1.3 High-throughput and high-precision positioning
5G technology will use multiple-input multiple-output (MIMO) antennas, which are characterized by higher density and throughput capacity than current 4G technology. 5G networks will have less coverage due to higher frequencies, which will improve the accuracy of device positioning, making it easier to reveal the location of data subjects. As a result, leveraging 5G could greatly improve the possibility of real-time location services that take advantage of the longer battery life, location accuracy and lower end-point costs of today's devices compared to traditional technologies such as Bluetooth and Wi-Fi .
3.1.4 Massive Device Connection (Internet of Things)
The low latency of 5G technology means more devices can be connected. According to GSM forecasts, the total number of 5G connections will increase from 500 million at the end of 2021 to 1.8 billion by 2025. 5G will have potentially disruptive impacts in several areas, including:
(1) From self-driving vehicles to renewable energy smart grids, reducing traffic congestion, greenhouse gas emissions and road traffic injuries; (2) From smart cities and smart homes to healthcare, with wireless service robots for operations and even surgery Surgery; (3) From collaborative robots to factories of the future, to improve the efficiency of energy and resource utilization, reduce waste and personnel injuries.
IoT developers should always adhere to the principle of data minimization, which essentially states that any data processing activity should only use the minimum amount of data required. Furthermore, the collected data should not be used for any other purpose or processed without the consent of the data subject.
3.1.5 Internet Protocol
5G mobile communication technology is still an IP-based network. It is well known that in some cases both dynamic and static IP addresses as identifiers are personal data. When devices are assigned static IP addresses, the addresses do not change; conversely, when devices use dynamic IP addresses, they connect automatically and change over time. Dynamic IP addresses may constitute "personal data" and may be possible when third parties (such as Internet Service Providers) have additional information (such as account details) that can link these dynamic IP addresses to the individual's identity constitute "Personal Data".
3.1.6 Policy choices for privacy risks and challenges
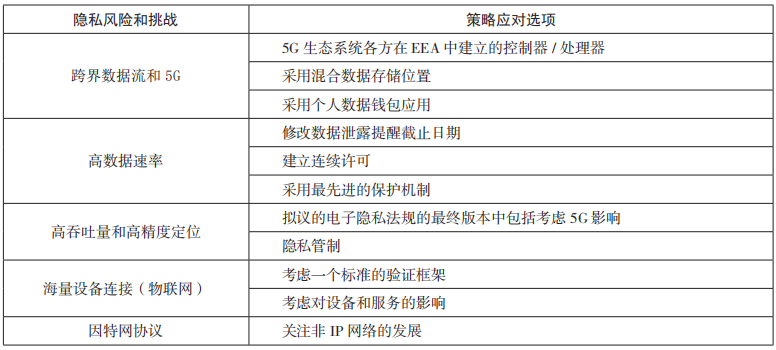
Based on existing technical specifications, scientific literature, and an assessment of the impact of 5G technology, 5 major privacy risks and challenges were identified, and 11 strategic response options were proposed to mitigate and address these issues, as shown in Table 1. 1 shown.
Table 1 Policy response options for privacy risks and challenges
3.2 Security and Cybersecurity Legal Framework
In 2013, the European Commission published the EU Cybersecurity Strategy: An Open, Reliable and Secure Cyberspace, with the aim of enhancing the security of cyberspace and identifying the goals of achieving cyber resilience, supporting the domestic market, strengthening EU security and substantially reducing Action required for cybercrime. With this move, the EU has promoted and shaped a more unified legislative approach to cybersecurity threats, especially those that cross national borders.
In view of this, Directive No. 2016/1148 of the European Parliament, the Network and Information Systems Security Directive, provides legal measures to improve the overall level of cybersecurity in the EU; Regulation No. 2019/881(32) promulgated by the European Commission proposes Launched the first EU certification scheme for ICT digital products, services and programs.
Within these guidelines, the expert group has published several reports related to 5G cybersecurity, including on risk assessments of 5G networks, a toolbox of measures to mitigate 5G network risks, and a report on Member States' implementation of measures in the toolbox progress report.
As evidenced by best practices in risk management, risk assessments must be conducted on an ongoing basis to identify new potential threats and assess the effectiveness of applicable strategies. This is mandatory, especially in the context of the still-evolving 5G specification. In fact, version 17 of the 3rd Generation Partnership Project (3GPP) was launched in March 2022, followed by protocol coding in June 2022. In response, the European Union Agency for Cybersecurity (ENISA) has issued supplementary and updated guidelines, in particular the report on the 5G cyber threat situation, the report on the security aspects in the 5G specification, and the 5G security measures Supplement to the guidelines.
The European Commission has recognized the importance of a unified approach to addressing risks related to the technical vulnerabilities of 5G networks and has asked ENISA to create a candidate European Security Certification Scheme (EU 5G Plan) for 5G networks. To achieve this, ENISA calls for the active participation of all parties interested in participating in the ad hoc working group.
