Let's talk about WiFi6 security technology

1. Overview of WiFi6
In 2018, in order to better build a WiFi ecosystem, facilitate the publicity and use of WiFi standards, and help non-professional users to effectively distinguish WiFi standards, the WiFi Alliance changed the standard naming rules, renamed the previous standard 802.11n to WiFi 4, and the standard 802.11 ac was renamed WiFi5. In 2019, the Institute of Electrical and Electronics Engineers released the latest WiFi standard protocol 802.11ax, WiFi6. It can support both 2.4GHz and 5GHz frequency bands, and the maximum transmission rate is 9.6 Gbit/s. Compared with 802.11ac, the actual throughput in dense user environments is increased by 4 times, the nominal transmission rate is increased by 37%, and the delay is decreased by 75%. In early 2020, the WiFi Alliance announced that WiFi6 devices that can operate in the 6GHz band will be named WiFi6E. E stands for Extended, that is, the original frequency band is extended to the 6GHz frequency band. Figure 1 shows some of the indicator differences between the WiFi6 standard and the WiFi4 and WiFi5 standards.
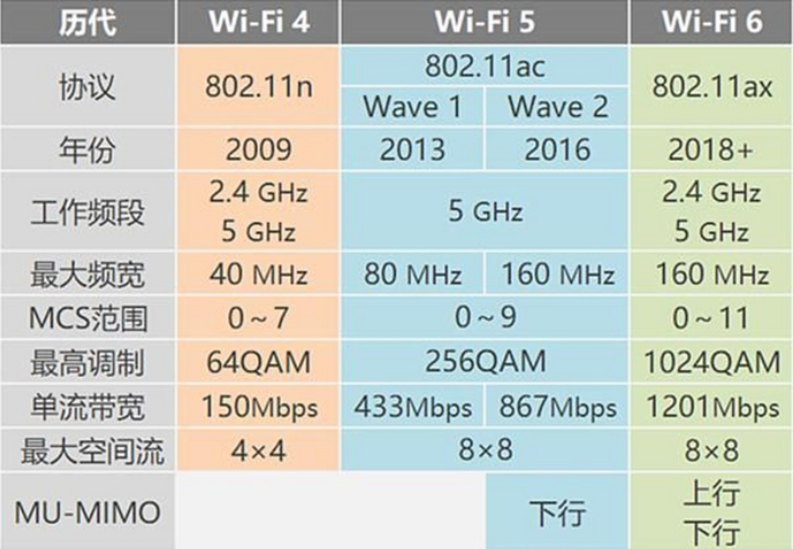
Figure 1. Some indicator differences between WiFi6 standard and WiFi4 and WiFi5 standards
The application scenarios of WiFi6 have also changed a lot compared with the previous version of WiFi. Typical WiFi6 application scenarios are listed as follows:
(1) Large-bandwidth video service bearer
With the continuous improvement of people's requirements for video experience, the bit rate of various video services is also increasing, from SD to HD, from 4K to 8K, and up to the current VR video. However, the requirements for transmission bandwidth are increasing day by day, and meeting the requirements for ultra-broadband video transmission has become a major challenge for video services. WiFi6 technology supports the coexistence of 2.4GHz and 5GHz frequency bands, of which the 5GHz frequency band supports 160MHz bandwidth and the rate can reach up to 9.6Gbit/s. The 5GHz frequency band has relatively less interference and is more suitable for transmitting video services. At the same time, BSS coloring mechanism, MIMO technology, dynamic CCA and other technologies can reduce interference, reduce packet loss rate, and bring better video experience to users.
(2) Bearing of low-latency services such as online games
Online game services are strongly interactive services, which have higher requirements on bandwidth and delay. Especially for emerging VR games, the best way to access it is through WiFi. The OFDMA channel slicing technology introduced by WiFi6 can provide dedicated channels for games, reduce latency, and meet gaming services, especially VR.
(3) Smart Home Smart Interconnection
Smart interconnection is an important part of smart home business scenarios such as smart home and smart security. The current home interconnection technology has different limitations, and WiFi6 technology will bring the opportunity of technological unification to smart home interconnection. It optimizes and integrates the characteristics of high density, large number of accesses, and low power consumption, and is compatible with various mobile terminals commonly used by users, providing good interoperability.
2. WiFi network security threats
Common WiFi threats in life mainly include the following categories:
(1) Illegal users occupy communication resources
When the password set by the WLAN is too simple, such as a pure digital password or even the default password, an attacker can obtain the password by guessing or brute force to access the network, occupying the bandwidth of legitimate users.
