Still don't understand the routing policy? Disc it!


For IP network engineers, the deployment of routing policies can be seen everywhere, and the application of routing policies is very common no matter in the operator's IP network or in the enterprise network. At the same time, in network planning, routing strategy planning is also a core content. In order to facilitate everyone to better grasp and apply routing policies, we have launched the topic of routing policies. We hope that this topic can guide you to discuss and learn together.
An overview of routing strategies
1. What is a routing policy?
When discussing something, we generally cannot avoid the question: "What is XXX?" Here we also try to define a routing strategy to answer the question: "What is a routing strategy?"
Many people equate routing policy with route-policy, and some people may say that filter-policy also belongs to the category of routing policy. In fact, these understandings are a bit inaccurate. Actually, routing strategy is not a specific technology, nor is it a specific feature.
A routing strategy is a "strategy" that performs various controls on routing through a series of tools or methods. This strategy can affect route generation, advertisement, selection, etc., and then affect the forwarding path of packets. These tools include ACL, route-policy, ip-prefix, filter-policy, etc. These methods include filtering routes and setting attributes of routes.
2. The calling relationship between the tools of the routing strategy
When discussing routing policies, we often encounter many kinds of tools, such as ACL, route-policy, ip-prefix, filter-policy, etc., which are not listed one by one. Many people will be confused by the calling relationship between them, and always feel that there is an unclear relationship between them. Here we use a picture to introduce the relationship between them.

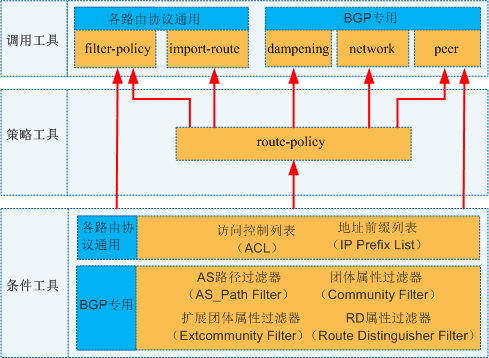
Figure 1 Calling relationship between tools of routing strategy
As shown in Figure 1, we divide all tools into three categories:
- Conditional tool: used to "grab" the required route.
- Policy tool: used to perform an action on the "fetched" route, such as allowing, denying, modifying attribute values, etc.
- Calling tool: used to apply the routing policy to a specific routing protocol to make it take effect.
The filter-policy and peer in the calling tool also have the function of the policy tool, so these two things can directly call the condition tool. All other invocation tools must indirectly invoke conditional tools through route-policy.
It should be noted that peers cannot call ACL, and can call all other conditional tools.
3. What is the use of routing policy?
In an IP network, the purpose of a routing policy mainly includes two aspects: 1) Filtering routing information. 2) Modify the properties of the route. See Table 1 for details:
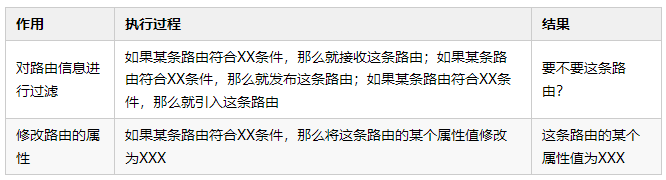
Table 1 The role of routing strategy
If you think that the role of introducing routing policies is still a bit abstract, it doesn't matter. Let's introduce another practical example and you will understand. Filter routing information by routing policy:

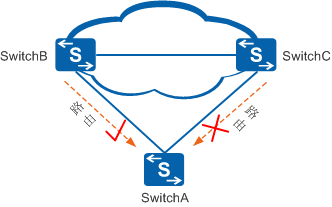
Figure 1 Filtering routing information through routing policies
As shown in Figure 1, SwitchA belongs to a dual-uplink networking structure, and SwitchA receives routes from SwitchB and SwitchC respectively. If SwitchA only wants to receive routes from SwitchB but not from SwitchC, what should I do? In this case, consider configuring a routing policy on SwitchA to allow routes from SwitchB and reject routes from SwitchC. routing. Modify the attributes of routes through routing policies