3.3 Security Risks and Challenges
Technical reports, research papers, and agency reports have all highlighted how 5G technology can greatly improve the privacy and security concerns of wireless networks through the protection mechanisms widely adopted in the 5G specification. Improvements to these security specifications are still under revision, and protocol encoding details are expected to be available in June 2022. In fact, a high level of security is one of the 5 pillars of 5G's new wireless architecture, which also includes new radio spectrum, huge bidirectional antennas, multiple connectivity and network flexibility.
In this regard, the analysis of security risks and challenges takes into account the latest version of the technical specifications, 3GPP published TS 23.501 "5G System Architecture" in July 2021 and TS 33.501 "5G System Security Architecture" in September 2021 Structure and Procedures" and officially published. This report formally models and describes security risks in 5G technology using the language and serialization format of structured threat information representation for exchanging cyber threat intelligence. The use of STIX has continued to grow over the past few years, and its development is under the control of OASIS, a non-profit standards body.
3.3.1 5G Service-Based Architecture
5G Service-base architectures (Sba) is the reference model of the 5G ecosystem, which identifies four main component types: user equipment, radio access network, 5G core, and data network, as shown in Figure 2 .
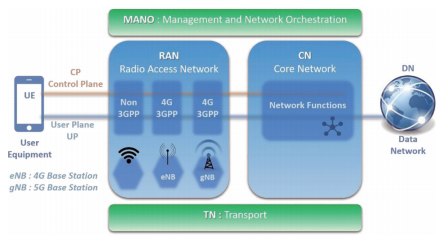
Figure 2 High-level architecture of a 5G network
Among them, the two green parts in the figure provide interconnection functions (ie TN-transmission) and governance functions (ie human management and network coordination) for the 4 component parts. It is emphasized that these two green parts are currently not part of the 3GPP specification.
Furthermore, for security risk analysis, two main communication channels are considered, namely, the user plane (User Plance, UP) and the control plane (Control Plance, CP). The user plane is the device data that carries users/connections, and the control plane (CP) is what handles control signaling traffic and interconnects all components in the 5G network architecture.
The 5G core network provides all network functions, such as routing, authentication and policy control, to enable communication within the accessing User Equipment (UE) and Data Network (DN). One of the most important innovations in the 5G architecture is the complete virtualization of the core network. This softwareization of network functions will significantly improve the portability, scalability and flexibility of systems and services, but will also bring new concerns and challenges. All components in the Service Based Architecture (SBA) of the 5G core network communicate through the Application Programming Interface (API).
3.3.2 Network software and flexibility
Of course, network softwareization brings many advantages in terms of flexibility, enabling network operators and service providers to choose the right solution in a wider and more competitive market. Telecom operators are often considered vulnerable even when they reduce the use of hardware equipment, and softwareization represents the ability to prevent, mitigate vulnerability, or recover from potential threats. In fact, since network functions can be scaled and replicated according to specific needs, any node of the network may be reconfigured and scaled in time to prevent potential compromises in the system and its connected resources, as well as depending on the applications being served. Flexible definition of specific needs. However, the current issue is to define some security controls (such as lack of encryption of control plane data) and physical deployment configurations (such as RAN and CN functions may be deployed at the same site) as optional in the technical specification, to the vendor Leave a degree of freedom in how controls are interpreted, implemented, and used. This may blur the distinction between the functions, roles, and responsibilities of components in the architecture from a security perspective, making it harder to identify potential vulnerabilities and threats that can undermine the resilience of the entire network.
3.3.3 Multiple Connectivity and Device Density
The network softwareization of 5G technology enables the interconnection of a new generation of mobile devices (i.e. 5G devices) and ensures connectivity with both 3GPP (e.g. 4G) based and non-3GPP (e.g. Wi-Fi) devices, a capability known as "multiple". “connectivity” is the key to the move towards standard wireless connectivity infrastructure and one of the five pillars of 5G, so 5G is expected to facilitate the deployment of IoT devices and enable “Internet of Everything” models (such as future factories and IoT robots, cars and vehicles, and electronic identification of everything).
Security mechanisms are deeply added and hardened through stronger encryption algorithms and authentication protocols, but multiple connectivity can hide broader, new potential risks from interconnections with legacy systems that do not enforce the latest security guidelines. In this regard, legacy systems and non-3GPP-connected devices can become backdoors for potential attacks, even if protection mechanisms (such as proxies and multi-access edge computing components) exist.
Additionally, this potential concern could be of concern if virtualized and massively connected devices are exploited by spoofed threat campaigns that clone network virtual nodes (digital twins) and route data traffic (for eavesdropping and jamming). If the predictive threat identification algorithm can prevent clone nodes, it can effectively improve the network's anti-attack capability, thereby mitigating the impact of the attack.