(2) Phishing attack
In the mobile cellular network, criminals take advantage of the defects of 2G technology to send spam information such as fraud and advertising to users' mobile phones through base stations disguised as operators. Similarly, in WLAN, criminals induce users to access by setting illegal hotspots with the same or similar Service Set Identifier (SSID) name as legal hotspots. Once a user accesses such a hotspot, important data may be stolen, resulting in loss of user property. For example, if a user accesses a shopping website pushed by an illegal WiFi hotspot and conducts a transaction, the criminals will intercept the user's account information and steal the user's account.
(3) Illegal AP access attack
At present, the attack methods of criminals are changing with each passing day, and the security attack and defense technology in the industry is also continuously expanding into the hardware field. The attacker may touch the WiFi access point device at the near end and tamper with the storage medium of the device. For the device without the hardware root of trust, the security protection measures of the entire system will be completely invalid. After an end user accesses a hijacked WiFi access point, all data traffic is stolen or tampered with. In addition, vulnerabilities inherent in older protocol standards, such as the Wired Equivalent Privacy (WEP) protocol's use of insecure algorithms and WeakIV vulnerabilities, also make passwords easy to crack.
To sum up, common security threats to WLAN include unauthorized use of network services, data security, unauthorized access points, and denial of service attacks. In response to the above security threats, we can take corresponding security measures to protect and protect network security. Below we mainly introduce the main security technologies involved in WiFi6.
3. WiFi6 security technology
Compared with WiFi5, WiFi6 improves the access bandwidth and concurrent capacity, and brings energy-saving technologies. Although the WiFi standard itself does not introduce new security mechanisms, the WPA3 certification mentioned above will become a standard from July 1, 2020. Compulsory certification of all new WiFi, namely WPA3 supporting WiFi6 to improve the security of wireless network. The WIFI6 security mechanism includes link authentication, user access authentication and data encryption, wireless attack detection and countermeasures, and the security and trustworthiness of the network element itself. Let's introduce them one by one:
(1) Link authentication
Link authentication is terminal authentication. Since the 802.11 protocol requires link authentication before accessing the WLAN, link authentication is generally considered to be the starting point of the handshake process for a terminal to connect to an AP (Access Point, AP) and access the WLAN. The 802.11 protocol specifies that there are two main types of link authentication methods: Open System Authentication and Shared-key Authentication. In the open system authentication, the terminal uses the ID (usually the MAC address) as the identity proof, and all the terminals conforming to the 802.11 standard can access the WLAN. The shared key authentication is only supported by the WEP protocol, which requires the terminal and the AP to use the same "shared" key. Since the WEP protocol has poor security and has been eliminated, open system authentication is generally used in the link authentication stage. This stage does not actually perform the identity authentication process, as long as it conforms to the protocol interaction process, the link authentication can be passed. In the WPA3 standard, Opportunistic Wireless Encryption (OWE) is newly introduced, which protects the privacy of users in the open network through separate data encryption, and realizes the non-authenticated encryption of the open network.
(2) User access authentication and data encryption
User access authentication distinguishes users and restricts their access rights before they can access the network. Mutually
For a simple terminal authentication mechanism (link authentication), user authentication is more secure. User access authentication mainly includes the following types: WPA/WPA2/WPA3 authentication, 802.1x authentication, and WAPI authentication. In addition to user access authentication, data packets need to be encrypted to ensure data security. After the data packet is encrypted, only the specific device with the key can decrypt the received packet. Even if other devices receive the packet, they cannot decrypt the data packet because they do not have the corresponding key. Figure 2 shows the two-way verification process of the device certificate:
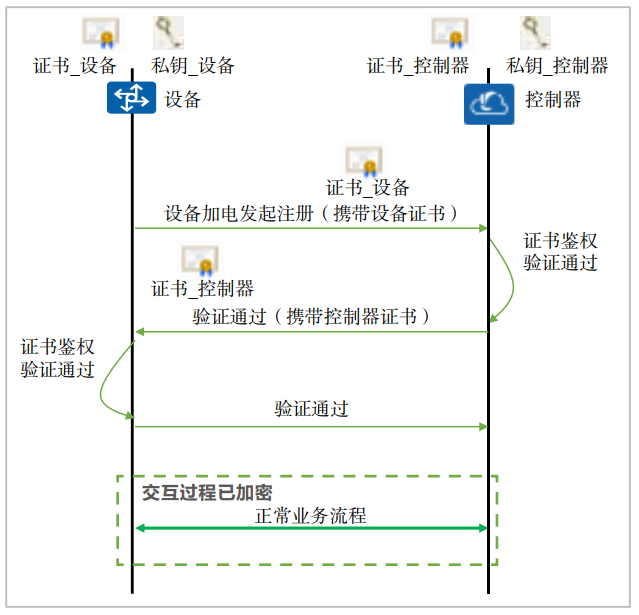
Figure 2. Device certificate two-way verification process
In order to build end-to-end security and trustworthiness, in addition to ensuring the security of the channel from the terminal to the WLAN device AP, the AP to the controller also needs to ensure the device trustworthiness and channel security.