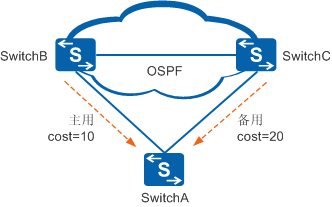
Figure 2 Modifying attributes of routes through routing policies
As shown in Figure 2, SwitchA also has a dual-uplink network structure. However, because the link on SwitchB is more stable and has a larger bandwidth, the user wants to use the link on SwitchB as the main link. The link on SwitchC serves as the backup link. When the active link fails, traffic is automatically switched to the backup link. In this scenario, a routing policy can be used to lower the routing cost from SwitchB and increase the routing cost from SwitchC, so that traffic will automatically select the link on SwitchB as the primary link. The link on SwitchC is used as the backup link to implement the primary backup of the route.
2. Routing Policy and Policy Routing
1. The difference between routing policy and policy routing
When I first came into contact with routing policies and policy routing, I was scratching my head, and I couldn't tell the difference. I always thought why the developers of the protocol gave them such confusing names. Wouldn't it be easy to confuse them if they changed a name! But since the name has been called for so many years, although you can't tell the difference, it's already familiar. Although the feature of policy routing is not the scope of discussion in this topic, we also make a comparative analysis of the twin brothers here, so that everyone will not be confused.
(1) Routing strategy
The operation object of the routing policy is routing information. Routing policy mainly implements functions such as route filtering and routing attribute setting. It changes the path that network traffic travels by changing routing attributes (including reachability).
(2) Policy routing
The operation object of policy-based routing is the data packet. When the routing table has been generated, it does not forward according to the routing table, but changes the forwarding path of the data packet according to a certain policy as needed.
Therefore, it can be seen that the policy routing works before the routing table. If the packet matches the policy routing, the packet will not be checked in the routing table, but will be forwarded directly according to the "guidelines" of the policy routing. . Therefore, policy routing is a "guy" who does not play cards according to the routine, and because of this, the application of policy routing will be more flexible.
2. Comparative Analysis of Routing Policy and Policy Routing
In order to compare routing policies and policy routing more specifically, we use Table 2 to make a comprehensive comparison between the two.
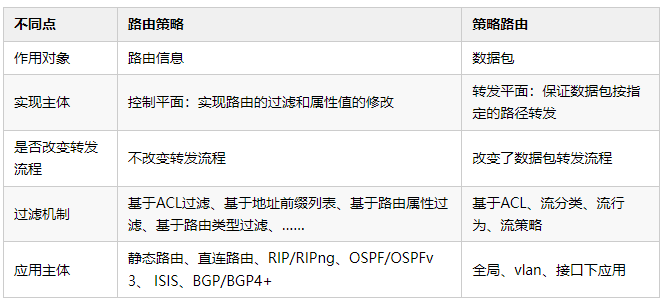
Table 2 Comparative analysis of routing policy and policy routing
3. A small test of routing strategy
The above has introduced some basic knowledge about routing policies from a macro level. Do you still feel that it is not enough? Do you still feel that the power of routing policies? It doesn't matter, let's take a look at the implementation of routing policies. The example of routing filtering is regarded as a small test. This example will involve concepts such as ACL, ip-prefix, route-policy, filter-policy, etc. We will introduce them in detail in the special topics in the following issues. You should first understand what routing policies can do. Don't study too much. Deep, so as not to go crazy!