3.3.4 Protocols and Interoperability
The softwareification of the network will expand the use of IP protocols in 5G (see Section 3.1.5 for details). The protocol was designed more than 40 years ago for worldwide connectivity and was reviewed 20 years ago to ensure more addressable and connected devices. IP has always been based on packets, with a minimal set of data to transmit (such as packet headers), which is less efficient for IoT devices that perform frequent and short data communications. Therefore, specialized protocols are defined for these devices, such as ZigBee and Long Range Wide Area Network (LoRaWAN). In addition, IP-based protocols have many vulnerabilities (such as address spoofing, IP route traceability), allowing attackers to obtain information on the sender and receiver of data packets, or change data routing to interrupt network communication, thereby affecting its confidentiality, integrity and availability. In March 2020, the European Telecommunications Standards Institute (ETSI) launched a new non-IP network working group to address the needs of new 5G services to meet the challenges of the new digital age of connecting everything together , thereby improving throughput, latency, interoperability, and security. New protocols are being analyzed based on alternative IP protocols, and this challenge will be another important revolution in the development of communication networks.
3.3.5 Identifiers and Encryption
As described in Section 3.3.1, according to the current technical specifications, data encryption is ensured between the 5G base station (gNB) and the user equipment, while the individual operator has the flexibility to implement it in other parts of the SBA architecture. Limited by throughput and latency, encryption can be a hindrance in many latency-sensitive scenarios (e.g. automotive, telesurgery), and as a result, encryption mechanisms may not be implemented for many functions. In this regard, both the RAN and the Core are key components of the 5G network in the SBA architecture, so the gNB has access to all plaintext data between devices. However, research into new efficient and improved encryption mechanisms is moving forward with effective solutions, such as SNOW-V, a stream cipher that provides 256-bit security, due to its improvements in throughput and latency, is expected to As the primary encryption mechanism in 5G, the same is true for lightweight architectures.
3.3.6 Policy options for security risks and challenges
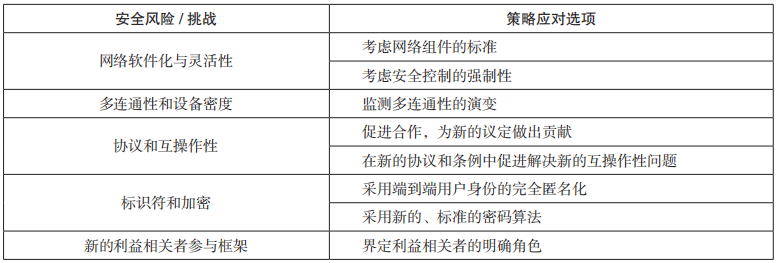
Based on existing technical specifications, scientific literature, and an assessment of the impact of 5G technology, 5 major security risks and challenges related to the security layer are identified, and 8 strategic response options are proposed to mitigate and solve these problems, such as shown in Table 2.
Table 2. Policy response options for security risks and challenges
3.4 The relationship between network security and artificial intelligence and 5G technology
The increase in overall 5G complexity is due to the shift in virtualization layers and networks to programmable, software-driven, services and management-based architectures. Additionally, 5G provides unprecedented operational flexibility to support new business opportunities arising from technological breakthroughs, including network slicing, which provides network functions to applications/users based on specific or operational needs. The complexity, agility, and transformation of the 5G ecosystem requires network service management to respond to new and sophisticated cyberattacks that are constantly evolving.
ETSI defines Zero-touch network and Service Management (ZSM) as a standard architectural framework for addressing 5G network management and security issues. The ZSM framework is envisioned as a next-generation management system with the goal of automating all operational processes and tasks such as planning and design, delivery, deployment, provisioning, monitoring and optimization, preferably without human intervention ("zero touch") .
Artificial intelligence, supported by machine learning and big data analytics, is a key factor in enhancing the ZSM framework and autonomous network capabilities, offering potential benefits for security improvements, enabling more effective and efficient security in cognitive network management Solutions that proactively perform predictive security capabilities in the expected network environment, even in 5G encrypted communications.
4. Final strategy choice
Based on the analysis conducted in this report, potential privacy and security risks, challenges, opportunities, and recommendations are identified and described, providing strategic options for this chapter. These include: feasibility of 5G technology application and privacy and security risks; effectiveness of 5G technology in terms of standardization (promoting privacy and security standards, and promoting ethical standards); integrity-driven 5G technology sustainability (strengthening legal and A regulatory framework that ensures trust and control post-5G, supports trustworthy investments by creating a common EU technology culture).
5. Conclusion
We are at another extremely challenging phase in the history of technological innovation, in which human values and technological knowledge seem to be increasingly intertwined, creating opportunities and risks not only for humans, but for the entire 5G ecosystem. The impact assessment conducted for this report identified six privacy and six security concerns related to 5G technology. For each of the concerns, there is neither technology inherently harmful nor contraindicated technological innovation. The same is true of 5G's impact on privacy and security, technology is not a means to an end, but a knowledge, and therefore depends on the robustness of security and the awareness and responsibility of the society in which it operates.