As shown in Figure 2, the device certificate two-way verification process, the device to be registered carries the device's own certificate to the cloud platform in the message that initiates the request; after the cloud platform obtains the device certificate, it performs the traversal authentication of the certificate chain and verifies the device at the same time. Whether the ESN is injected into the device in the resource pool; the corresponding device will also verify the certificate of the cloud platform. Only after the two-way verification is passed, the business process can be initiated, and the risk of device counterfeiting can be prevented through the security mechanism of the certificate. Two-way authentication between Wi-Fi device and controller
It needs to be implemented based on digital certificates. The most critical part of the authentication process is the signature of the private key. If an attacker can break through the host software and call the authentication private key, he can imitate a legitimate device and deceive the controller to access the network, thereby realizing a lateral attack.
(3) Wireless attack detection and countermeasures
The two methods of authentication and encryption are commonly used wireless security solutions at present, which can protect the network in different scenarios. On this basis, the protection function of WLAN can also be provided through wireless system protection. At present, the main technologies of wireless system protection include wireless intrusion detection system (Wireless Intrusion Detection System, WIDS) and wireless intrusion prevention system (Wireless Intrusion Prevention System, WIPS). These two technologies can not only provide intrusion detection, but also implement some intrusion countermeasures to protect the network more proactively. For the most common key brute force cracking, the anti-brute force key function can be deployed. The AP will detect the number of negotiation failures in key negotiation packets during authentication within a certain period of time. If it exceeds the configured threshold, it is considered that the user is cracking the password through brute force cracking. At this time, the AP will report an alarm message to the AC. If the dynamic blacklist function is enabled at the same time, the AP will add the user to the dynamic blacklist. , discard all packets of this user until the dynamic blacklist ages.
(4) Equipment integrity protection
The goal of secure boot is to protect the integrity of software installation packages and ensure that the integrity verification process is safe and reliable. The software installation package may be maliciously tampered with by the attacker during the transmission process. Once the maliciously tampered software is installed on the user system, user information may be leaked, user system resources may be occupied, or the system may even be completely controlled by the attacker. If the software of enterprise equipment is tampered with and implanted with eavesdropping function, it will bring huge losses to operators and enterprises.
The security guarantee of this part is mainly based on the hardware root of trust and the secure boot of the digital signature. The principle of the scheme is as follows: the system must have a piece of unchangeable code and a signature verification key as the Root of Trust (RoT), and as the first piece of code to start the system. When the system is started, each start-up stage checks the code for the next stage start-up step by step. If the check fails, the start-up is stopped.
4. Summary
In the long run, the increase in the access of IoT devices is the main reason for the surge in network traffic, so the constant update of the protocol is also to meet people's multi-device and multi-scenario Internet access needs in the future. Although the technology is constantly updated, attackers still frequently invade IoT devices through protocols, and users still need to be vigilant when using public WiFi. Although WiFi6 is rapidly gaining popularity, there are still deficiencies, such as few supporting devices and high cost, and the advantages can only be highlighted in specific occasions. It is the general trend that WiFi6 will enter people's lives. In the future, more and more bearer devices will be launched, and security risks will also arise. People not only need to enjoy the benefits of technology, but also actively respond to the risks and challenges brought by technology.
references
[1] Cao Bin, Jixiang. Research on the application of Wi-Fi6 security and trusted technology [J]. Secrecy Science and Technology, 2020(08): 20-28.
[2] Huang Yu, Li Yuru. Overview of WiFi6 Technology Status [J]. China Radio, 2021(05):90-91.
[3] Wang Yicheng. Analysis of the sixth generation WiFi technology and its relationship with 5G [J]. Information and Communication, 2020(05): 1-3.
[4] Mathy Vanhoef , Eyal Ronen. Dragonblood. Analyzing the Dragonfly Handshake of WPA3and EAP-pwd.
[5] https://en.wikipedia.org/wiki/IEEE_802.11ax[6] https://www.freebuf.com/articles/wireless/242734.html