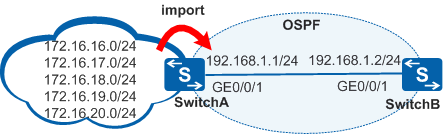
Figure 3 Example of implementing route filtering through routing policies
As shown in Figure 3, in the network running the OSPF protocol, SwitchA receives routes from the Internet network and provides Internet routes for the OSPF network. Now the user wants the OSPF network to only receive 172.16.16.0/24, 172.16.17.0/24 and 172.16. The three external routes of 18.0/24 are not accepted by other external routes.
The above user requirements can be achieved in a variety of ways. Next, we give two common implementation methods for your reference.
In the following experiment, we configure a black hole route in SwitchA as a test route, and import a static route into OSPF to simulate receiving routes from the Internet. The key configurations on SwitchA are as follows:
#
ospf 1
import-route static
area 0.0.0.0
network 192.168.1.0 0.0.0.255
#
ip route-static 172.16.16.0 255.255.255.0 NULL0
ip route-static 172.16.17.0 255.255.255.0 NULL0
ip route-static 172.16.18.0 255.255.255.0 NULL0
ip route-static 172.16.19.0 255.255.255.0 NULL0
ip route-static 172.16.20.0 255.255.255.0 NULL0
#
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
1. Implement route filtering through ACL+route-policy
(1) Define an ACL 2000 to match the route that needs to be released.
[SwitchA] acl 2000
[SwitchA-acl-basic-2000] rule 5 permit source 172.16.16.0 0
[SwitchA-acl-basic-2000] rule 10 permit source 172.16.17.0 0
[SwitchA-acl-basic-2000] rule 15 permit source 172.16.18.0 0
[SwitchA-acl-basic-2000] quit
- 1.
- 2.
- 3.
- 4.
- 5.
(2) Create a route-policy named RP, configure a node numbered 10, and call ACL2000.
[SwitchA] route-policy RP permit node 10
[SwitchA -route-policy] if-match acl 2000
- 1.
- 2.
(3) Call this route-policy when OSPF imports a static route
[SwitchA] ospf 1
[SwitchA-ospf-1] import-route static route-policy RP
[SwitchA-ospf-1] quit
- 1.
- 2.
- 3.
Because the route-policy defaults to deny nodes, the routes 172.16.19.0 and 172.16.20.0 are not imported into OSPF because they do not satisfy the if-match statement.
After configuring the above routing policy, the routing table of SwitchB is as follows:
[SwitchB]display ip routing-table
Route Flags: R - relay, D - download to fib
-----------------------------------------------------------------------------
Routing Tables: Public
Destinations : 7 Routes : 7
Destination/Mask Proto Pre Cost Flags NextHop Interface
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
172.16.16.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
172.16.17.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
172.16.18.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
192.168.1.0/24 Direct 0 0 D 192.168.1.2 Vlanif10
192.168.1.2/32 Direct 0 0 D 127.0.0.1 Vlanif10
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
It can be seen that after the routing policy is configured on SwitchA, there are only three external routes 172.16.16.0/24, 172.16.17.0/24 and 172.16.18.0/24 in the IP routing table of SwitchB, and there are no other external routes.
2. Implement route filtering through ip-prefix+filter-policy
(1) Define an address prefix list for matching routes that need to be released.
[SwitchA] ip ip-prefix huawei index 10 permit 172.16.16.0 24
[SwitchA] ip ip-prefix huawei index 20 permit 172.16.17.0 24
[SwitchA] ip ip-prefix huawei index 30 permit 172.16.18.0 24
- 1.
- 2.
- 3.
(2) In the OSPF view of SwitchA, use filter-policy to filter the advertised routes.
[SwitchA] ospf 1
[SwitchA -ospf-1] filter-policy ip-prefix huawei export
[SwitchA-ospf-1] quit
- 1.
- 2.
- 3.
Since ip-prefix implicitly implies deny nodes, the routes 172.16.19.0 and 172.16.20.0 are not within the range allowed by ip-prefix, so when SwitchA advertises routes to SwitchB, only those within the range allowed by ip-prefix are advertised. route, all other routes are not advertised.
After the above configuration is complete, the routing table of SwitchB is as follows:
[SwitchB] display ip routing-table
Route Flags: R - relay, D - download to fib
-----------------------------------------------------------------------------
Routing Tables: Public
Destinations : 7 Routes : 7
Destination/Mask Proto Pre Cost Flags NextHop Interface
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
172.16.16.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
172.16.17.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
172.16.18.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10
192.168.1.0/24 Direct 0 0 D 192.168.1.2 Vlanif10
192.168.1.2/32 Direct 0 0 D 127.0.0.1 Vlanif10
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- twenty one.
It can be seen that after the routing filter-policy is configured on SwitchA, there are only three external routes 172.16.16.0/24, 172.16.17.0/24 and 172.16.18.0/24 in the IP routing table of SwitchB, and there are no other external routes. .
From the experimental results, the tools and methods used by the above two methods are different, but the results are the same. I believe you have seen that routing policy cannot be directly equivalent to route-policy, right? In fact, routing policies are a series of means to control routing. The use of routing policies may be different combinations of multiple tools such as ACL, route-policy, ip-prefix, filter-policy, etc. The above examples only list them. Just two of the more common combinations.